
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG SHOWCASE
Bolstering Your Cyber Resilience with Veritas
By Christophe Bertrand, Senior Analyst; and Monya Keane, Senior Research Analyst
SEPTEMBER 2021
Abstract
Market Landscape
Figure 1. Today’s Cyber-threat Landscape
43%
Of IT professionals are very concerned their backups can become infected
#1
Cybersecurity is the most-cited area for IT skills shortages
47%
See fortifying cybersecurity as a business issue driving technology spending
Leveraging the NIST Cybersecurity Framework
The framework provides guidance on how both internal and external stakeholders can manage and reduce those risks."
Figure 2. The NIST Framework
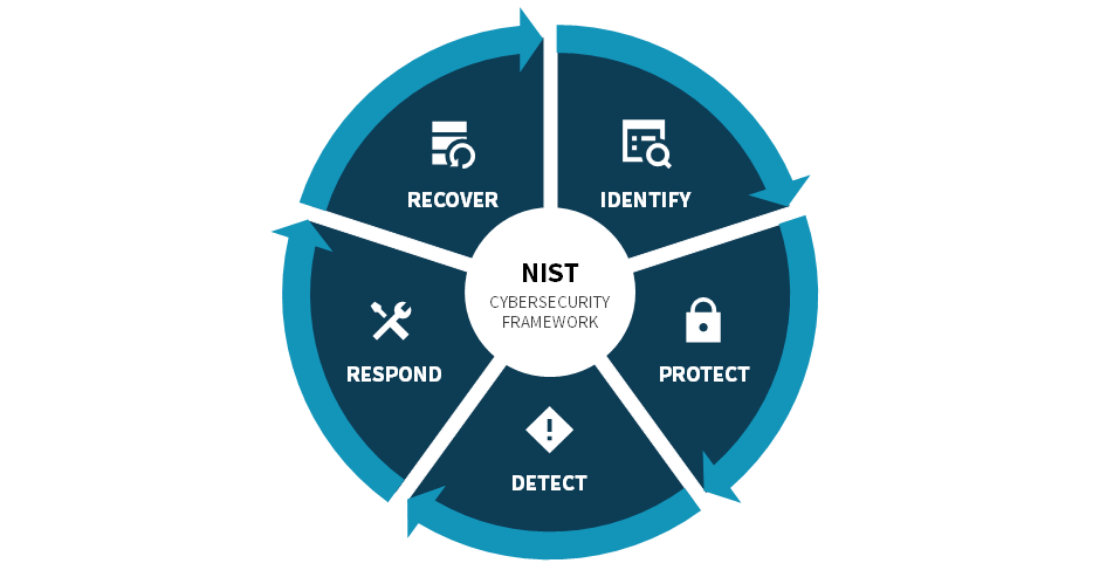
Focus on Protect, Detect, and Recover Using the Veritas Approach
Protect
Immutability
They are:
Air Gapping
Cloud and S3
Detect
Veritas NetBackup IT Analytics
Veritas Data Insight
Recover
Granular Recovery
Cloud
Orchestration and Testing
The Bigger Truth
Best-in-class enterprise data backup and recovery
This ESG Showcase was commissioned by Veritas and is distributed under license from ESG.
1 Source: ESG Master Survey Results, Tape’s Place in an Increasingly Cloud-based IT Landscape, Jan 2021.
2 Source: ESG Master Survey Results, Real-world SLAs and Availability Requirements, Aug 2020.
3 Source: ESG Master Survey Results, Tape’s Place in an Increasingly Cloud-based IT Landscape, Jan 2021.
4 Source: ESG Master Survey Results, 2021 Technology Spending Intentions Survey, Dec 2020.
5 ibid.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
