
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL VALIDATION
IBM Cloud Pak For Security
Modernizing Security Visibility and Response in a Hybrid Multi- Cloud World
By Alex Arcilla, Senior Validation Analyst
MAY 2021
ESG Technical Validations
Introduction
Background
Figure 1. Top Ten Reasons for Increasing Complexity in IT Environments
What do you believe are the biggest reasons your organization’s IT environment has become more complex? (Percent of respondents, N=496, five responses accepted)
Source: Enterprise Strategy Group
IBM Cloud Pak for Security
Figure 2. IBM Cloud Pak for Security
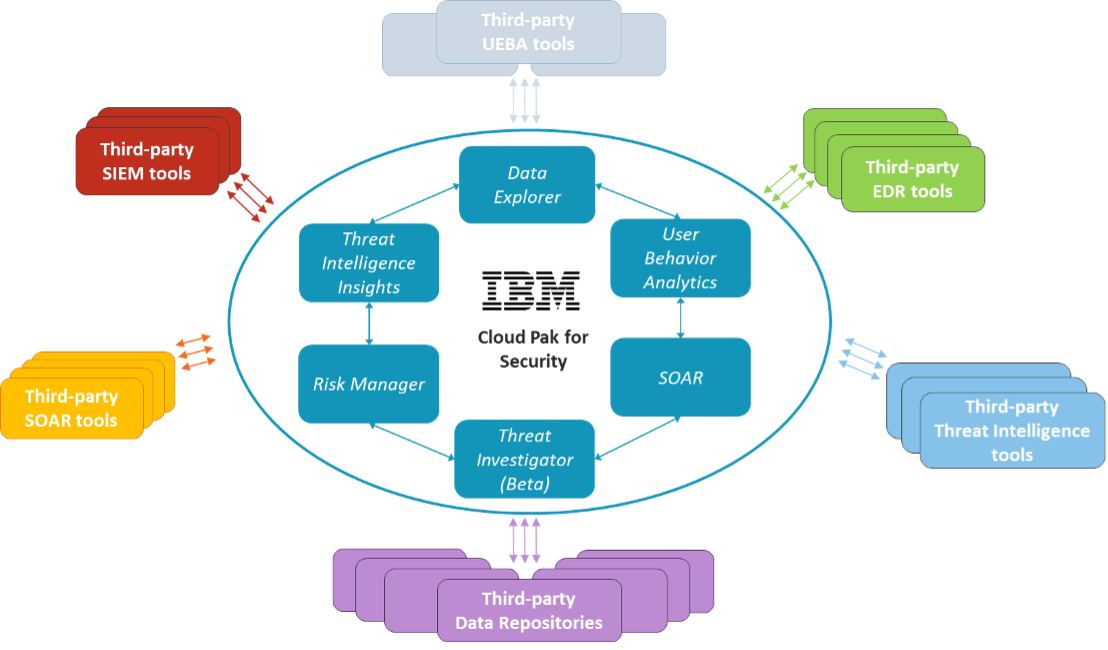
Source: Enterprise Strategy Group
ESG Technical Validation
Threat Hunting
ESG Testing
