
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG ECONOMIC VALIDATION
Analyzing The Economic Benefits Of Trend Micro Vision One
By Nathan McAfee, Validation Analyst
MAY 2021
Executive Summary
ESG validated that organizations highly aligned with XDR:
- Suffered half as many attacks.
- Were 2.2 times more likely to detect a data breach or successful attack in only a few days or less.
- Were 60% less likely to report attack repropagation.
Introduction
Challenges
Figure 1. Top 7 Business Initiatives Driving Technology Spending
Which of the following business initiatives do you believe will drive the most technology spending in your organization over the next 12 months? (Percent of respondents, N=664, five responses accepted)
Source: Enterprise Strategy Group
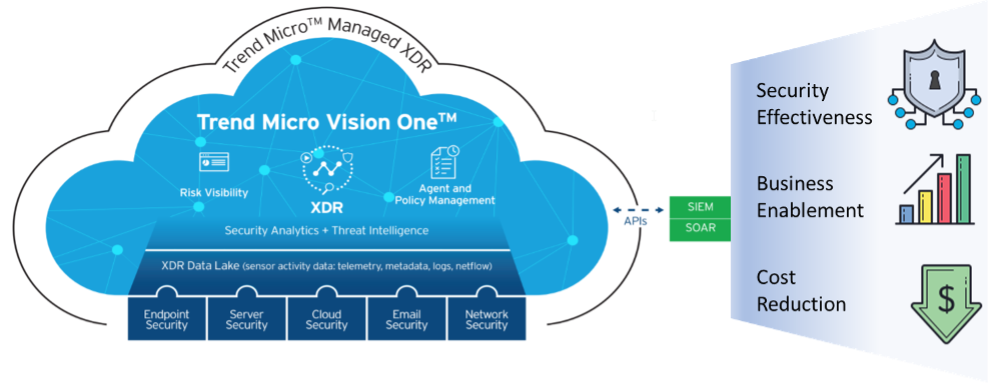
The Solution: Trend Micro Vision One
- Visualizing attacks through an interactive visual representation of events within an endpoint, server, or cloud workload.
- Engaging network analysis capability to replay network communications to see details of command and control communications or lateral movement.
- Mapping techniques to the MITRE ATT&CK framework and linking to related documentation.
- Searching the XDR data lake through all or specific data sources and combining criteria with the MITRE ATT&CK framework.
- Connecting to SIEM and SOAR platforms via APIs.
Figure 2. Trend Micro Vision One Platform
ESG Economic Validation
Alignment with XDR Leads to Better Overall Security Posture
Figure 3. ESG’s XDR Value Assessment Model
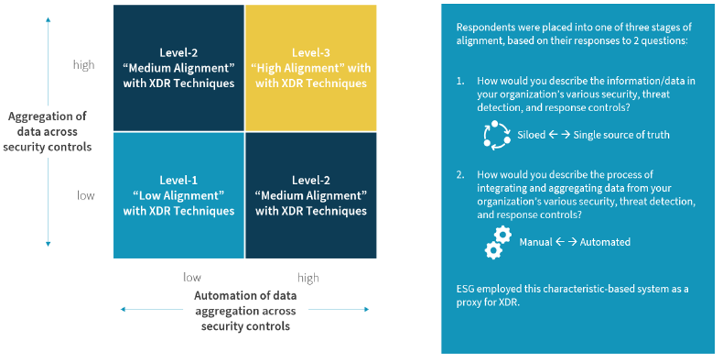
Figure 4. XDR Alignment Maturity Model Distribution

Figure 5. High Alignment with XDR Results in Greater Confidence in Threat Detection and Response
Thinking of the next 12-24 months, how confident are you that your organization's detection and response function can move at the speed needed to keep pace with threats and not negatively impact the business? (Percent of respondents)
Source: Enterprise Strategy Group
Trend Micro Economic Overview
Figure 6. Effective Threat Data Correlation Produces Operational Improvements
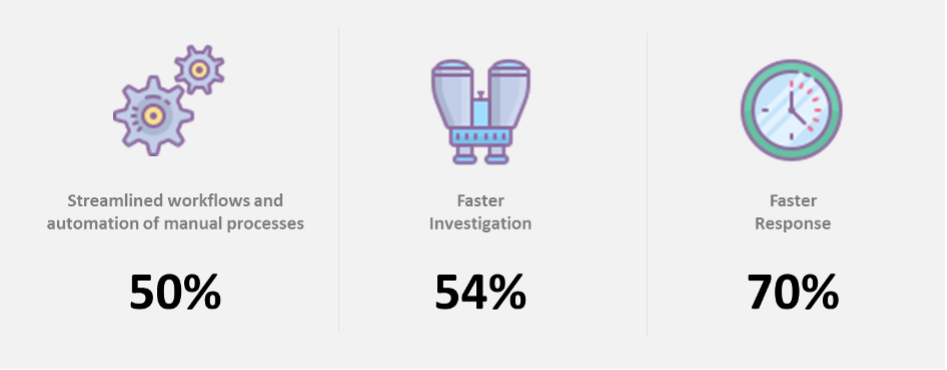
Security Effectiveness
“XDR tells a story. Not only can I see what is happening, I can quickly find everything that is impacted and immediately take action.”
– CISO, healthcare provider
Business Enablement
Cost Reduction
“I estimate it would be 5x to 6x more expensive if we tried to use our own employees and less effective at the same time.”
―Cybersecurity Administrator, local government agency
Annual Security savings with trend Micro XDR
The Bigger Truth
This ESG Economic Validation was commissioned by Trend Micro and is distributed under license from ESG.
1 Source: ESG Research Report, Cybersecurity in the C-suite and Boardroom, Mar 2021.
2 Source: ESG Research Insights Report commissioned by Trend Micro, The XDR Payoff: Better Security Posture, Sep 2020.
3 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021.
4 Source: ESG Research Insights Report commissioned by Trend Micro, The XDR Payoff: Better Security Posture, Sep 2020.
5 Ibid.
6 Ibid.
7 Ibid.
8 Source: ESG Research Report, Cybersecurity in the C-suite and Boardroom, Mar 2021.
9 Source: ESG Research Report, Cybersecurity in the C-suite and Boardroom, Mar 2021.
10 Ibid.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
