
WHITE PAPER
How to Deliver Successful AI Projects by Reducing Risk and Boosting Performance
Pathways To A Zero
Trust Branch
Delivering Accelerated and Secure Connectivity
With the Power of SD-WAN and SASE
How to Deliver Successful AI Projects by Reducing Risk and Boosting Performance
By Jim Frey, Principal Analyst
Enterprise Strategy Group
January 2025
Introduction
Branch connectivity might seem straightforward, when considering the basic needs of extending WAN connectivity and providing secure access, but trying to do so at scale and in the face of mixed, dynamic application and threat environments is anything but simple. The pace of change in applications and the ever-growing nature of the threat landscape demand careful consideration and accommodation.
From a security perspective, Zero Trust strategies are becoming a focal point for helping to align and tune efforts to protect branches and the enterprises of which they are part. Zero Trust is not the only dimension of a branch security strategy, but it has become an essential pillar.
From an operational performance perspective, branch security must be balanced with network optimizations that can improve and ensure user experience and, by doing so, improve productivity and customer satisfaction. This requires network acceleration and traffic management that can adapt to a mix of cloud, SaaS, and business applications and that can intelligently accommodate specific work activities and behaviors with those applications.
Done successfully, organizations can realize the benefits of a Zero Trust Branch, addressing the combined networking and security needs within a single, integrated branch connectivity solution. Palo Alto Networks has this exact Zero Trust Branch end goal in mind when bringing the best of networking and security technologies together, binding advanced software-defined WAN (SD-WAN) functionality with cloud-based secure access service edge (SASE) that includes Zero Trust capabilities, delivered as Prisma SASE®.
Applying Zero Trust to the Branch
Key Objectives for Branch Connectivity
Design and deployment of branch network connectivity provides both a platform and an opportunity to employ Zero Trust strategies, but it must be done in way that accommodates the broader context of essential operational goals and constraints. The overall business purpose of branch connectivity is to deliver reliable and efficient access to remotely hosted resources, such as cloud and SaaS-based data and applications. This can be decomposed further into a few key objectives:

Understanding Zero Trust
Figure 1. Top Reasons for Considering or Adopting a Zero Trust Strategy
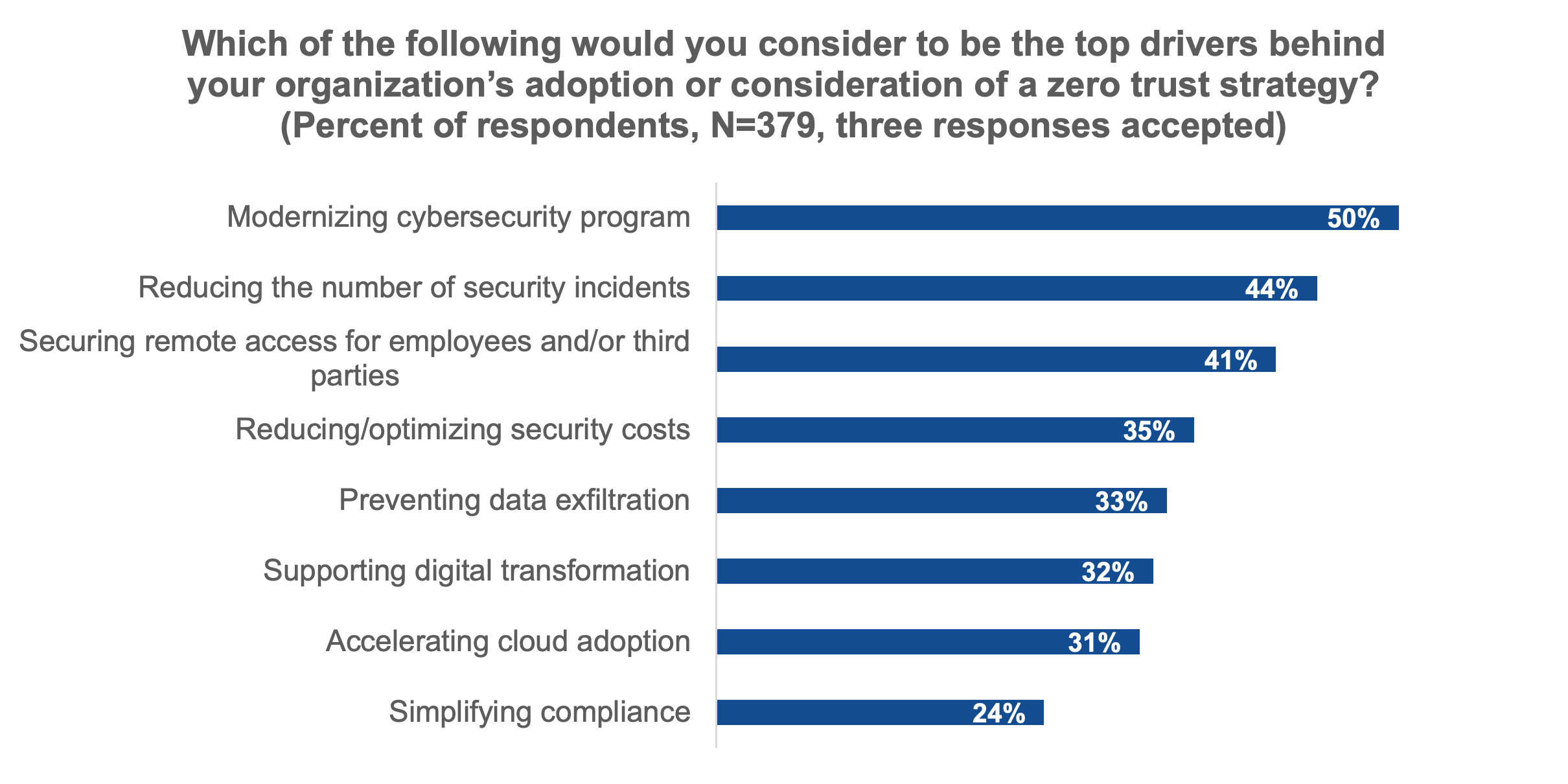
Figure 2. Most Effective Tools and Technologies for Achieving Zero Trust Objectives


SD-WAN Role in a Zero Trust Branch
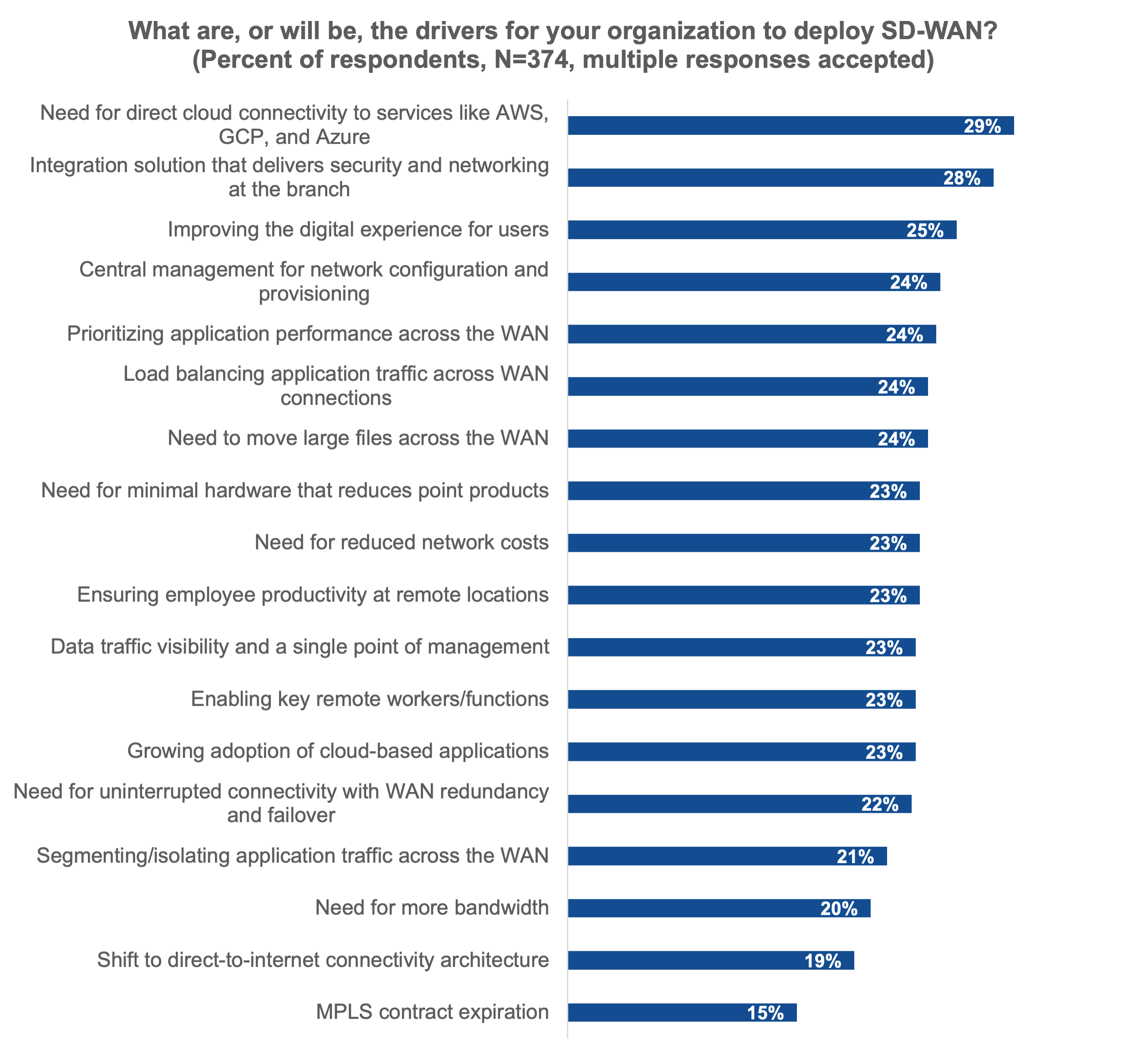
Figure 3. Drivers for Deploying SD-WAN