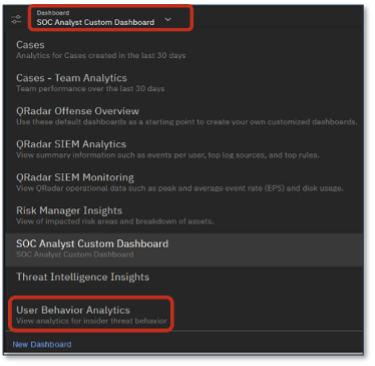
Figure 3. Examining the Extent of Infiltrated Threat with User Behavior Analytics
Source: Enterprise Strategy Group
Figure 4. Discovering Threat via IBM Threat Intelligence Insights
Source: Enterprise Strategy Group
Figure 5. Running Data Explorer to Discover Effects of BLADABINDI Malware on Overall Security
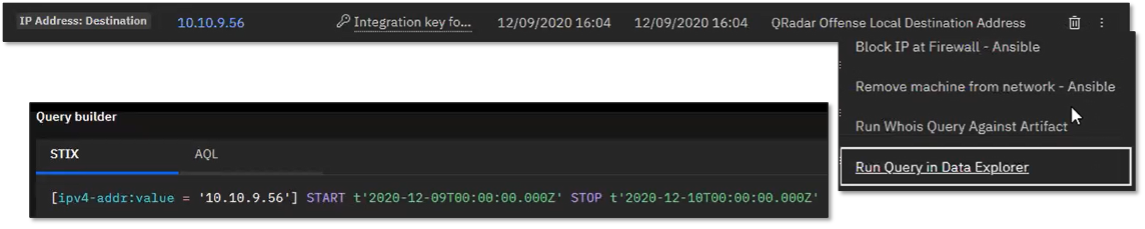
Source: Enterprise Strategy Group
Figure 6. Investigating Severity of Threat Introduced with BLADABINDI Malware
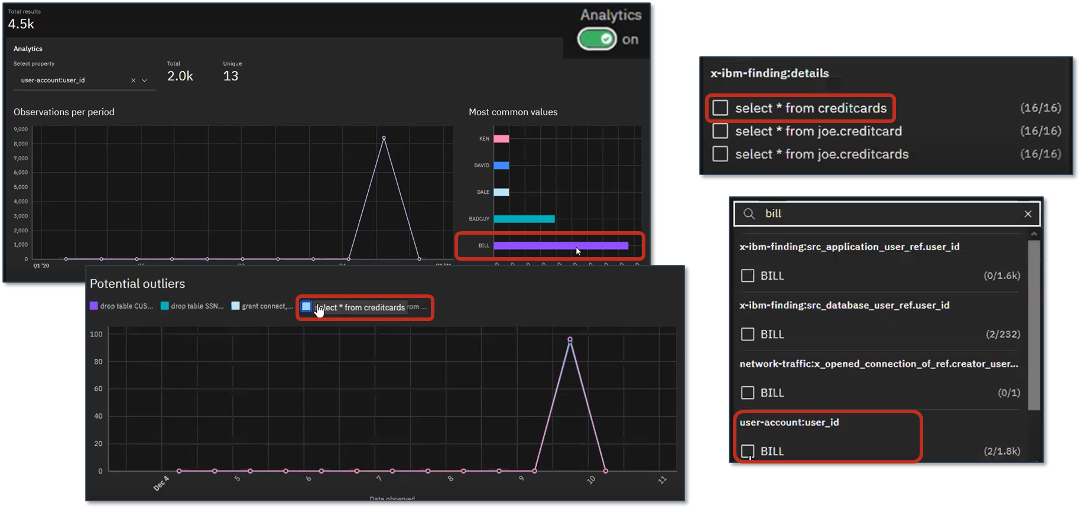
Source: Enterprise Strategy Group
Figure 7. Adding Artifact to Existing Case
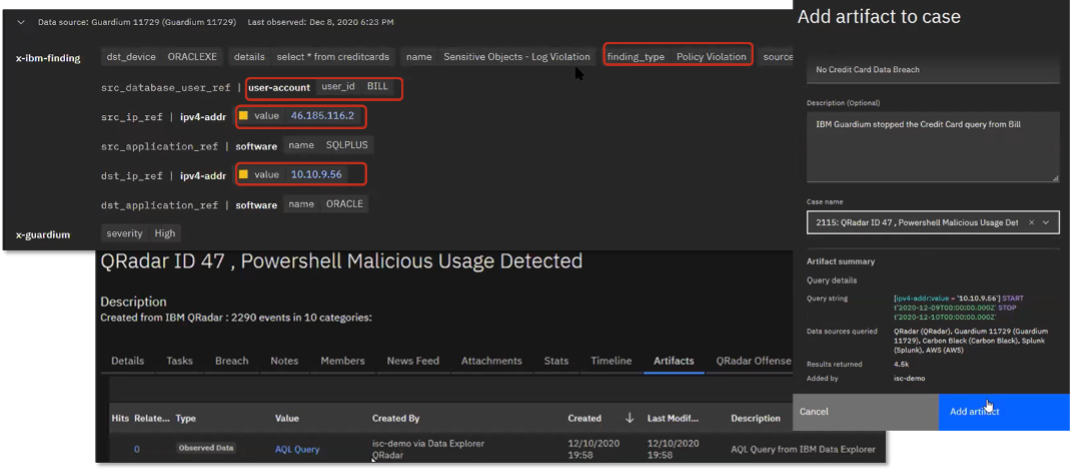
Source: Enterprise Strategy Group
Why This Matters
Incident Response
ESG Testing
