
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG WHITE PAPER
The Case for Open XDR
By Jon Oltsik, ESG Senior Principal Analyst and Fellow
DECEMBER 2020
EXECUTIVE SUMMARY
Security operations focus an organization’s efforts around threat prevention, detection, and response. This then depends upon effective data collection, processing, and analysis, followed by data-driven decision making.
While organizations have years of experience in these areas, security operations processes and technologies seem to be less and less effective, increasing cyber-risk and the prospect of a costly data breach. CISOs can’t keep doing things the same old way but rather need different types of solutions to overcome the inefficiency and ineffectiveness of today’s security operations. This report concludes:
Disconnected point tools create security operations challenges. ESG research indicates that many firms anchor their security operations with an assortment of disconnected point tools, making it difficult to assess security status, detect cyber-attacks, or respond to incidents in a timely manner. These challenges also introduce lots of operational overhead as the security staff must deploy, configure, and operate each security tool.
Organizations are moving toward a tightly coupled security operations infrastructure. Proactive CISOs are moving beyond security point tools toward a security operations and analytics platform architecture (SOAPA). SOAPA is designed to address many technology issues by providing an integrated technology stack for data management, messaging, analysis, and security operations.
XDR may fill the SOAPA role. Recognizing the need for SOAPA, technology vendors are now promoting eXtended detection and response (XDR) tools—integrated platforms of security products spanning hybrid IT architectures, designed to interoperate and coordinate on threat prevention, detection, and response. In this way, XDR can unify control points, security telemetry, analytics, and operations into one enterprise system. Thus, XDR can be seen as a technology platform emulating the SOAPA design.
Enterprise organizations need open XDR. Despite the promise of XDR, many organizations remain reluctant to move forward as they don’t want to embark on costly and complex projects that involve replacing existing security controls and analytics solutions. Open XDR alleviates these issues by acting as an overlay that sits on top of the existing security infrastructure. Open XDR can synthesize the alerts from multiple security controls, act as a common workbench for security operations, monitor/measure security efficacy, and take automated actions for incident response and risk mitigation. Some open XDR systems also provide services for continuous testing and controls validation, creating a closed loop for threat prevention, detection, and risk mitigation.
THE STATE OF CYBERSECURITY OPERATIONS
According to ESG research, 63% of organizations believed that security operations has grown increasingly difficult as compared to two years ago.1 This belief is based on several factors (see Figure 1):
Increasingly sophisticated threat landscape. Organizations are under attack by an assortment of cyber-criminals, hacktivists, and nation states that use social engineering techniques like spearphishing to compromise systems, move laterally across their networks, create privileged accounts, and steal valuable data. Many organizations find it difficult to monitor cyber-threats; correlate cyber-threat intelligence (CTI) with internal security telemetry; or keep up with the tactics, techniques, and procedures (TTPs) used by cyber-adversaries.
Volume and variety of security data. Aside from threat intelligence, organizations rely upon a variety of other security data sources like system logs, NetFlow/IPFIX data from networks, endpoint telemetry from EDR systems, proxy logs, cloud logs, DNS logs, etc. Collecting, processing, and analyzing volumes of security data can require a highly scalable data pipeline for analyzing real-time and batch data. Unfortunately, many organizations don’t have data pipelining expertise within their security departments, leading to difficulties staying ahead of massive volumes of security telemetry.
Overwhelming amount of security alerts. Over many years, organizations have added multiple security analytics tools as countermeasures for different types of threats. Each individual security system is programmed to issue alerts when it detects anomalous, suspicious, or malicious behavior, often leading to thousands of alerts per day. Given this volume, many security operations teams are overwhelmed as they attempt to triage, prioritize, and investigate alerts that could indicate a damaging cyber-attack in progress.
Figure 1. Reasons Why Security Analytics and Operations Have Become More Difficult
You indicated that cybersecurity analytics and operations is more difficult today than it was 2 years ago. What are the primary reasons why you believe this to be true? (Percent of respondents, N=256, three responses accepted)
Source: Enterprise Strategy Group
Growing attack surface. Organizations are regularly moving workloads to public cloud infrastructure, embracing SaaS applications, and deploying IoT devices as part of digital transformation initiatives. To defend against attacks, security teams must be able to discover, monitor, and protect all assets as they connect and disconnect to and from the network. This can be a daunting task as the attack surface grows unabated—especially as it extends to public clouds outside of traditional corporate data centers.
