
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG ECONOMIC VALIDATION
Analyzing the Economic Benefits of Cobalt’s Pentest as a Service (PtaaS) Model
By Aviv Kaufmann, Principal Validation Analyst; and Jen Duey and Justin Boyer, Validation Analysts
JULY 2022
Executive Summary
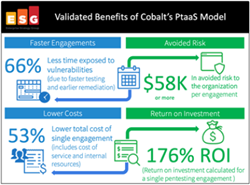
Introduction
Challenges
Figure 1. Actions to Improve Pentesting for Organizations
In your opinion, which of the following actions would most improve your organization’s penetration testing/red teaming program(s)?
Source: ESG, a division of TechTarget, Inc.
The Solution: Cobalt’s Pentest as a Service Model
Figure 2. Cobalt’s Pentest as a Service Model
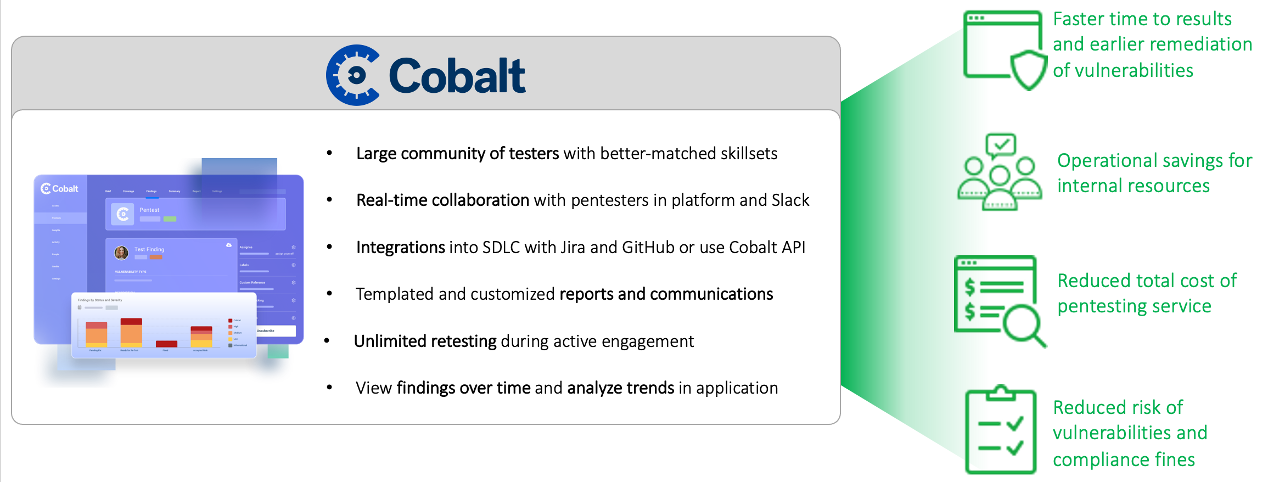
Source: ESG, a division of TechTarget, Inc.
• Streamline remediation and reporting workflows by integrating with customers’ existing tech stack.
• Streamline communication between security and development.
• Create a single pane of glass for all pentest findings.
• Feed internal security dashboard with custom pentest data.
• Automatically push pentest findings to internal system(s).
• Accelerate remediation cycle by automating workflows and communication.
• Use data to calculate internal performance metrics and track historical progress.
• Get comprehensive information about assets, associated findings, and events.
• Define filters to include criteria and make queries more specific.
ESG Economic Validation
Cobalt PtaaS Economic Overview
Faster Time to Results and Remediation – Begin remediating critical vulnerabilities within days of starting a test.
Operational Savings – Reduced organizational overhead to manage the pentest.
Reduced Cost and Risk to the Organization – Cost flexibility and a reduced chance of a data breach.
Faster Time to Results and Remediation
“Traditional consultancy lead times can be between four and eight weeks depending on the time of year and the resources available. With Cobalt, the lead time to begin testing was inside 48 hours.”
“One of the best things was being able to collaborate with the testers through the platform as well as through Slack. We got on-the-fly updates to the dashboard and were able to work on fixing issues as they were still testing.”
