
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL REVIEW
Microsoft Active Directory Disaster? Recover at Least Five Times Faster with Quest Recovery Manager
By Jack Poller, Senior Analyst; and Eve Falk, Associate Validation Analyst
NOVEMBER 2021
Executive Summary
What we found. AD is a mission-critical component of the IT infrastructure. When AD fails, either from ransomware, cyberattacks, or catastrophes, the IT environment comes to a grinding halt, which means the entire organization stops working until AD is restored.
Quest RMADDRE automates the manual Active Directory recovery process documented in Microsoft’s Active Directory Forest Recovery Guide. This onerous, error-prone, and lengthy manual process includes 18 major steps (each with many minor steps) that must be coordinated and synchronized across the entire suite of DCs being recovered. Automating the manual process significantly reduces the opportunity for manual errors.
Quest RMADDRE runs operations in parallel and synchronizes steps as necessary. This significantly accelerates the process and reduces the time to recover from an AD failure. Quest offers a wide variety of backup and recovery options, providing flexibility, speed, efficiency, and risk reduction for both backup and recovery operations.
Using RMADDRE can reduce risk, as the solution can scan backups for malware. In addition, RMADDRE can back up just the Windows components necessary to recover AD to a system with a clean install of Windows Server. This avoids backing up and restoring malware hiding in boot sectors, temporary directories, or system directories, and results in smaller, faster backups.
With Quest Recovery Manager, organizations can further accelerate the recovery process by first recovering the bare minimum number of DCs needed for proper operations. Once AD is operational, the teams responsible for recovering business applications, databases, and files can begin their recovery operations while the AD recovery team works in parallel to increase AD forest performance and capacity.
ESG-validated Benefits
- Performance: Recovering AD with Quest RMADDRE was at least 5 times faster than the manual process. Large environments with hundreds of DCs may require days to manually recover AD versus just a few hours when using Quest RMADDRE.
- Automation: Automating the process drastically reduced the amount of keyboard interaction and concomitant risk of human error.
- Reduced Risk: By avoiding backing up non-critical files and directories, and scanning for malware during backup and recovery, Quest RMADDRE reduces the possibility of reintroducing malware during recovery operations.
- Flexibility: Recovering to a clean OS install and implementing a two-phase recovery process provides flexibility while simultaneously accelerating time to recovery.
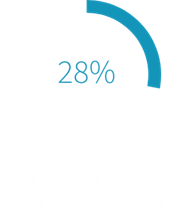
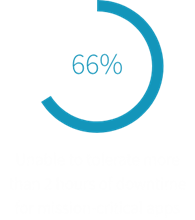
The Challenges



The Solution: Quest Recovery Manager for Active Directory Disaster Recovery Edition
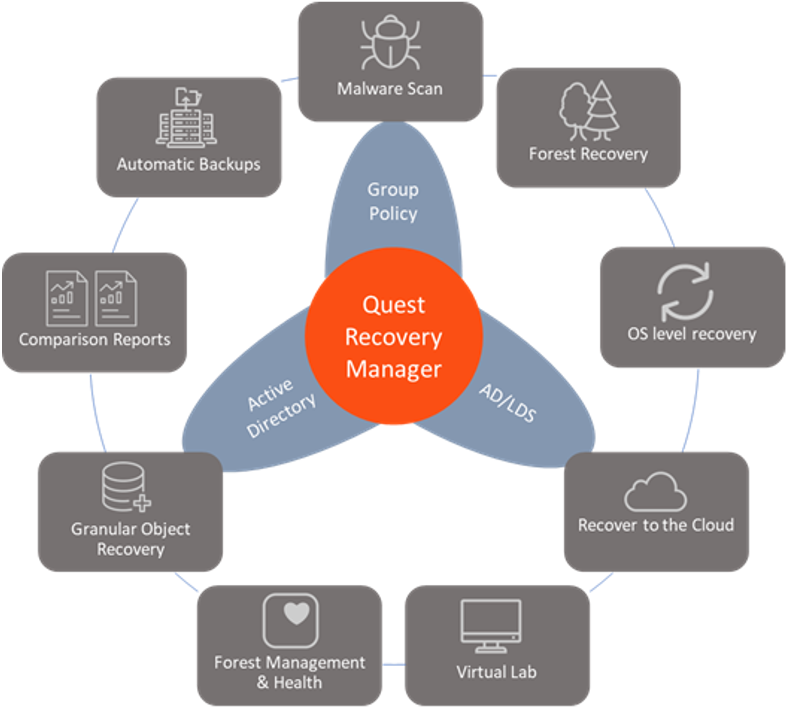
Key features of Quest RMADDRE include:
- Automation. Quest Recovery Manager automates the complex recovery process, removing the element of human error. RMADDRE runs operations in parallel and synchronizes tasks when necessary, simplifying and accelerating the recovery process.
