
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG WHITE PAPER
A Security Leader’s Guide to Leveraging MDR for Security Maturity and Development
By Dave Gruber, ESG Principal Analyst
JULY 2022
Building a Modern Cybersecurity Program
The Security Maturity Journey
Security Program Scalability
An ESG Security Industry Maturity Model
Figure 1. Five Levels of Security Maturity
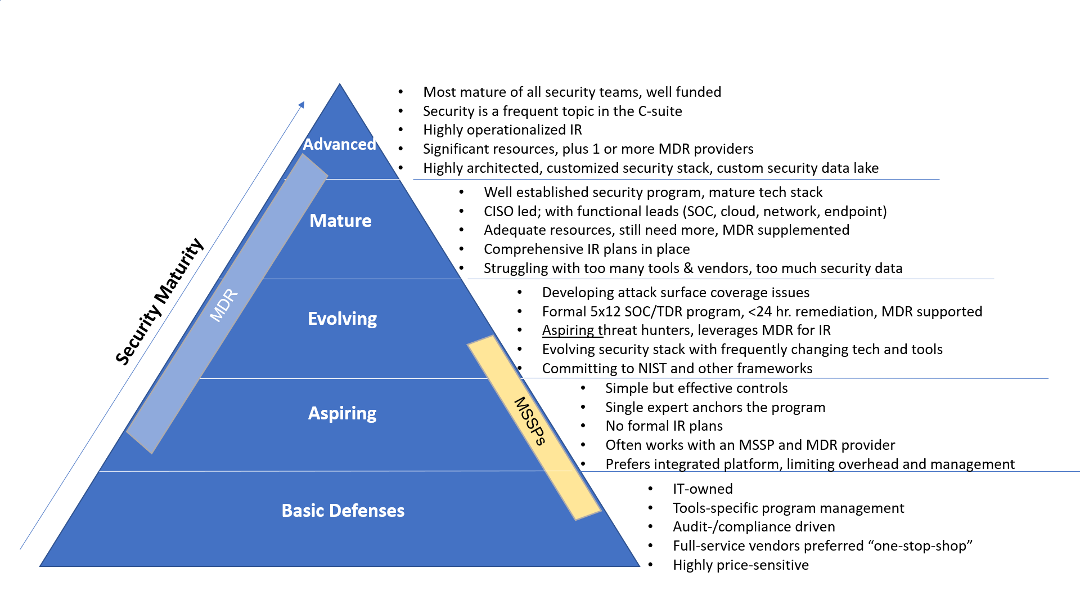
Source: ESG, a division of TechTarget, Inc.
5 Levels of Security Maturity
Ongoing Skills Shortages
Leveraging Managed Detection and Response Providers
MDR Core to Modern Security Strategies
Outcomes
MDR Outcomes:
Improvements in efficacy:
Operational/efficiency improvements:
o Lower security tools deployment and management costs.
o Increased 7x24x365 coverage at a lower cost.
Advancements in security program development:
Expanded staffing/skills coverage and growth:
Arctic Wolf Managed Security Operations Offerings
A Scalable, Open, Extensible Technology Platform
A Personalized Delivery Model
More than Detection and Response
The Bigger Truth
This ESG White Paper was commissioned by Arctic Wolf and is distributed under license from TechTarget, Inc.
All product names, logos, brands, and trademarks are the property of their respective owners. Information contained in this publication has been obtained by sources TechTarget, Inc. considers to be reliable but is not warranted by TechTarget, Inc. This publication may contain opinions of TechTarget, Inc., which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget, Inc.’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget, Inc. makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
This publication is copyrighted by TechTarget, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
