
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG WHITE PAPER
Modern Application Security is Failing
A Multidimensional Approach to Application Risk with Apiiro
By Dave Gruber, ESG Senior Analyst
MAY 2021
Application Security Programs are Failing to Scale
Application development teams are under unprecedented levels of pressure to deliver as businesses accelerate digital transformation initiatives. As AppDev teams accelerate code development through code reuse, open source, cloud platform advancements, and investments in DevOps, Application Security teams are struggling to implement tools that can ensure high levels of application security while aligning with development velocity objectives. Modern deployment models are further adding complexity to application development risk assessment, requiring a combined analysis of application code changes, infrastructure code changes, API gateway changes, and cloud configuration changes to effectively determine material risk.
Development teams knowingly push application updates with risks on a regular basis. ESG research tells us that 79% of organizations knowingly push vulnerable code—48% regularly and 31% occasionally. When asked why, 54% said they did so to meet a critical deadline, with a plan to remediate in a future release.1 These teams are compromising security by releasing according to business demand.
Despite the use of multiple automated security tools, security, development, and compliance teams spend too much time focusing on the wrong things. With most tools lacking the necessary context to understand the true risk of a change, teams end up focusing too much time on changes with little business impact, and not enough time on the changes that matter. While multiple SQL injection vulnerabilities may introduce significant risk to an internet-facing application, the same vulnerabilities could be classified as low risk for an internally facing application. Accurate risk assessment requires context beyond simple vulnerability severity and application risk profiling. Understanding the likelihood and potential impact of an issue can completely change risk decisions.
So, the real question is, given the limited nature of AppSec tools and manpower, how effective are organizations at understanding the risks associated with pushing application changes with known risks, such as vulnerabilities, exposing PII, or the use of an unauthenticated API? Are these organizations truly making informed decisions?
Figure 1. Organizations Knowingly Push Vulnerable Changes
Has your organization ever pushed code to production with known organic vulnerabilities? (Percent of respondents, N=378)
Source: Enterprise Strategy Group
Figure 2. Time to Delivery Often Trumps Security
For which of the following reasons has your organization pushed code to production with known organic vulnerabilities? (Percent of respondents, N=323, multiple responses accepted)
Source: Enterprise Strategy Group
Shifting Security Left Is Not Enough
Despite the use of automated testing and analysis tools and the drive to move security left, the process of issue triage and prioritization is still highly manual and time-consuming. Existing tools often lack the necessary context for effective risk scoring, causing many development teams to waste time remediating issues in code with little material risk and minimal real-world business impact, while code that introduces material risk often ships lacking appropriate security scrutiny.
Further, 39% of development teams depend only on individual developers or development managers to prioritize and assess the severity of issues.2 When manual risk decisions are left to individual managers, results are inconsistent, unpredictable, and lack auditability.
While 43% of application security teams believe that improved DevOps integration is the most important thing to do to improve their application security program,3 there are fundamental issues in the current AppSec model that prevent the process from scaling to keep up with development velocity. These issues slow application delivery and reduce the efficacy of security program investments.
Challenges
Accelerating Code Development Delivery
While development organizations are successfully accelerating development cycles through investments in DevOps automation, the application security process lacks similar refinements, leading to the generation of more security alerts, many of which have little to no real-world business impact. This situation creates additional headwinds for development teams who are already under pressure to deliver faster. With developers releasing faster and a median ratio of full-time security resources to developer resources of 159 to 1,4 the current application security model is failing to scale.
Too Many Alerts with Too Little Impact
Figure 3. The Need for More Testing Tools Results in Too Many Alerts
How many individual application security testing tools is your organization currently using? (Percent of respondents, N=378)
Source: Enterprise Strategy Group
Inconsistent, Highly Manual Risk Assessment Processes
Lack of Context
Current Strategies Are Not Keeping Up
Shift-left
Speeding Up Existing Processes is Insufficient
The fundamental issue is the lack of automation for assessing business risk, not prioritizing vulnerability severity. It is not about which vulnerabilities to focus on; it’s about what application changes to focus on.