As the research indicates, security analytics and operations are also impacted by a reliance on manual processes (26%) and a shortage of staff and skills (21%). Manual process issues are often exacerbated because many organizations rely on numerous disconnected point tools for security operations, and each of these tools demands its own administration and produces its own reporting. This means security analytics and operations depend upon the security operation center (SOC) team piecing everything together to get a full picture. Finally, the combination of manual processes, a reliance on point tools, and the staff and skills shortage likely contributes to the 29% of organizations that claim that it is difficult to keep up with the operational needs of security analytics and operations technologies.
ON TO SOAPA
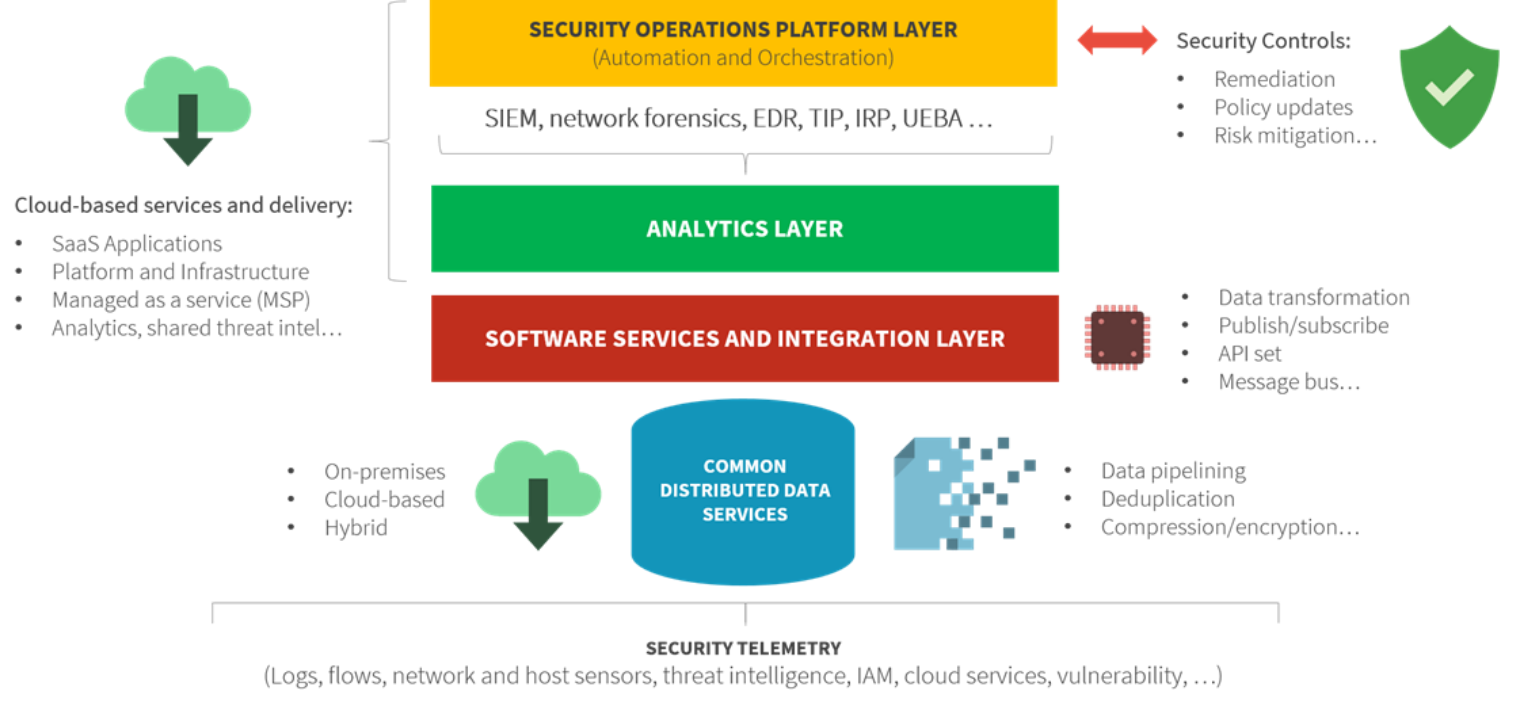
Addressing security analytics and operations issues will require a different security operations technology architecture—one built for scale, integration, advanced analytics, and process automation. This fits in with ESG’s SOAPA concept (see Figure 2). SOAPA is a bottom-up architecture featuring a:
Common distributed data service. SOAPA creates a common data pipeline for batch and streaming data and a flexible schema for any and all security analytics engines. In this way, SOAPA can collect, process, analyze, and act upon a massive ever-changing data repository.