Figure 8. Tile View of Cases to be Addressed, by Stage of Response
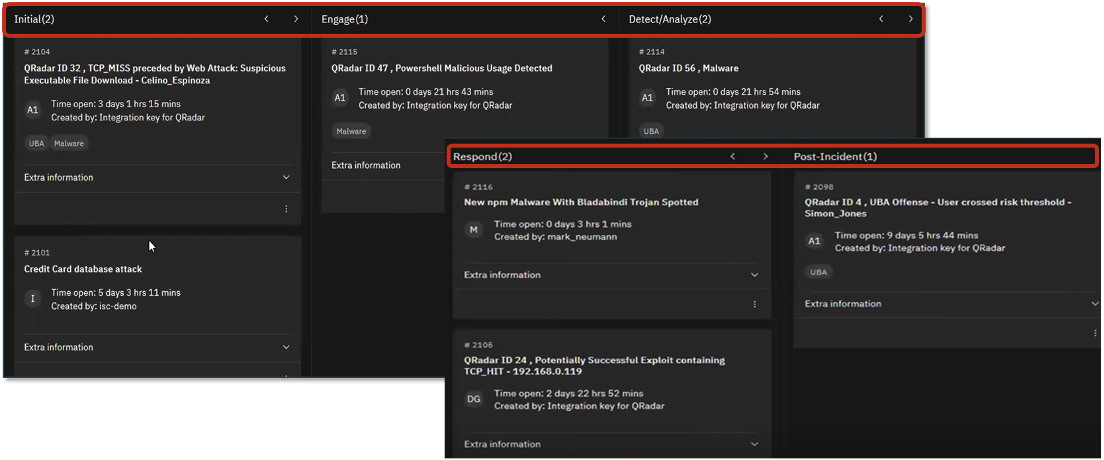
Source: Enterprise Strategy Group
Figure 9. Case Description and Tasks to be Completed
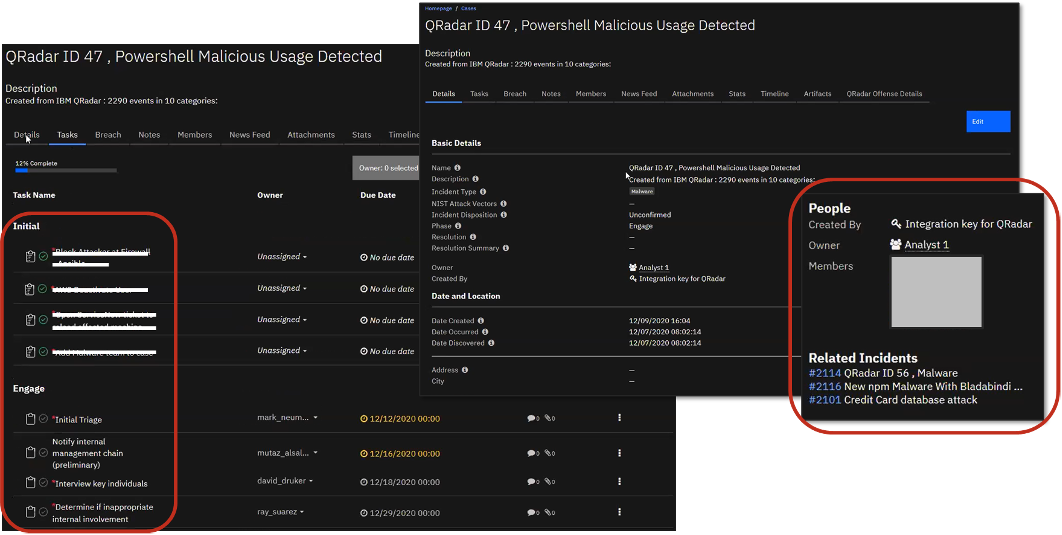
Source: Enterprise Strategy Group
Figure 10. Creating a Playbook using the “Breach” Module
Source: Enterprise Strategy Group
Why This Matters
Data Security
ESG Testing
Figure 11. Assessing Risk Posture of Organization’s Databases
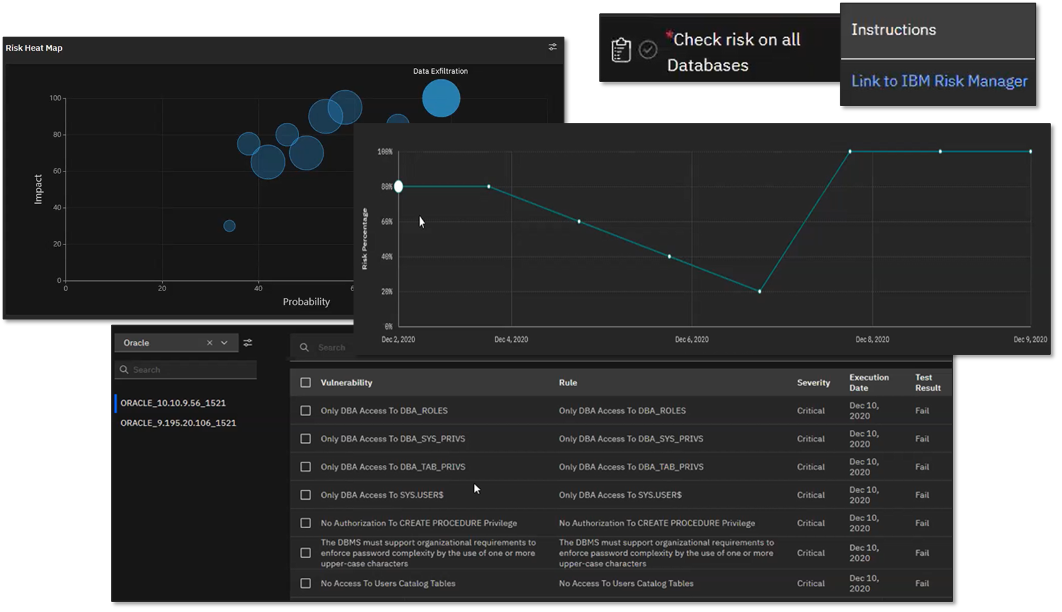
Source: Enterprise Strategy Group
Why This Matters
The Bigger Truth
- Locate threats without the need to correlate data manually from multiple tools and data sources.
- Prioritize threats to address and remediate so that an organization is less susceptible to breaches and attacks.
- Automate and orchestrate the necessary steps to respond to threats and breaches quickly, minimizing the need for manual intervention.
- Assess and improve the organization’s risk profile over time.
This ESG Technical Validation was commissioned by IBM and is distributed under license from ESG.
1 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021.
2 IBM Security Guardium Insights helps organizations to construct a comprehensive view of their data security and compliance landscapes.
3 BLADABINDI is a backdoor threat. If it infiltrates an organization, it stealthily downloads and installs malware onto affected systems.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