- Flexibility and choice. RMADDRE offers a wide variety of options, from a Clean OS recovery method to bare metal. Organizations can simply remove a DC from the directory, promote in a replacement, force demote and/or re-promote it at any time. Admins can configure “pauses” at each stage of the recovery to verify or make configuration changes before continuing the process. And RMADDRE ensures that all critical roles and functions are healthy and available before confirming a successful recovery.
- Increased security. Recovery to clean OS systems reduces the footprint where undetected malware may be hiding, reducing the possibility of reinfecting AD from backups. Automated malware scanning enables scanning backups just before recovery.
- Increased efficiency and reliability of AD backups. Quest has analyzed Microsoft’s native System State backups and removed any elements that are not necessary for AD recovery. This reduces the size of the backup set, increasing efficiency and reliability, and prevents backing up malware hiding in system storage.
- Avoidance of malware reinfection. RMADDRE can scan for malware during both backup and recovery processes, reducing the possibility of malware reinfection.
- Phased recovery to shorten recovery time objective (RTO). Quest Recovery Manager enables organizations to recover their AD in phases. Quickly recovering the most critical domain controllers (DCs) first enables organizations to start recovery of dependent services and quickly enable employee access to key applications. Organizations can increase AD capacity, availability, and reliability by recovering or adding DCs in subsequent phases.
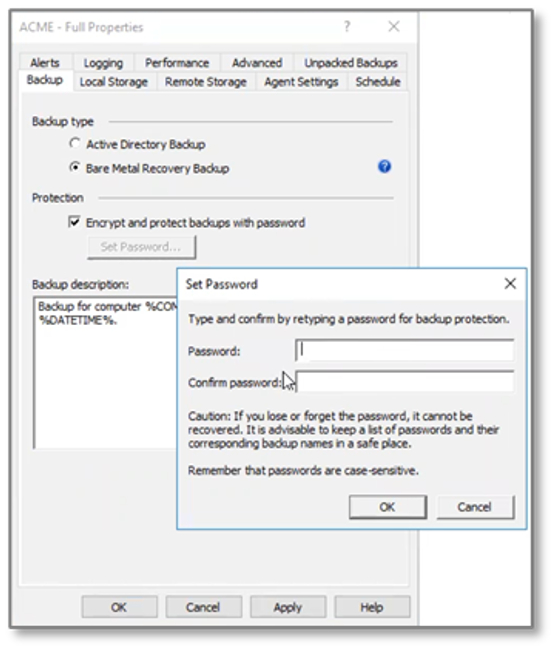
- Encrypted AD backups. RMADDRE can encrypt backups to prevent malicious actors from accessing sensitive information such as passwords.
- Protected AD backups. Quest Secure Storage is a hardened server that is completely isolated using IPSec rules with checks to confirm backup integrity. Even if an organization suffers a ransomware attack or loses the DCs, tier-1 storage, or the Recovery Manager server, the organization will still be able to recover using the protected backups in Secure Storage.
ESG Validated
- Back up each DC in the forest.
- Simulate a disaster by destroying all VMs in the forest.
- Simulate a recovery by creating new VMs.
- Recover three DCs, one for each domain, from backup to bare metal VMs.
- For Quest RMADDRE, recover three DCs, one for each domain, from backup to clean OS VMs.
- For Quest RMADDRE, perform a second phase of recovery, installing AD from media to new Windows Servers VMs.
