
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL VALIDATION
Improve User Experience, Increase Security, And Enhance Business Value With Citrix Workspace
By Jack Poller, Senior Analyst
AUGUST 2021
ESG Technical Validations
Introduction
Background
Figure 1. Biggest Priorities for Employee Technology Experience
In terms of employee technology experience, what are your organization’s biggest priorities when it comes to delivering applications, data, and desktops/devices in the current work-from-home climate? (Percent of respondents, N=389, multiple responses accepted)
Source: Enterprise Strategy Group
Citrix Workspace
Figure 2. Citrix Workspace Platform
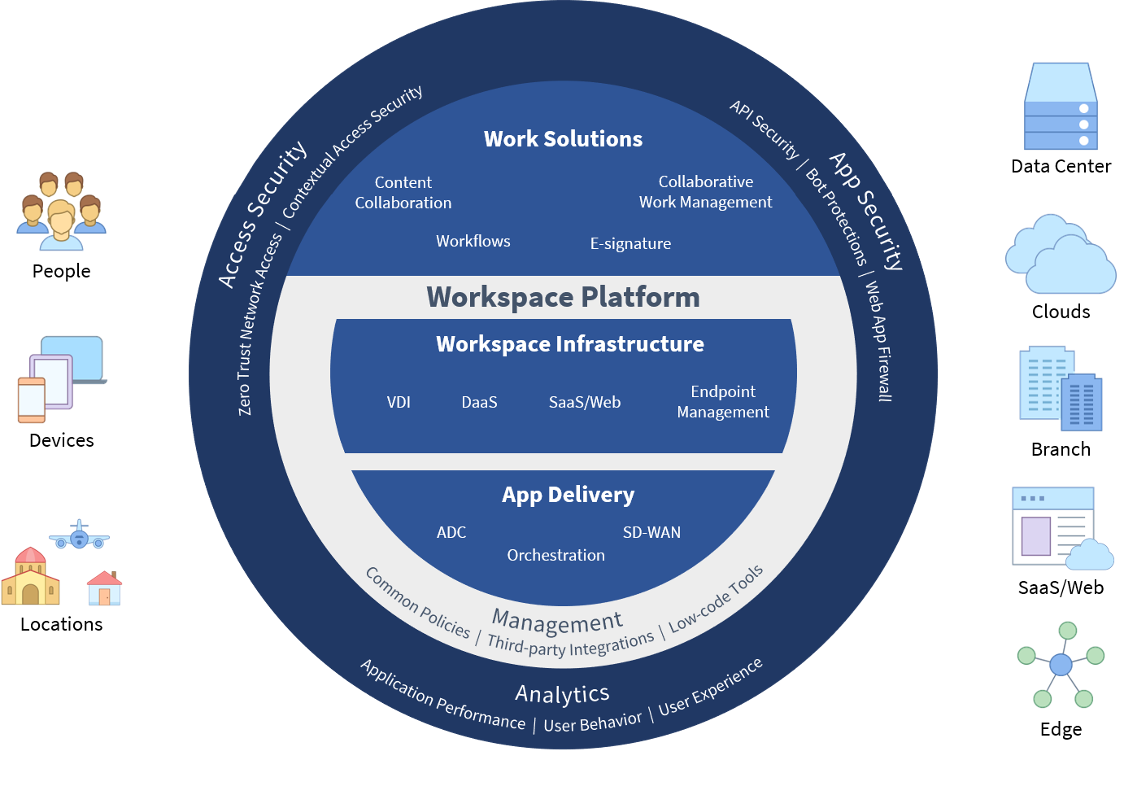
Source: Enterprise Strategy Group