Software services and integration layer. This layer serves as a bridge between security data and analytics engines that consume the data. The software services and integration layer makes all security data available to analytics engines when they want it and in the format they want it.
Analytics layer. The SOAPA analytics layer is designed for efficient monitoring and analysis of all security data (i.e., cloud data, network data, endpoint data, log files, threat intelligence, etc.). Modern SOAPA systems will build analytics across all telemetry for detection of sophisticated cyber-attacks across an extended kill chain.
Security operations platform layer. SOC analysts will spend most of their time in the security operations layer. This top layer of the SOAPA stack is programmable and can be instrumented to take automated actions like gathering data for an investigation, blocking a network connection, or opening a ticket in a case management system. Security remediation operations can also be orchestrated to take actions across multiple security controls like firewalls, network proxies, web, or DNS gateways, etc.
Figure 2. SOAPA
Introducing eXtended Detection and Response (XDR)
Large organizations have spent the last several years on SOAPA projects with the intent of integrating security operations point tools into a more holistic and comprehensive architecture. These initiatives often required programming, customization, and the integration of open source tools like the Apache Kafka messaging bus or ELK stack (i.e., Elastic, Logstash, Kibana). Unfortunately, this relegated SOAPA to a small subset of organizations that had the advanced skills and resources necessary.
Recognizing the need to simplify SOAPA, numerous technology vendors have introduced a new technology in 2020 called XDR. ESG defines XDR as:
An integrated suite of security products spanning hybrid IT architectures, designed to interoperate and coordinate on threat prevention, detection, and response. XDR unifies control points, security telemetry, analytics, and operations into one enterprise system (i.e., SOAPA).
XDR exemplifies the old adage, “The whole is greater than the sum of its parts,” by consolidating data telemetry, centralizing management (i.e., configuration management, policy management, allowing/denying, etc.), unifying analytics, and providing process automation capabilities for incident response (IR) and risk mitigation. XDR can also make these connections across the extended enterprise—remote systems, data centers, IoT devices, cloud-based workloads, etc. In this way, XDR provides end-to-end visibility for threat detection. This is critical for detecting “low and slow” attacks as they move laterally over networks through the cyber-attack kill chain. XDR provides the ability to detect discrete threats and then map their progression through a timeline of events. This should greatly improve threat detection accuracy, reduce security alert volume, and provide analysts with the right evidence and artifacts for more thorough investigations.
With built-in integration and central management, XDR could help a majority of enterprise organizations move from disconnected point tools to SOAPA for security analytics and operations.
XDR Challenges
XDR is in a genesis phase today, but it is progressing rapidly and will likely be a major focus for enterprise security organizations and the technology industry in 2021. While the potential benefits of XDR are attractive, XDR solutions may create other difficulties, especially for large distributed organizations. Why? Some XDR offerings are anchored to a vendor’s security controls like EDR, NDR, email security, cloud security, etc. To achieve XDR benefits, organizations would therefore have to replace their existing heterogeneous security controls with those from a single vendor. This may not be a problem for smaller organizations, but large enterprises may find this challenging because:
Different controls have different owners and budgets. To support disparate point tools, many CISOs carved up their security budgets and organizations into atomic units, focused on different areas like endpoint security, network security, etc. Often, these sub-groups extend beyond security to include IT operations. A single vendor’s XDR can only succeed if it breaks down these existing walls, unifies teams, and consolidates budgets. This may be possible, but large global firms will likely need time to change their organizational structures, select an XDR vendor, and deploy new controls across the enterprise. A lengthy transition negates any near-term benefits from XDR.
Security teams may have advanced skills and tight relationships with existing vendors. Endpoint, network, email, and cloud security specialists may have years of experience working with specific tools and vendors. It may be difficult to convince these specialists that their expertise can be usurped by burgeoning technologies like XDR.
In addition to these issues, many security teams already consider their SIEM as a security consolidation platform, so an XDR strategy must be designed with SIEM integration as part of the plan. The goal here is to harmonize the interaction between security operations silos and the SIEM, not burn everything to the ground and start over.
Open XDR Can Act as a Vendor-Agnostic Integration Hub
According to ESG research, 36% of organizations said that integrating disparate security analytics and operations tools was one of their highest priorities, while another 48% were somewhat active in a project to integrate disparate security analytics and operations tools. This data seems to indicate that organizations are headed toward SOAPA. XDR could help SOC teams get there, but CISOs simply can’t fathom the cost and complexity associated with swapping out the security controls they’ve counted on for years.
