
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL REVIEW
Continuous Security Posture and Risk Management of Infrastructure-as-code with Tenable.cs
By Alex Arcilla, Senior Validation Analyst
JANUARY 2022
Abstract
The Challenges
Figure 1. CSP Infrastructure Presents Greatest Risk to Cloud-native Applications
Which element of the cloud-native application stack do you feel is most susceptible to compromise and therefore represents the greatest risk to your organization? (Percent of respondents, N=383)
Source: Enterprise Strategy Group
The Solution: Tenable.cs
Figure 2. The Tenable.cs Platform
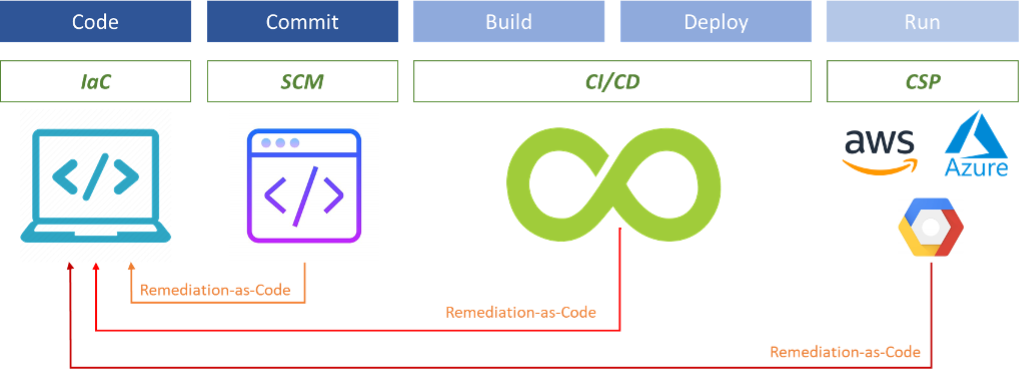
Source: Enterprise Strategy Group
ESG Tested
Figure 3. Grouping IaC via Projects