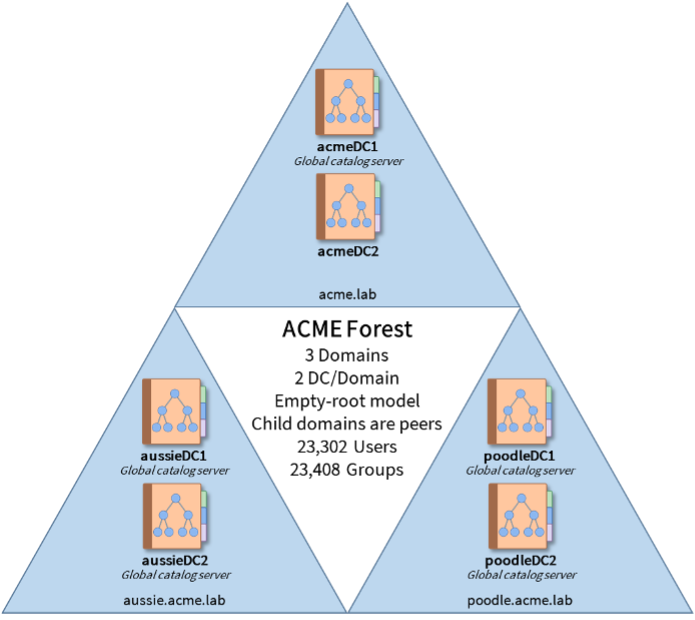
Manual Backup of the AD Forest
ESG Technical Validation
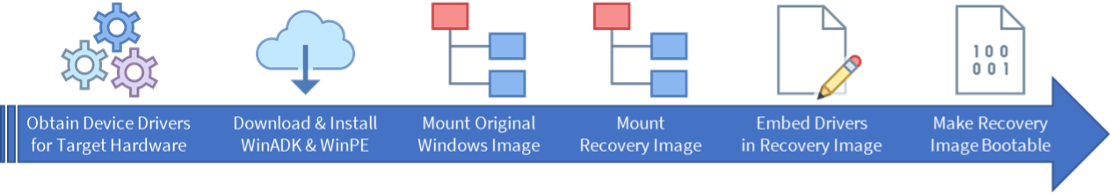
Figure 1. Create a Custom Windows Server Recovery Image
WHY THIS
MATTERS
Manual Recovery of the AD Forest
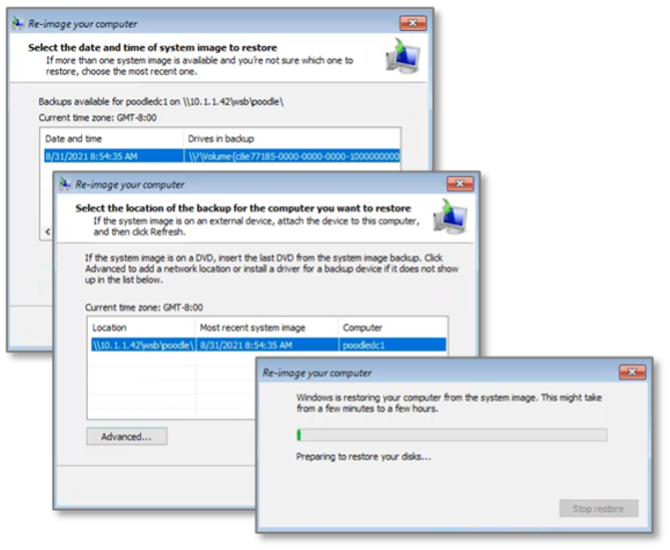
1. Verify network connectivity and DNS.
2. Reset the DC computer account passwords.
3. Raise the RID pool, invalidating any published RIDs.
4. Seize FSMO roles for the root domain.
5. Seize FSMO roles for all other domains.
6. Clean up the metadata of other DCs.
7. Reset the KRBTGT account password.
8. Reset internal Trust passwords.
9. Validate SYSVOL share is available.
10. Add the Global Catalog.
Figure 2. Reconfiguring AD Post-restoration
WHY THIS
MATTERS
Quest RMADDRE Automated Backup
Quest RMADDRE Automated Recovery to Bare Metal
Figure 3. Configuring RMADDRE to Recover AD Forest to Bare Metal Servers
Figure 4. RMADDRE Recovery Process with Sync Points
Quest RMADDRE Backup and Recovery to Clean OS
Two-phased AD Forest Recovery
Figure 5. Phase Two: Install AD from Media
Time and Risk Reduction Analysis
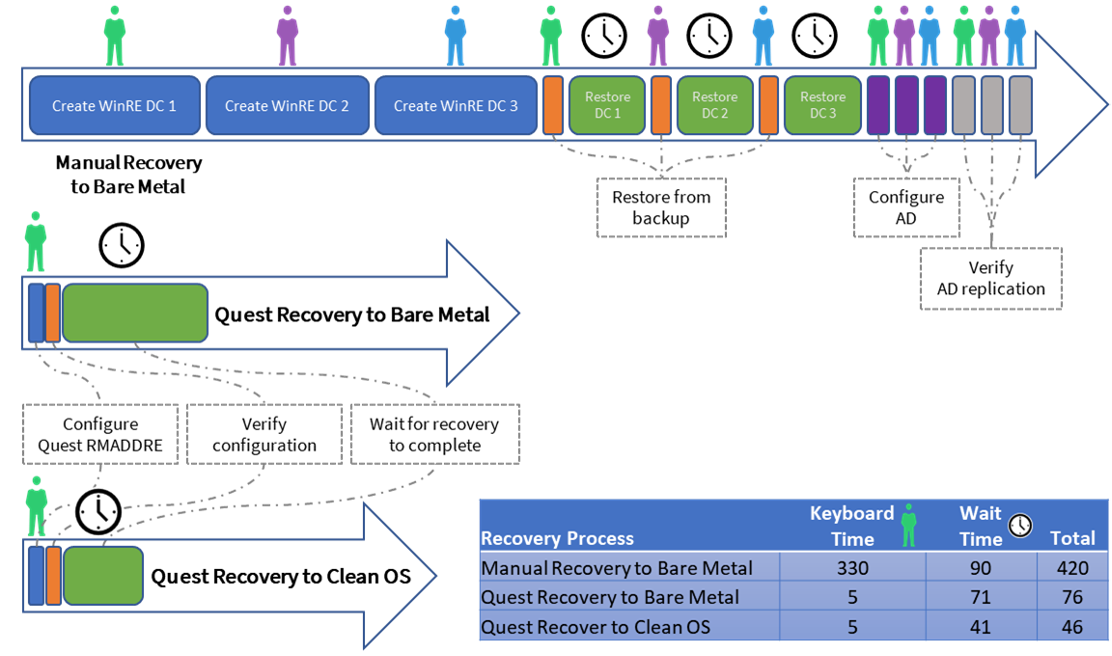
Figure 6. Time and Effort to Recover AD Forest
WHY THIS
MATTERS
The Bigger Truth
ESG validated that:
- Quest RMADDRE automated and accelerated the manual recovery process recommended by Microsoft and documented in Microsoft’s Active Directory Forest Recovery Guide. This onerous process consists of 18 major steps, each of which involves a complicated set of actions that must be coordinated and synchronized across the entire suite of DCs being recovered.
- Quest RMADDRE significantly reduced the opportunity for human error. We configured and verified the recovery configuration before proceeding, and Quest RMADDRE reduced the amount of keyboard interaction from hours scattered throughout the manual process to just minutes at the start of the process.
- Quest RMADDRE significantly reduced the time to recover an AD forest. Overall, Quest RMADDRE was more than five times faster than the manual process to recover the test bench AD forest to bare metal servers. ESG believes that each additional DC in the forest increases the manual recovery time and effort. The time to recover using Quest RMADDRE, which runs operations in parallel, will not be greatly affected by the number of DCs. Large environments with hundreds of DCs may require days to manually recover AD versus just a few hours when using Quest RMADDRE.
- • The ability to implement a two-phase recovery process and to recover to clean OS install systems provided additional flexibility, reduced the possibility of reintroducing malware during the recovery process, and accelerated the process.
Recovery Manager for Active Directory Disaster Recovery Edition
This ESG Technical Review was commissioned by Quest and is distributed under license from ESG.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