ESG believes that XDR doesn’t have to be a Faustian compromise. There’s an alternative strategy, made possible with an open XDR strategy. Rather than replace independent controls, open XDR acts as an abstraction layer above existing controls. In other words, open XDR becomes an integration hub for security analytics and operations as a “manager of managers,” integrating with SIEM, EDR, NDR, public clouds, and individual point tools. In this role, open XDR:
Synthesizes alerts from current controls. Open XDR uses advanced analytics to piece together individual security alerts, uncover real cyber-attacks, piece together the entire attack kill chain, and then provide high-fidelity comprehensive alerts to the SOC team. Applying detection content across tools unifies alerts and investigation-related artifacts abstracting out duplicate alerts and false positives. Armed with kill chain details, open XDR can map alerts to the MITRE ATT&CK framework, helping analysts contextualize attack progress and pinpoint the right remediation actions. .
Acts as a workbench for SOC analysts. SOC analysts often complain about “swivel chair” management as they pivot from tool to tool to detect and respond to security incidents. Open XDR can help alleviate this inefficient process by acting as a centralized workbench for SOC activities like security investigations, security control fine-tuning, threat hunting, etc. This alone should help organizations improve SOC output and productivity.
Monitors and measures security performance. Security programs are complex and multi-faceted, so CISOs need the right visibility and reports to measure where they need to focus their attention. By sitting above existing controls, open XDR can measure which ones are consistently detecting the tactics, techniques, and procedures (TTPs) used by sophisticated adversaries. This information can help CISOs adjust controls, identify security team members who may be overworked or need additional training, or locate ineffective security controls that need replacement. In this way, open XDR can also help CISOs measure ROI on security spending and guide them to areas requiring additional investment. .
Automates investigation and remediation actions. While not a full-function SOAR, Open XDR can be instrumented to take actions based upon the severity and types of synthesized alerts. For example, when a SIEM alert fires, open XDR can recognize the alert type and immediately pull the right EDR, NDR, and threat intelligence data needed for a full security investigation. Automation can also extend to incident response actions like blocking an IP address or file hashes, creating watchlists, or running IOC lookups against multiple technologies to uncover the scope of an attack. Leading open XDR solutions will also provide routines for automated threat hunting based upon the latest threat intelligence on exploits and campaigns. Open XDR can also integrate with existing SOAR platforms to participate in more comprehensive security operations workflows.
Rather than starting from scratch, open XDR can help organizations get more efficacy and efficiency from their existing controls. This is certainly a less disruptive path to SOAPA than replacing dozens of security tools, a project that could take years to accomplish. Aside from consolidation, open XDR also adds advanced analytics to help organizations detect “low and slow” attacks across endpoints, servers, and cloud workloads as they traverse the network. Open XDR should also help CISOs bolster security team members’ productivity and job satisfaction, which should result in better mental health and lower attrition rates. This will be especially true as organizations use open XDR for process automation. Finally, open XDR should help CISOs improve the measurement and management of their security stacks and isolate where budget dollars can make the biggest impact.
THE BIGGER TRUTH
There is an old Indian parable of the blind men and the elephant that Wikipedia describes as follows:
It is a story of a group of blind men who have never come across an elephant before and who learn and conceptualize what the elephant is like by touching it. Each blind man feels a different part of the elephant's body, but only one part, such as the side or the tusk. They then describe the elephant based on their limited experience and their descriptions of the elephant are different from each other.
The moral of the story is that the truth can only be known if all the blind men take the time to combine individual facts into a comprehensive picture.
Security operations follows a similar pattern. Individual security controls generate alerts based upon their myopic views of endpoints, networks, email, etc., but detecting and responding to a cyber-attack depends upon similar analysis from end to end across the entire IT infrastructure.
SOAPA and XDR are designed to be the “glue” that brings security operations together through technology integration, but this can require advanced skills, custom integration, or lengthy projects for XDR technology deployment. Open XDR can alleviate these issues, acting as an integration layer that sits on top of existing controls. If open XDR is also designed with advanced analytics, visualization, and automation workflows, it can greatly improve security efficacy and operational efficiency.
CISOs looking for a more expedient way to SOAPA may want to consider open XDR solutions as a path to get there.
Security confidence starts here.
1 Source: ESG Master Survey Results, Cloud-scale Security Analytics Survey, DEC 2019. All ESG research references and charts in this white paper have been taken from this master survey results set, unless otherwise noted.
This ESG White Paper was commissioned by Reliaquest and is distributed under license from ESG.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