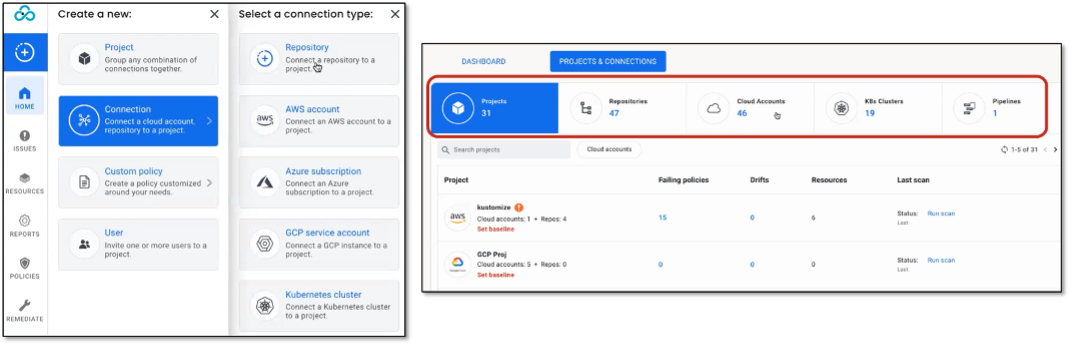
Source: Enterprise Strategy Group
Figure 4. Scanning for Policy Violations via Tenable.cs UI and CLI
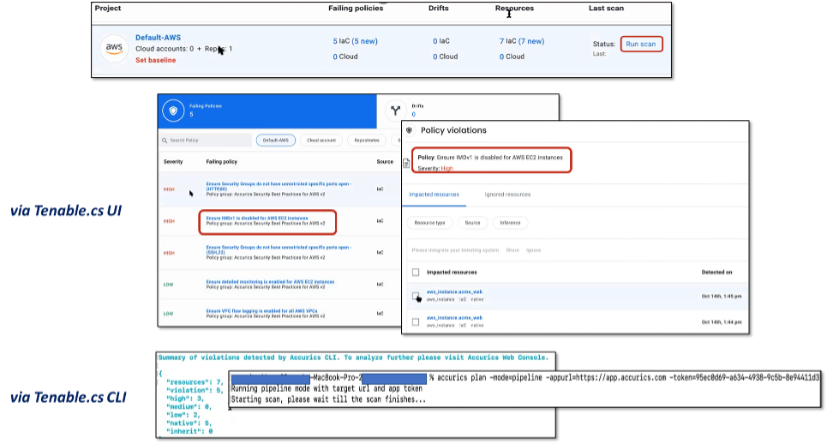
Source: Enterprise Strategy Group
Figure 5. Detecting Sources of Configuration Drift
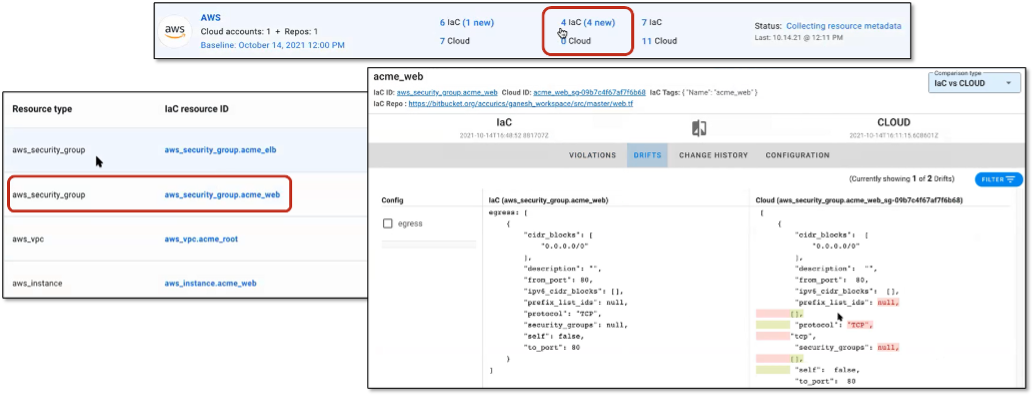
Source: Enterprise Strategy Group
Figure 6. Scanning for Vulnerabilities in Pipeline Repositories
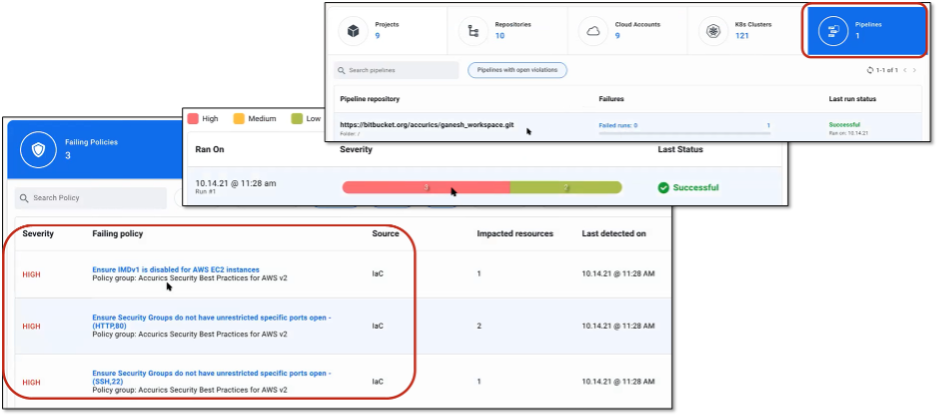
Source: Enterprise Strategy Group
Figure 7. Generating Pull Request and Specifying Remediation for Single Policy Violation
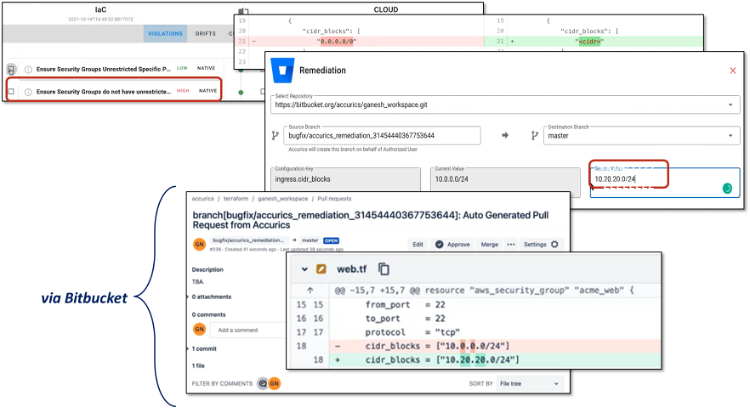
Source: Enterprise Strategy Group
Figure 8. Generating IaC Fixes via Auto-remediation for Multiple Policy Violations
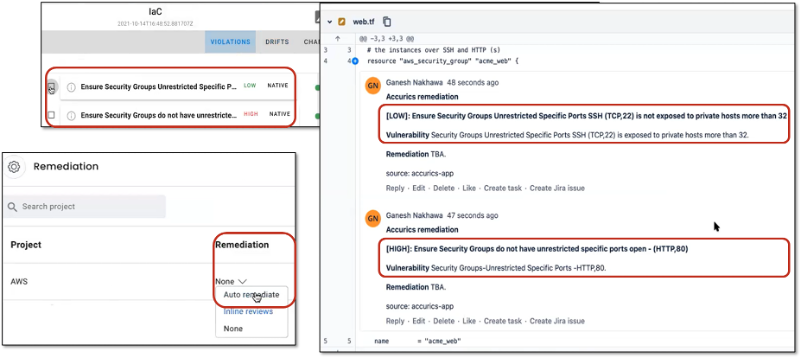