“When the pandemic hit, most of the cities around us shut down. Because we had Citrix, we were able to immediately shift to work from home and continue operations.” –CIO respondent
ESG Technical Validation
Improved User Experience
“Our experience with Citrix has enabled our leadership to break paradigms about how government services are delivered and has opened the door so we can hire critical talent that lives outside of our city.” –CIO, City of 160,000 with 1,000 employees
Figure 3. Citrix Workspace Home Page
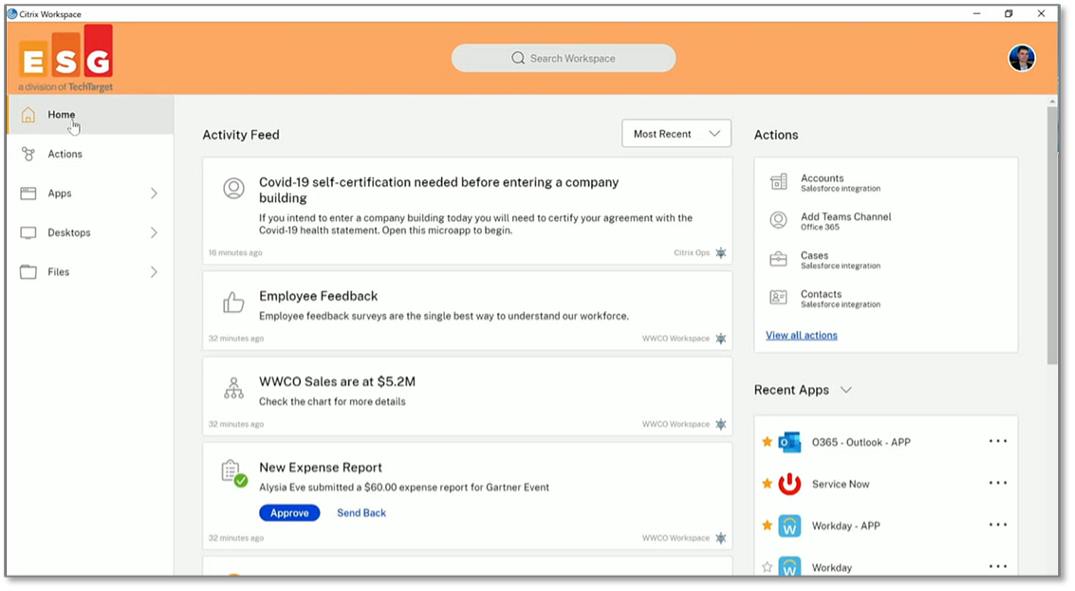
Source: Enterprise Strategy Group
Figure 4. Workspace Apps and Virtual Desktops
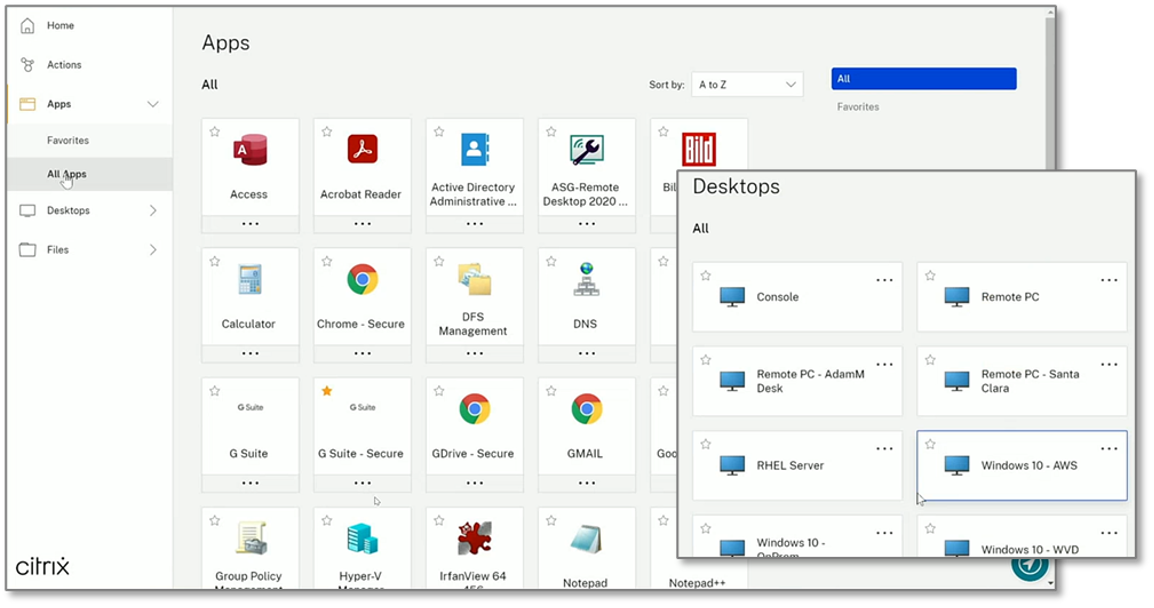
Source: Enterprise Strategy Group
“Citrix enables our employees to securely access their applications from anywhere at any time, and our data shows that our employees are more productive now that we're using Citrix.” –CIO respondent