“80% of our retesting was finished before the engagement was over.”
Operational Savings and Efficiency
“The engagement came with a customer success manager who is your partner from day one. The support you get from the platform and guided experience saves you a lot of time.”
“We had to achieve compliance for two standards, and we just don’t have the experience or resources in-house to dedicate to pentesting. There is no way we could have done it that timeframe without Cobalt .”
“Data is stored for subsequent testing, allowing you to go through the pentest wizard and test the same asset you’ve already collected within the platform, so to spin up the next test is so much faster.”
Reduced Cost and Risk to the Organization
“You have to pick the best choice between price, quality, and other elements related to the end result. We interviewed four or five different companies. Cobalt’s value was awesome as opposed to other providers.”
“With Cobalt we were able to address all of the critical vulnerabilites before the end of the engagement – with other testers we would not have even had a report of what was found by then.”
ESG Analysis
Why This Matters
Figure 3. Cobalt Provides Faster Pentesting Engagement and Remediation of Critical Vulnerabilities
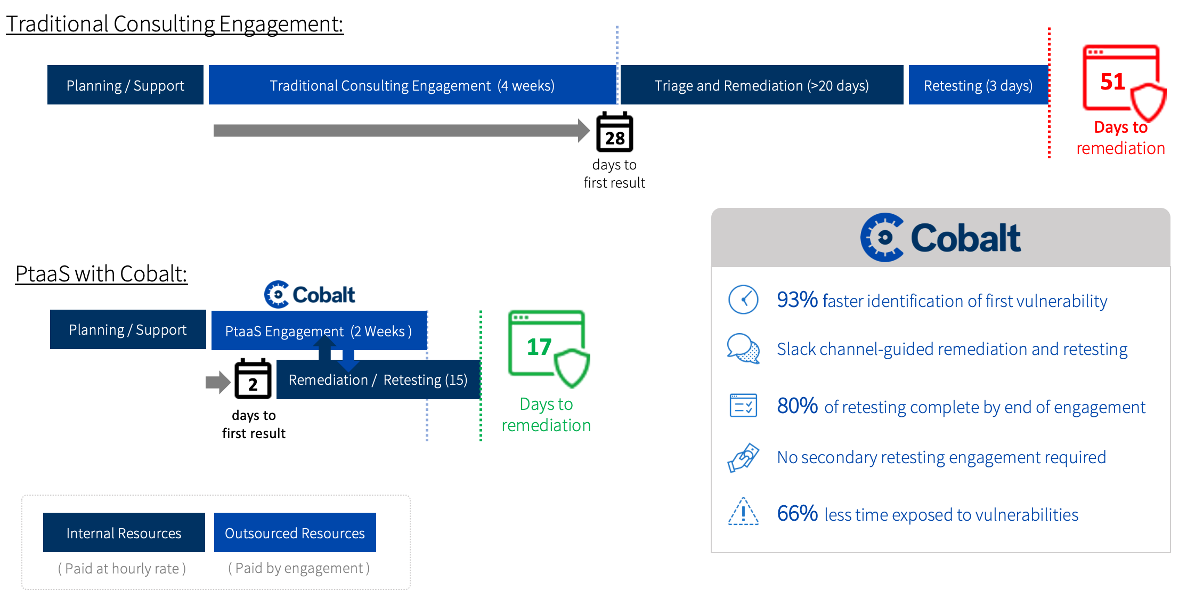
Source: ESG, a division of TechTarget, Inc.
