
TECHNICAL VALIDATION
How to Deliver Successful AI Projects by Reducing Risk and Boosting Performance
Google Cloud Security Ecosystem—Exabeam
How to Deliver Successful AI Projects by Reducing Risk and Boosting Performance
Leveraging the Google Platform to Accelerate the
Delivery of Differentiated Security Offerings
By Tony Palmer, Practice Director and Principal Analyst, Validation Services
Enterprise Strategy Group
December 2023
Introduction
Background
Figure 1. Cloud-first Policy for New Applications on the Rise

The Google Cloud Security Ecosystem
Google Cloud is designed, built, and operated with security as a primary design principle to help protect its customers against threats in their environments. Google layers on security controls to enable organizations to meet their own policy, regulatory, and business objectives. Customers can leverage elements of Google’s compliance framework in their own compliance programs.
Google Cloud secures more than three billion users globally. To accomplish that, Google’s cloud infrastructure can’t rely on any single technology to make it secure. Google’s stack builds security through progressive layers designed to deliver true defense in depth, and at scale.
Figure 2. Google Cloud Security Ecosystem Overview
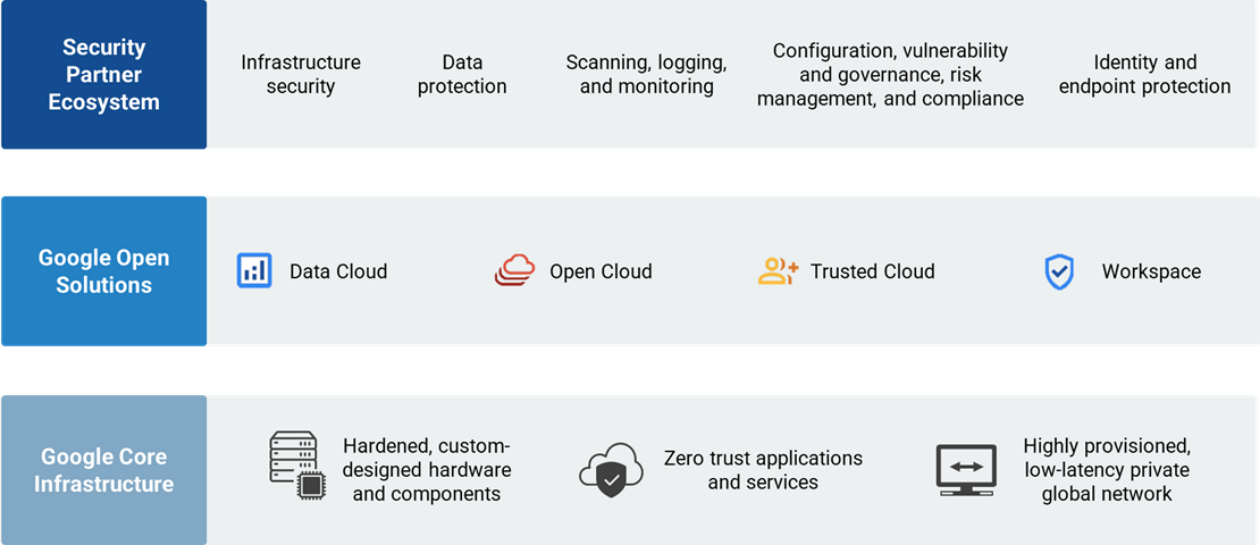
Source: Enterprise Strategy Group, a division of TechTarget, Inc.
Google Workspace