Figure 5. Workspace Integrated Files and Folders
Source: Enterprise Strategy Group
Why This Matters
Increased Security
“Citrix enables our employees to securely access their applications from anywhere at any time, and our data shows that our employees are more productive now that we're using Citrix.” –CIO respondent
Figure 6. Watermarking Apps for Security
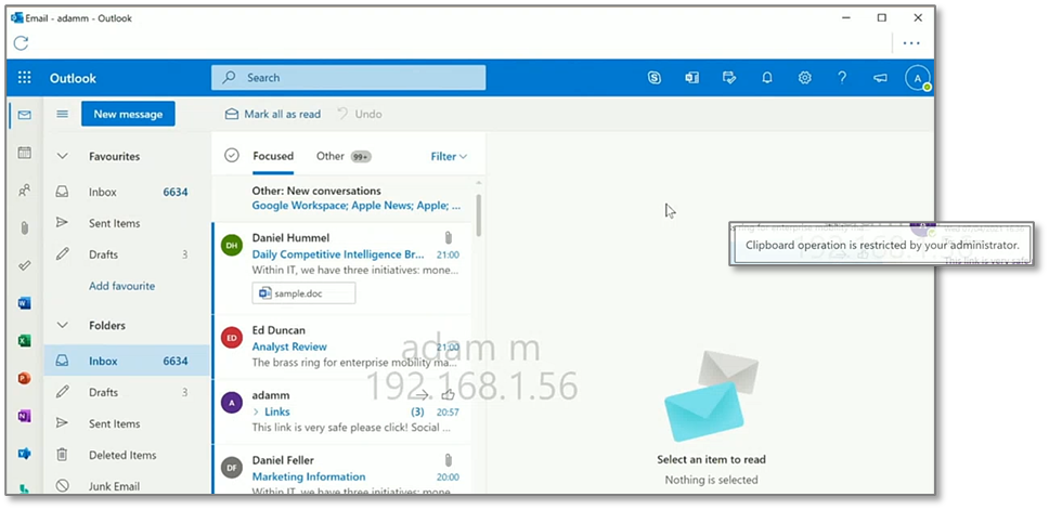
Source: Enterprise Strategy Group
Figure 7. Workspace Administrator’s Security Dashboard
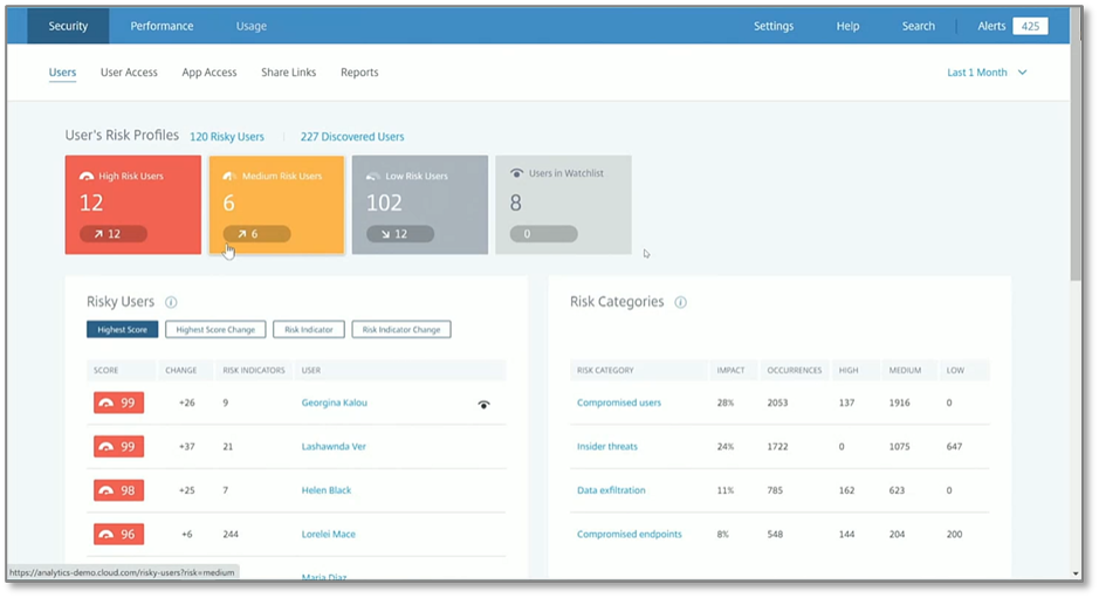
Source: Enterprise Strategy Group
Figure 8. High-risk User Behavioral Analysis
Source: Enterprise Strategy Group
Why This Matters
Enhanced Business Value
Figure 9. Improving User Workflows with Microapps