Source: Enterprise Strategy Group
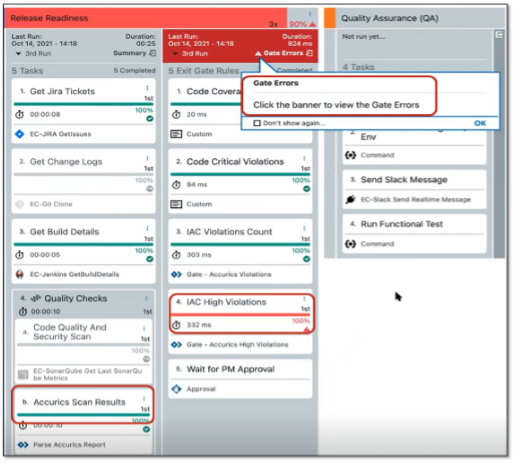
Figure 9. Tenable.cs Integration with Jenkins
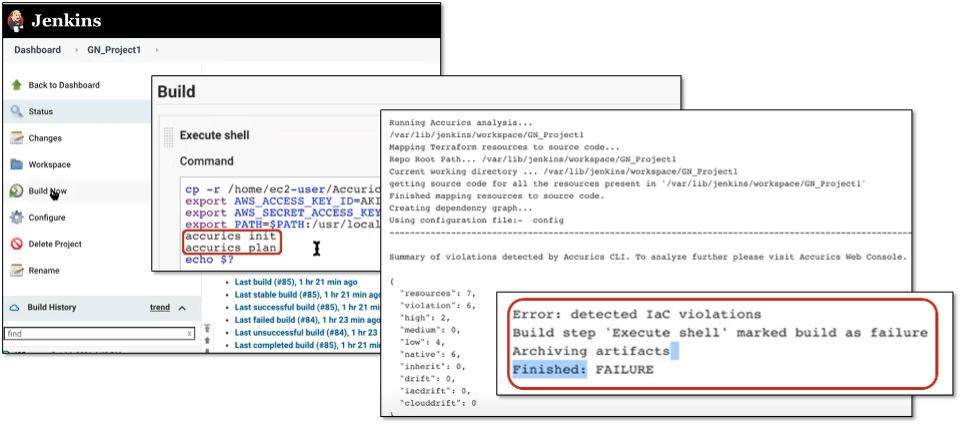
Source: Enterprise Strategy Group
Why This Matters
The Bigger Truth
- Proactively uncover vulnerabilities embedded in infrastructure throughout the application lifecycle.
- Remediate policy violations or cloud resource misconfigurations before they can be exploited during runtime.
- Identify and close security gaps when code is integrated into existing code bases before committed to the final build.
This ESG Technical Review was commissioned by Tenable.cs and is distributed under license from ESG.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