More DevOps Automation and Integration
AppSec Orchestration
A Multidimensional Approach to Application Security
Figure 4. The Risky Material Change Funnel
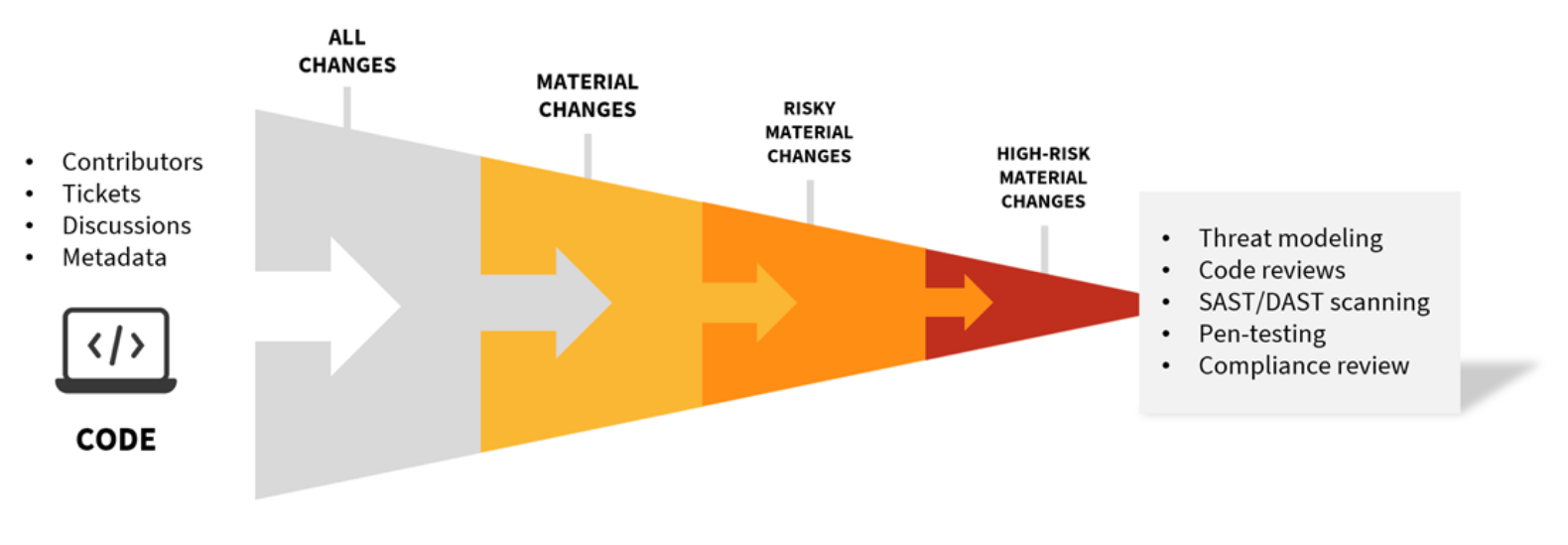
Figure 5. Aligning Security Controls to Material Business Risk

Contextual Risk Assessment

Automated Risk Classification and Security Policies
Alignment of Security Controls
Introducing Apiiro: Multidimensional Application Risk Management
The Bigger Truth
Data-driven decisions are better decisions.
This ESG White Paper was commissioned by Apiiro and is distributed under license from ESG.
1 Source: ESG Research Report, Securing Modern Application Development Environments, Dec 2020.
2 Ibid.
3 Ibid.
4 Source: Building Security in Maturity Model (BSIMM) – Version 11.
5 Source: ESG Research Report, Securing Modern Application Development Environments, Dec 2020.
6 Source: ESG Research Report, Securing Modern Application Development Environments, Dec 2020.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