Enterprise Strategy Group Technical Validation
Exabeam: Digital Transformation
Figure 3. The Exabeam Security Operations Platform
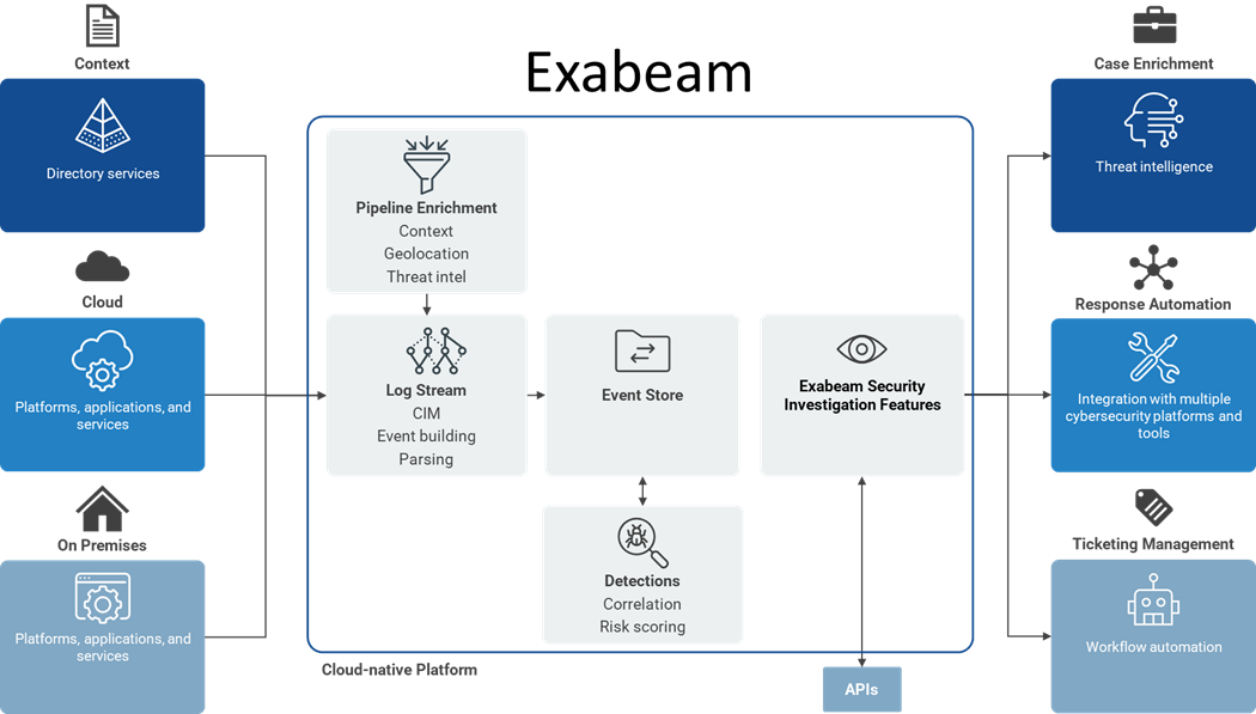
Source: Exabeam and Enterprise Strategy Group, a division of TechTarget, Inc.
Figure 4. Google Stack Impact
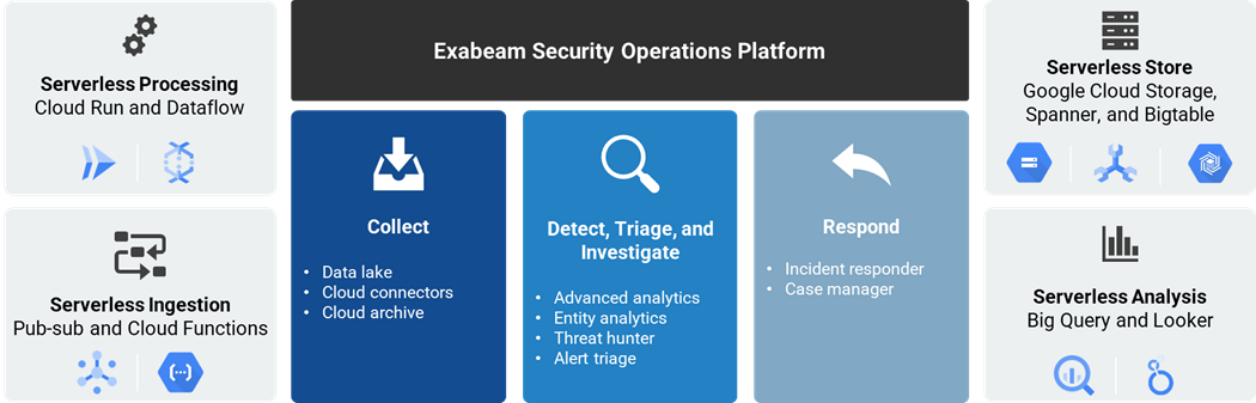
Source: Google and Enterprise Strategy Group, a division of TechTarget, Inc.

Why This Matters
Companies continue to embrace the cloud to create and deploy business applications. According to Enterprise Strategy Group research, 46% of organizations surveyed indicated that they have a cloud-first policy for deploying new applications. This has led to a change in how organizations build applications that Exabeam has experienced first-hand.
Google Cloud provided Exabeam with a secure, highly scalable platform on which to develop and deploy its cloud-native SecOps offering, reaping numerous business benefits from the partnership. An Exabeam executive told Enterprise Strategy Group: “Google ... makes it so much easier for us to deal with our own challenges without having to worry about the back end.”
Running in Google Cloud means that Exabeam uses Google Cloud’s infrastructure and first-party tools to create and deliver differentiated products and offerings to their customers at scale and with performance that was impossible with their on-premises infrastructure.
Conclusion
This Enterprise Strategy Group Technical Validation was commissioned by Google and is distributed under license from TechTarget, Inc.
©TechTarget, Inc. or its subsidiaries. All rights reserved. TechTarget, and the TechTarget logo, are trademarks or registered trademarks of TechTarget, Inc. and are registered in jurisdictions worldwide. Other product and service names and logos, including for BrightTALK, Xtelligent, and the Enterprise Strategy Group might be trademarks of TechTarget or its subsidiaries. All other trademarks, logos and brand names are the property of their respective owners.
Information contained in this publication has been obtained by sources TechTarget considers to be reliable but is not warranted by TechTarget. This publication may contain opinions of TechTarget, which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.
About Enterprise Strategy Group
TechTarget’s Enterprise Strategy Group provides focused and actionable market intelligence, demand-side research, analyst advisory services, GTM strategy guidance, solution validations, and custom content supporting enterprise technology buying and selling.
