ESG Technical Validations
The goal of ESG Technical Validations is to educate IT professionals about information technology solutions for companies of all types and sizes. ESG Technical Validations are not meant to replace the evaluation process that should be conducted before making purchasing decisions, but rather to provide insight into these emerging technologies. Our objectives are to explore some of the more valuable features and functions of IT solutions, show how they can be used to solve real customer problems, and identify any areas needing improvement. The ESG Validation Team’s expert third-party perspective is based on our own hands-on testing as well as on interviews with customers who use these products in production environments.

Introduction
This ESG Technical Validation documents evaluation of Arctic Wolf’s security operations services. We focus on how the Arctic Wolf platform integrates the organization’s existing security stack and telemetry into Arctic Wolf’s managed security operations with the goal of reducing risk and increasing efficiency.
Background
Protecting an organization from cyber-attacks has become more difficult as attackers gain sophistication and knowledge through experience, developing stealthy attacks that target key personnel in weakly protected organizations. These attackers threaten organizations with automated tools that reduce their cost and effort and enable them to target a larger population at scale.
Organizations face additional challenges securing their infrastructure due to the rapidly changing and evolving threat landscape, the growing attack surface as organizations shift to support mobile and remote workers, and the increased volume of alerts. These challenges are exacerbated by the global cybersecurity skills shortage: according to ESG research, organizations have been facing a shortage of cybersecurity skills since 2013, and almost half (48%) of organizations rank cybersecurity as one of their most critical skills shortages for 2021 (see Figure 1).1
Figure 1. IT Skills Shortage
In which of the following areas do you believe your IT organization currently has a problematic shortage of existing skills? (Percent of respondents, N=654, multiple responses accepted)
Source: Enterprise Strategy Group
The skills shortage makes it harder for organizations of any size to appropriately staff cybersecurity teams, and this is driving many organizations to turn to third parties. Indeed, according to ESG research, 73% of organizations that reported a problematic shortage of cybersecurity skills said they would increase their use of third-party security services to cope with that shortage.2
Arctic Wolf Managed Security Operations
Arctic Wolf is a managed security operations services provider with a mission of ending cyber risk. Believing that security breaches are rooted in operational failures rather than simply product failures, Arctic Wolf aims to help organizations become so effective at security operations that both the risk and impact of a cyber-attack are minimized far beyond what an organization would be able to achieve on its own.
To achieve this goal, Arctic Wolf has developed the cloud-native Arctic Wolf Platform to provide security operations as a concierge service, including managed detection and response (MDR), managed risk, and managed cloud monitoring. Arctic Wolf delivers these services using a concierge security team of highly trained and experienced security experts that work as an extension of the organization’s internal teams to provide continuous monitoring, detection, and response, as well as ongoing risk management. This helps organizations proactively monitor and protect their infrastructure while strengthening their security postures.
The Arctic Wolf platform implements a security operations and analytics platform architecture (SOAPA) to deliver security orchestration, automation, and response. Arctic Wolf designed the platform to meet their needs as a concierge security operations services organization, integrating security operations and customer management to reduce risk and increase both Arctic Wolf and customer efficiency.
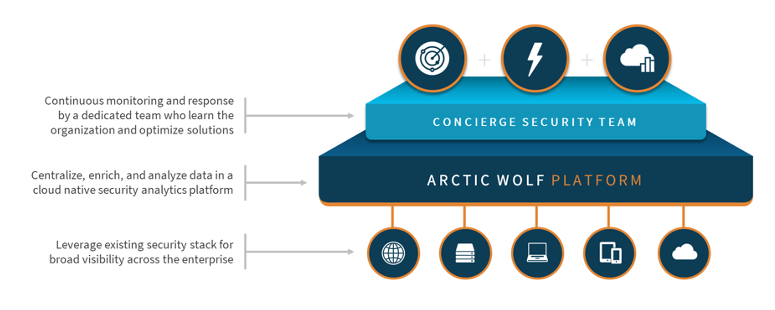
The platform enhances the customer’s existing security stack to obtain broad visibility across the entire cloud and on-premises infrastructure. The platform becomes the centralized store for all security logs and telemetry. This helps the organization meet compliance requirements and enables Arctic Wolf to enrich the data with additional context from more than 30 sources of security data and threat intelligence. Across the entire customer base, the platform collects and analyzes more than 135 billion events every day.
