Your Organization’s Customized Zero Trust Segmentation Report
Assessment and benchmark
research powered by ESG
Your Organization’s Data-First Leader Report
Assessment and benchmark
research powered by ESG

Introduction
Thank you for taking Illumio’s Zero Trust Segmentation assessment. The goal of this assessment is to give you data driven insights about your organization’s progress toward achieving Zero Trust Segmentation, complete with recommendations specific to your current state.
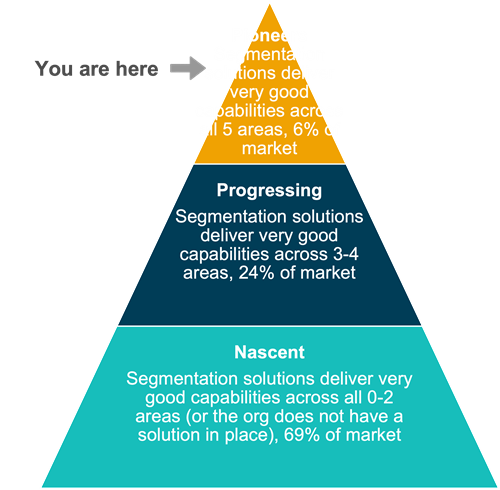
To power this assessment, we partnered with ESG to survey 1,000 of your peers across the globe. Based on this benchmark dataset, we identified 5 critical aspects of technologies needed to become a Pioneer on Zero Trust Segmentation. And the research validated that organizations with segmentation technologies that deliver these key capabilities enjoy dramatically improved security outcomes.
Below you will see how your organization compares to the market in general, as well as surveyed Pioneers on key questions. By working to close the gaps you see, your organization will move up the maturity curve so you can gain better visibility to network activity and traffic patterns in your environment, segment and protect your organization’s mission-critical digital assets, and limit the scope of inevitable security incidents to respond faster and keep incidents from becoming cyber disasters.
Your Zero Trust Segmentation Progress
Based on your responses your organization is
PIONEERING
ESG’s research shows that Leaders outperform their peers in a number of ways:
Leaders more successfully advance zero trust; they are:


Leaders’ applications are more resilient; they are:



Leaders achieve more comprehensive visibility across their environments; they are:

What Data-first Leaders Achieve
Understanding the Zero Trust trend
Where you stand: 99% of respondents we surveyed are at least interested in Zero Trust as a broad concept, though just 36% have implemented or begun to implement Zero Trust across their entire IT footprint. This tells us two things:
- Zero trust represents a major change that has captured significant mind share among cybersecurity strategists.
- While the concepts of Zero Trust have a lot of resonance with security practitioners, we are still in the early days of implementation.
Organizations are investing heavily to make Zero Trust a reality
Weighing the tradeoffs between ease of use and functionality
How do segmentation technologies fit into the Zero Trust puzzle?
Breadth of segmentation
Depth of segmentation capabilities
Why it matters: Breadth of segmentation is one aspect of achieving Zero Trust Segmentation. But just as important are the capabilities of your organization’s segmentation solutions.
- At its heart Zero Trust Segmentation should strive to give the organizations key capabilities:
- Visibility – you can’t protect what you can’t see, and today’s IT environments are a complex mix of cloud-hosted, on-premises-resident, microservices-based, and monolithic workloads. You need visibility into the network patterns in all cases to achieve Zero Trust Segmentation
- Containment – when attacks happen, and they will, the ability to pivot quickly to response and prevent attackers from moving laterally and infecting additional systems is critical. This requires integrations with SIEM and SOAR tools to plug into existing workflows, as well as technology guardrails (like port blocking) that can block this movement.
- Environmental separation – A critical in moving from reactive to proactive is ensuring that unrelated environments are separated (such as development from production)
To measure and organizations’ ability to deliver on the promise of Zero Trust Segmentation, this assessment looks at several key capabilities:
- Integration with SIEM and SOAR tools: Teams rely on their SIEM and SOAR tools for insights from across their entire security posture. To make insights from segmentation tools like where attempted attacks are in progress, what machines are acting suspiciously, and if your segmentation is secure, tight integration is critical.
- Separation of test and dev from production environments: Enforcing a boundary between development and production environments helps secure your mission-critical production data. However, development environments often leverage production systems for management and essential data center services. The solution is to ensure an enforcement boundary is present and to add policy-based exceptions based on the topology of network communications.
- The ability to block ports to stop the spread of attacks: Serious malware and ransomware attacks typically follow a similar pattern. Generally, the attacker is not able to gain direct access to “crown jewel” databases and applications. Rather, the attacker gains a foothold on an unprotected system, generally something of low business value. The attacker then moves to a more high-value target before launching the attack. By properly segmenting applications, organizations can stop this behavior.
- Consistent enforcement across cloud and data center environments: Today’s IT infrastructure environments are complex, being comprised of bare-metal servers, VMs, and containers running in a variety of locations from the core data center, the edge, and in a variety of CSPs. To secure the environment effectively and efficiently, organizations need controls that can span those many environments and infrastructure types and do so in a consistent manner. Consistent enforcement across different application architectures: Similarly, organizations’ application portfolios are varied from microservices-based cloud-native applications to legacy monolithically architected applications. Again, consistency and completeness of coverage are key to maximizing security effectiveness.
Decision point: dedicated microsegmentation tools versus features in a platform
Who your organization purchases security controls from
The Bigger Truth
We hope this assessment, and the research that underpins it, has helped you better understand the state of the market with respect to cloud-native security maturity and your organization’s progress towards becoming a leader. As a cohort, leaders have identified the key security capabilities to embed into their cloud-native development processes:
- It is increasingly business-critical: Today, 11% of respondents tell us most/all of their cloud-native applications are business-critical. Looking ahead 12 months, 40% of respondents expect the same proportion to be business-critical.
- It is more effective: Despite the fact that leaders have a much broader attack surface (managing 3.7x as many cloud-native applications in production), they suffer from 31% fewer security incidents. Leaders have found a better, and more scalable, way to secure their environments.
- It enables what developers care about, agility: Leaders, while being better protected, have also driven greater speed into their development environments and are 2.6x more likely than less mature organizations to push code to production environments multiple times per day.