Figure 4. Cobalt Provides Lower Total Cost of Engagement and Remediation of Critical Vulnerabilities
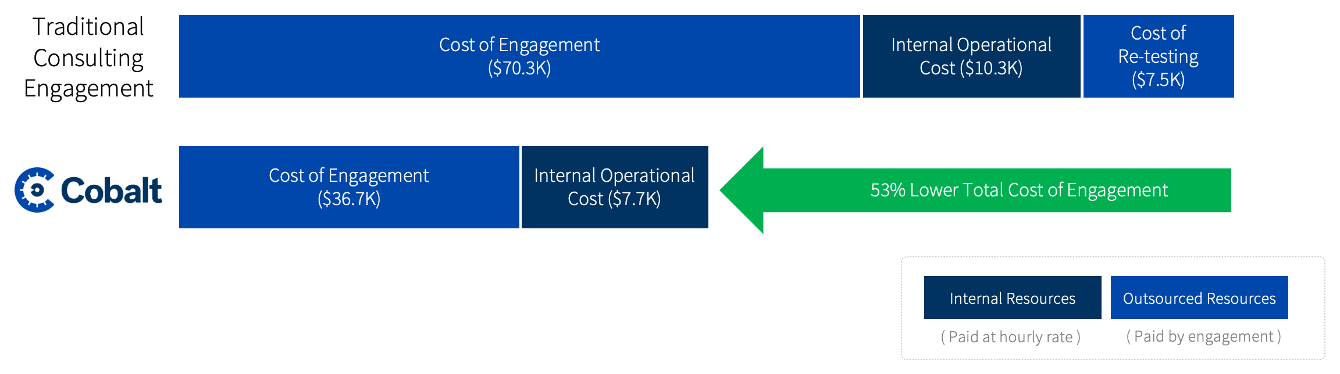
Source: ESG, a division of TechTarget, Inc.
Figure 5. Expected Avoided Cost of Data Breach Due to Earlier Remediation of Critical Issues
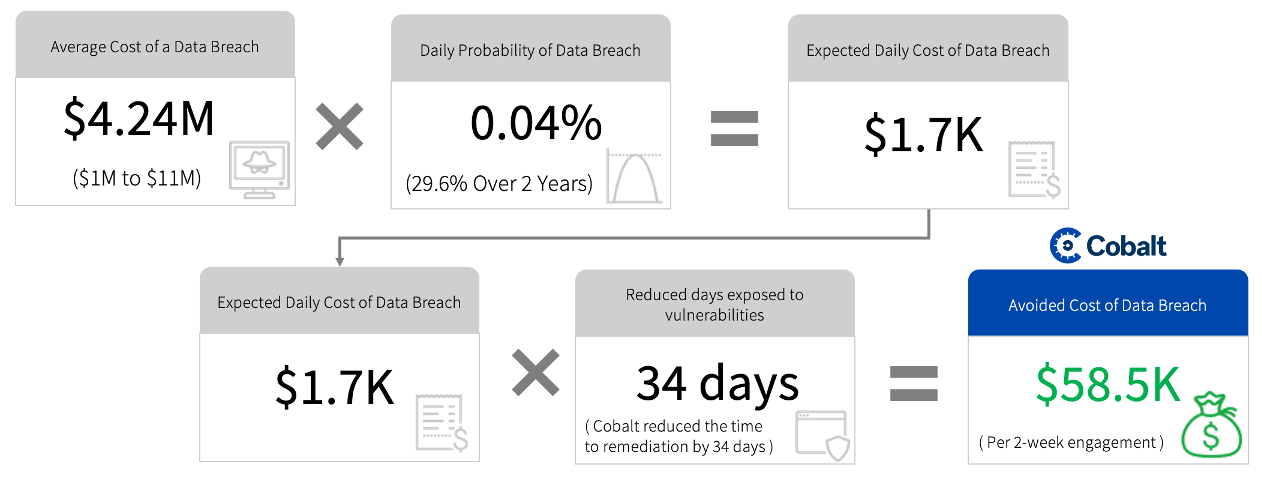
Source: ESG, a division of TechTarget, Inc.
Issues to Consider
The Bigger Truth
This ESG Economic Validation was commissioned by Cobalt and is distributed under license from TechTarget.
All product names, logos, brands, and trademarks are the property of their respective owners. Information contained in this publication has been obtained by sources TechTarget, Inc. considers to be reliable but is not warranted by TechTarget, Inc. This publication may contain opinions of TechTarget, Inc., which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget, Inc.’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget, Inc. makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
This publication is copyrighted by TechTarget, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
