
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL VALIDATION
Protecting Your Business Backup Data from Ransomware Attacks
Secure Cloud Storage from Wasabi
By Vinny Choinski, Senior Validation Analyst; and Brian Garret, EVP Validation Services
OCTOBER 2021
Introduction
Background
Figure 1. Public Cloud Infrastructure Adoption Rate
Percent of organizations currently using infrastructure-as-a-service (IaaS), 2017-2021.
Source: Enterprise Strategy Group
Wasabi Overview
Figure 2. Wasabi Hot Cloud Overview

Source: Enterprise Strategy Group
Key protection capabilities and features include:
ESG Technical Validation
Getting Started with Wasabi
Figure 3. Access Management and Security
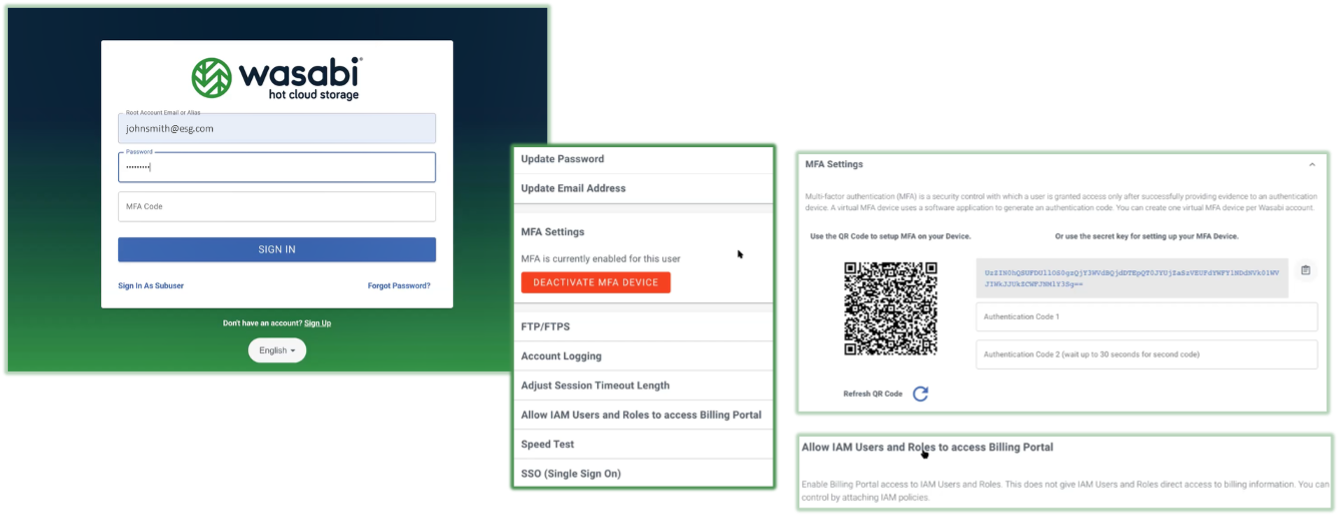
Source: Enterprise Strategy Group
Figure 4. General Bucket Management
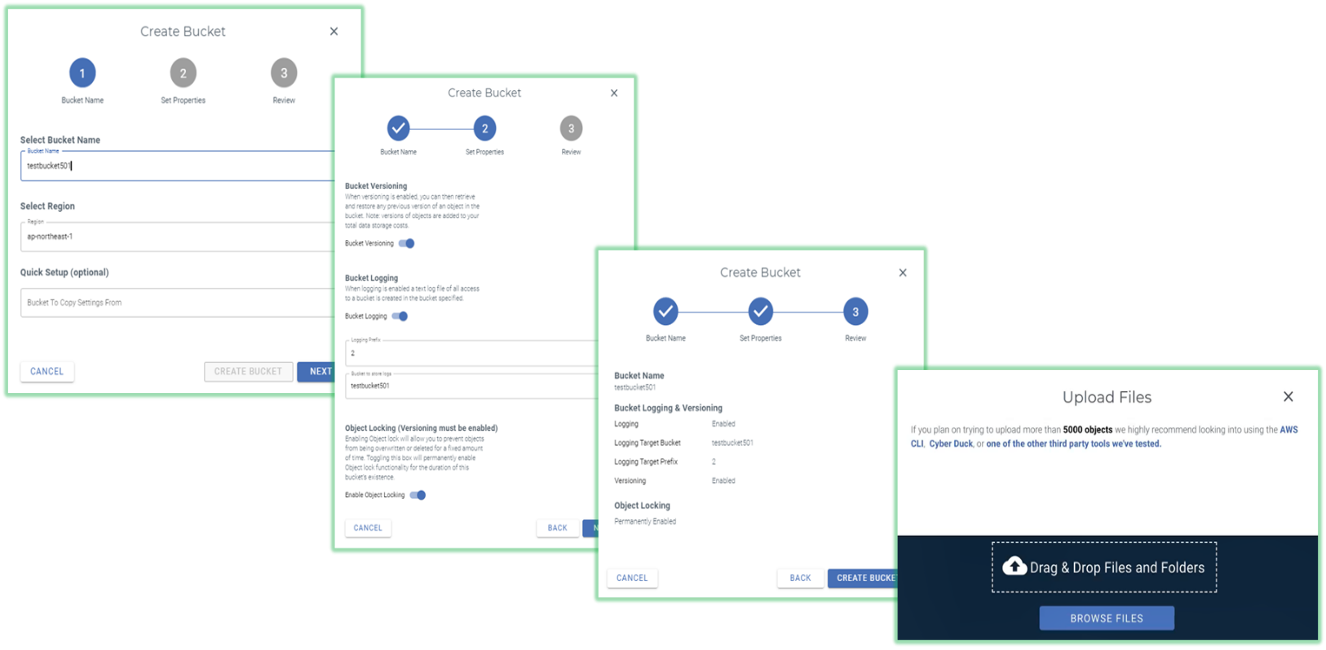
Source: Enterprise Strategy Group
Why This Matters
Wasabi Cyber-resiliency and Security Features
Figure 5. Bucket Logging, Versioning, and Public Access
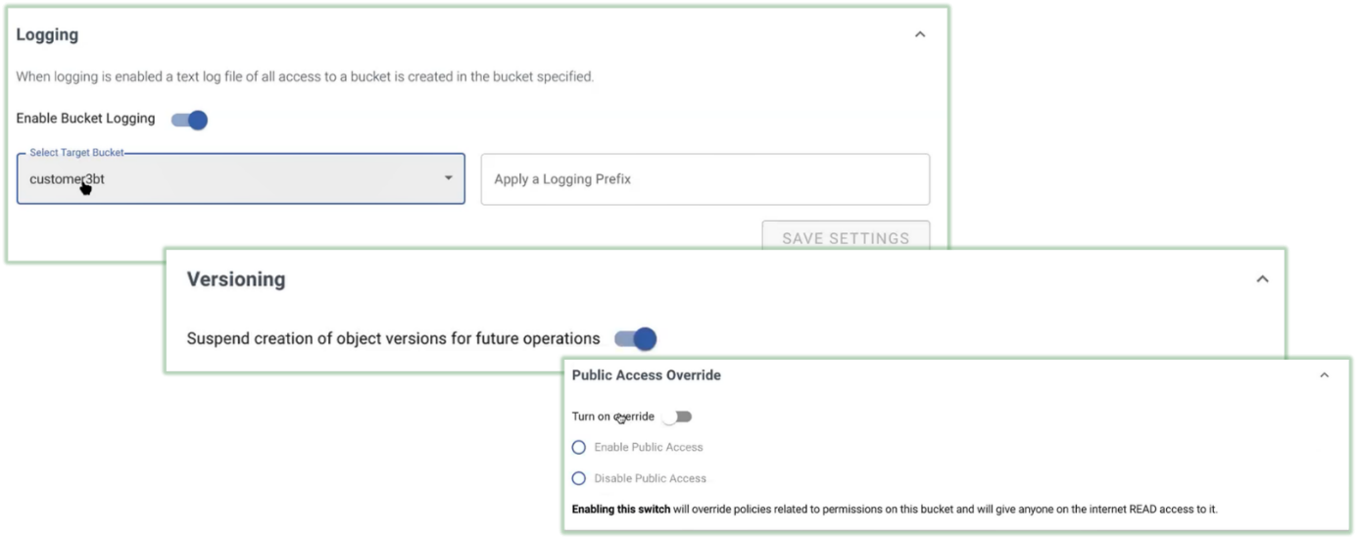
Source: Enterprise Strategy Group
Figure 6. Object Locking with Immutable Storage
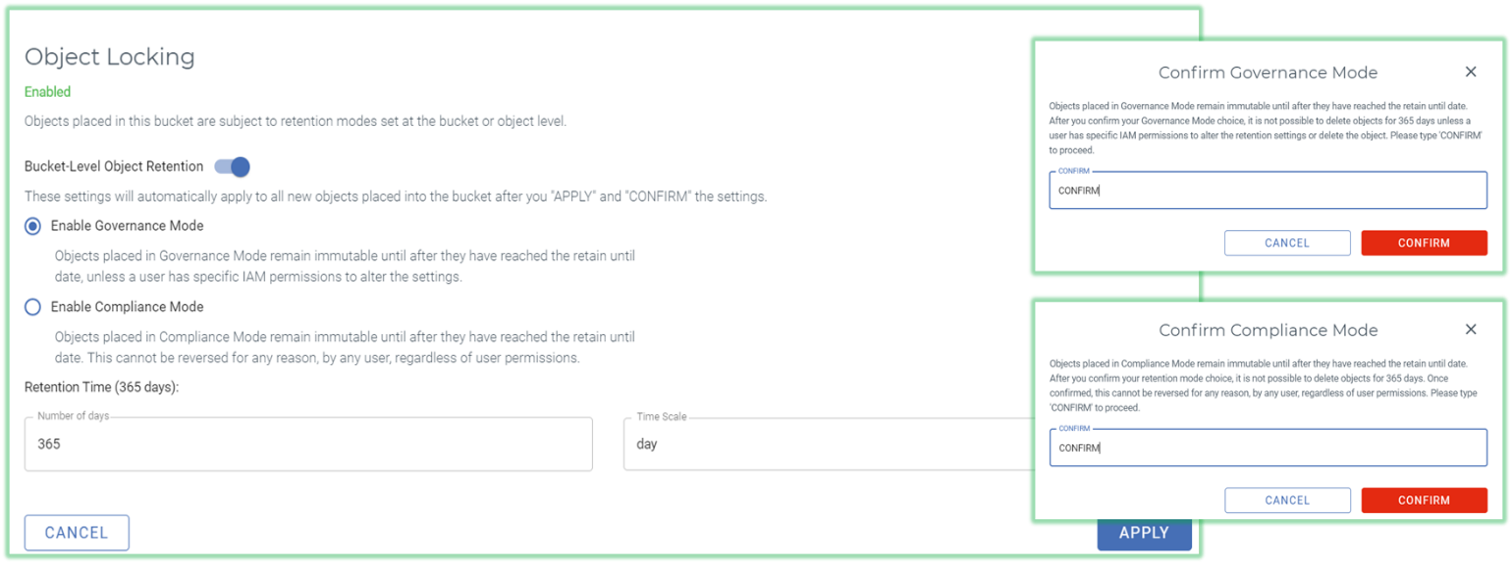
Source: Enterprise Strategy Group
Why This Matters
Third-party Data Protection Integration with Wasabi
Figure 7. Access Key Creation
Source: Enterprise Strategy Group
Figure 8. Third Party Integration – Veeam
Source: Enterprise Strategy Group
Why This Matters
The Bigger Truth
This ESG Technical Validation was commissioned by Wasabi Technologies and is distributed under license from ESG.
1 Source: ESG Research Report, Cybersecurity in the C-suite and Boardroom, Feb 2021.
2 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021.
3 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021.
4 Source: ESG Research Report, Tape’s Place in an Increasingly Cloud-based IT Landscape, Jan 2021.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