SASE for a Zero Trust Branch
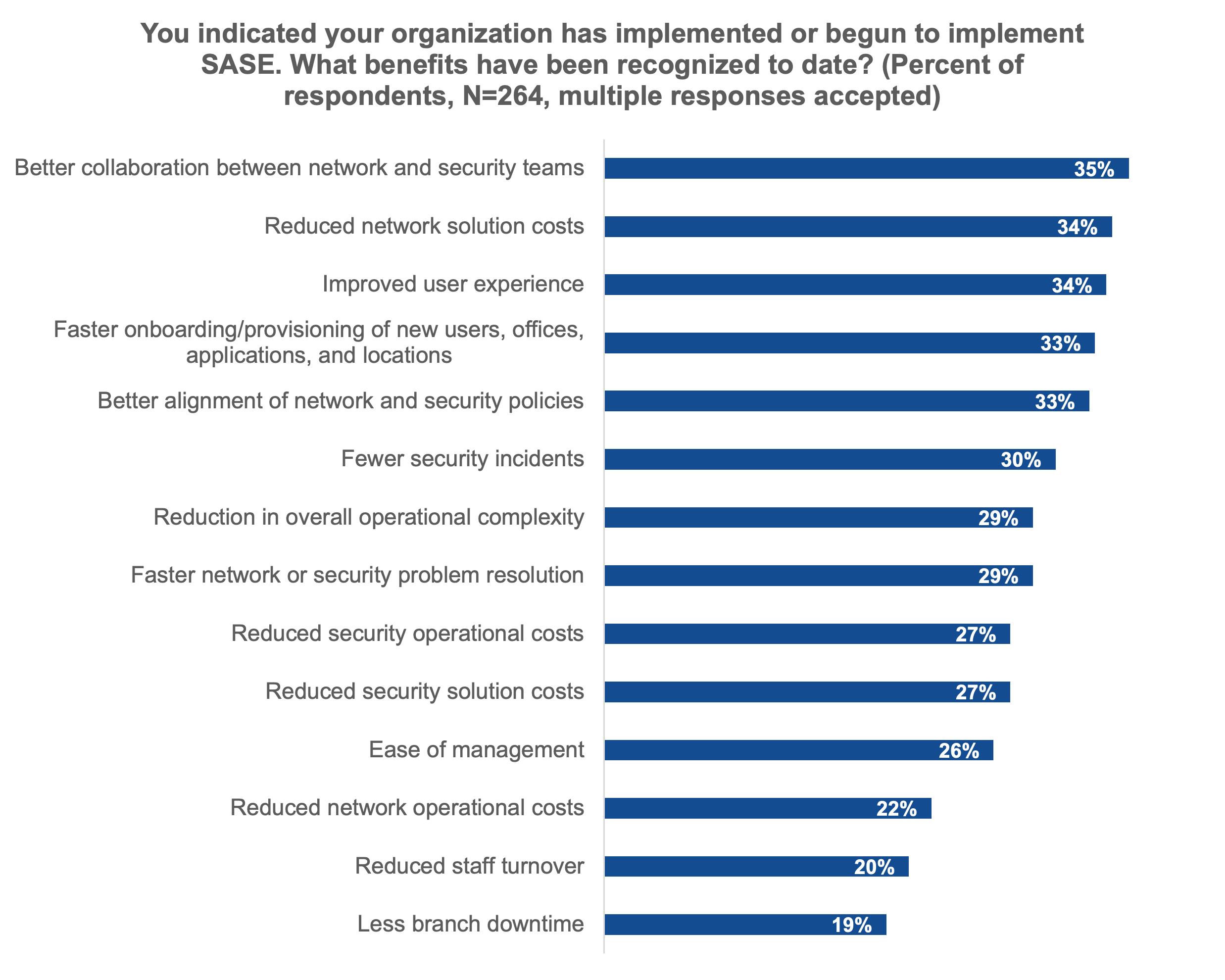
Figure 4. Benefits Experienced by Deploying SASE
An Ideal Approach: Tightly Integrated SD-WAN Plus SASE
The Palo Alto Networks Approach for a Zero Trust Branch
Conclusion
This Enterprise Strategy Group White Paper was commissioned by Palo Alto Networks and is distributed under license from TechTarget, Inc.
©TechTarget, Inc. or its subsidiaries. All rights reserved. TechTarget, and the TechTarget logo, are trademarks or registered trademarks of TechTarget, Inc. and are registered in jurisdictions worldwide. Other product and service names and logos, including for BrightTALK, Xtelligent, and the Enterprise Strategy Group might be trademarks of TechTarget or its subsidiaries. All other trademarks, logos and brand names are the property of their respective owners.
Information contained in this publication has been obtained by sources TechTarget considers to be reliable but is not warranted by TechTarget. This publication may contain opinions of TechTarget, which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.
About Enterprise Strategy Group
TechTarget’s Enterprise Strategy Group provides focused and actionable market intelligence, demand-side research, analyst advisory services, GTM strategy guidance, solution validations, and custom content supporting enterprise technology buying and selling.
www.esg-global.com | contact@esg-global.com