Source: Enterprise Strategy Group
Figure 10. Analysis of User Experience
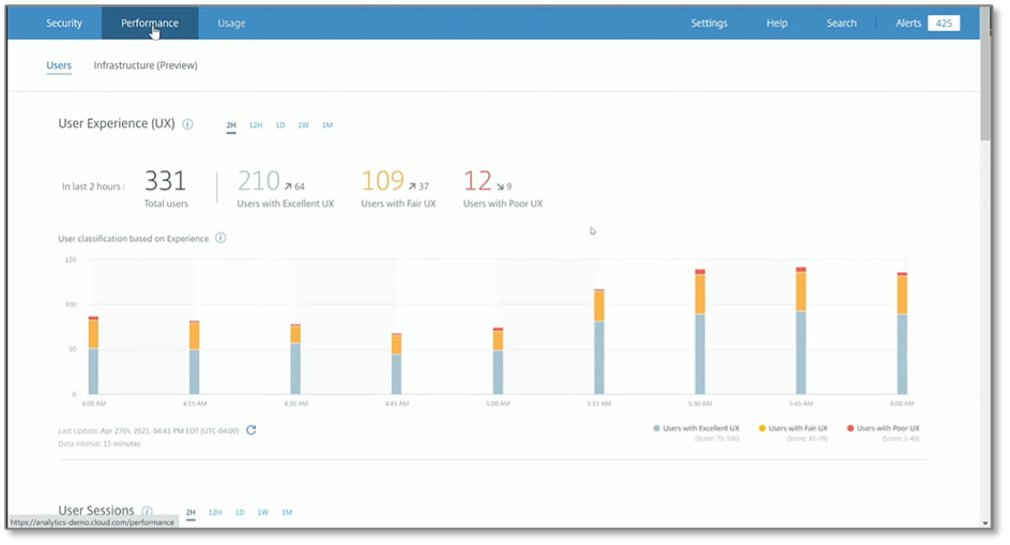
Source: Enterprise Strategy Group
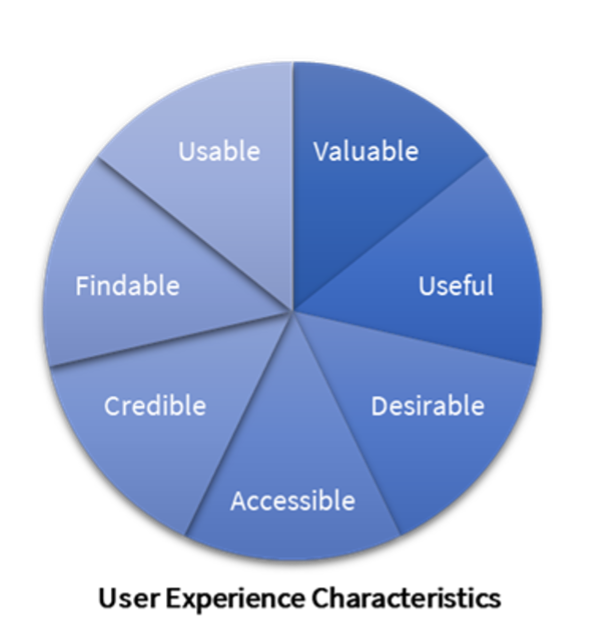
Figure 11. User Experience Classification Factors
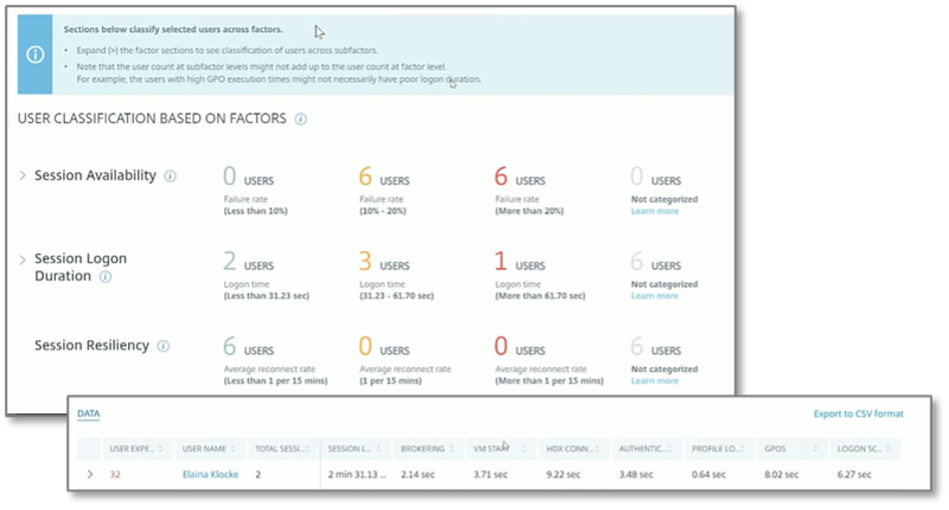
Source: Enterprise Strategy Group
Why This Matters
The Bigger Truth
This ESG Technical Validation was commissioned by Citrix and is distributed under license from ESG.
1 Source: ESG Master Survey Results, Digital Workspace Strategies in an Increasingly Remote Worker World, May 2021.
2 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021. All ESG research references in this technical validation have been taken from this research report unless otherwise noted.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