Providing concierge security operations means that Arctic Wolf is responsible for reviewing and resolving security alerts. Arctic Wolf sends only those alerts that require action from the organization’s infrastructure teams to the customer. Thus, daily, across the Arctic Wolf customer base, millions of security data observations are enriched and analyzed, reducing them to thousands of security alerts. Arctic Wolf’s internal security analysts evaluate and resolve most alerts. This translates into customers having to respond to just a few actionable security events. Each customer is assigned a dedicated concierge security team that works hand-in-hand with the customer, providing round-the-clock coverage and guided response to triage alerts, stop threats, prevent damage, find root causes, validate remediations, and collaborate with the customer to continuously improve the organization’s overall security posture.
The concierge security team is also designed to work with the customer to manage and reduce risk. Managed risk efforts are focused on identifying, categorizing, and hardening risky software, assets, and accounts. Activities include cloud security posture management (CSPM), network and host-based vulnerability assessments, dark web scanning, account takeover risk assessment, and security controls benchmarking. The concierge security team can help the customer develop and manage risk reduction project plans.
Customers can add managed cloud monitoring to their managed security operations. This service identifies exposed cloud platforms and accounts, monitors IaaS services for configuration risks, monitors SaaS apps for key threats and indicators of compromise, and streamlines cloud security with cloud experts and concierge deployment and management.
ESG Technical Validation
Arctic Wolf provided access to a demo environment based on anonymized customer data, enabling ESG to evaluate the customer portal of the Arctic Wolf platform. We were also provided access to the platform’s internal backend, which helped ESG evaluate how Arctic Wolf security professionals operate and how the portal increases operational efficiency.
Increase Efficiency With The Arctic Wolf Customer Portal
The Arctic Wolf customer portal dashboard, shown in Figure 2, is informational, providing an at-a-glance summary of the organization’s security posture, along with a summary of Arctic Wolf activity. The security score ranks the security posture relative to similar organizations in the industry. Arctic Wolf designed the score to drive security posture conversations—it is meant to be a starting point for the customer’s journey to increased security and decreased risk.
Other information includes the number of online endpoints (obtained via the Arctic Wolf agent) and security telemetry network sensors in the customer’s environment, as well as a map showing the countries generating the most threats and attacks targeting the organization.
Demonstrating how Arctic Wolf’s internal security team reduces the customer workload, the portal shows that the team analyzed and investigated 569 different data points, most of which were taken care of without having to involve the customer. Ten incidents required customer action, and these are tracked as ticketed incidents in the customer portal.
Figure 2. Customer Portal Dashboard
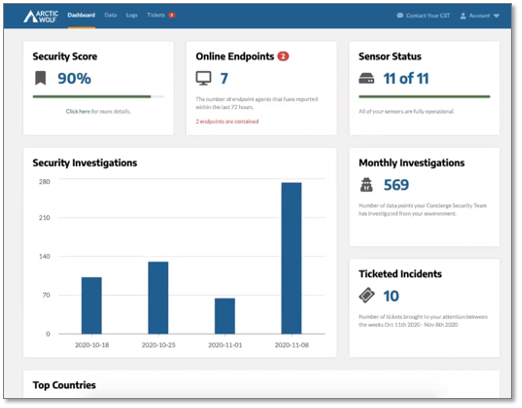
Source: Enterprise Strategy Group
Arctic Wolf alerts customers to actionable incidents using a ticketing system. The platform creates a new ticket for each incident and alerts the customer by email and other methods, as dictated by the customer. As part of the white-glove customer onboarding process, Arctic Wolf and the customer jointly map out custom alerting and escalation procedures for various types of incidents. For example, some customers may want instant notification via email for every type of incident, whereas others may want to receive an email for everything, and an immediate phone call for ransomware. The notification and escalation configuration is captured and automated in the customer directory section of the platform’s backend.
Customers can review all open incidents through the ticketing interface, shown in Figure 3, which provides searchable and filterable incident summary and status. Clicking on a ticket provides incident details, including description, affected systems, and suggested remediation. Customers can provide status updates and feedback, and all activities and comments are captured in the incident ticket. Customers can also speak directly to the concierge security team to better understand the issue and get additional help.
Figure 3. Ticketing Interface
Source: Enterprise Strategy Group
While Arctic Wolf didn’t design the portal to be a comprehensive SIEM interface, customers can access flow data and search raw log data through the portal. This increases customer efficiency by enabling customers to quickly access commonly desired information without having to call the concierge security team.
Searching Logs
A university routinely uses the Arctic Wolf portal’s log search function to validate copyright infringement notifications and identify students that are potentially illegally downloading copyrighted material.
Using the interface, the customer can search and filter to obtain critical information. Should the customer need more information, they can click on a button to automatically generate a request to the concierge security team that includes the search parameters, simplifying the efforts of the Arctic Wolf team (see Figure 4).
Figure 4. Logs and Traffic Flows
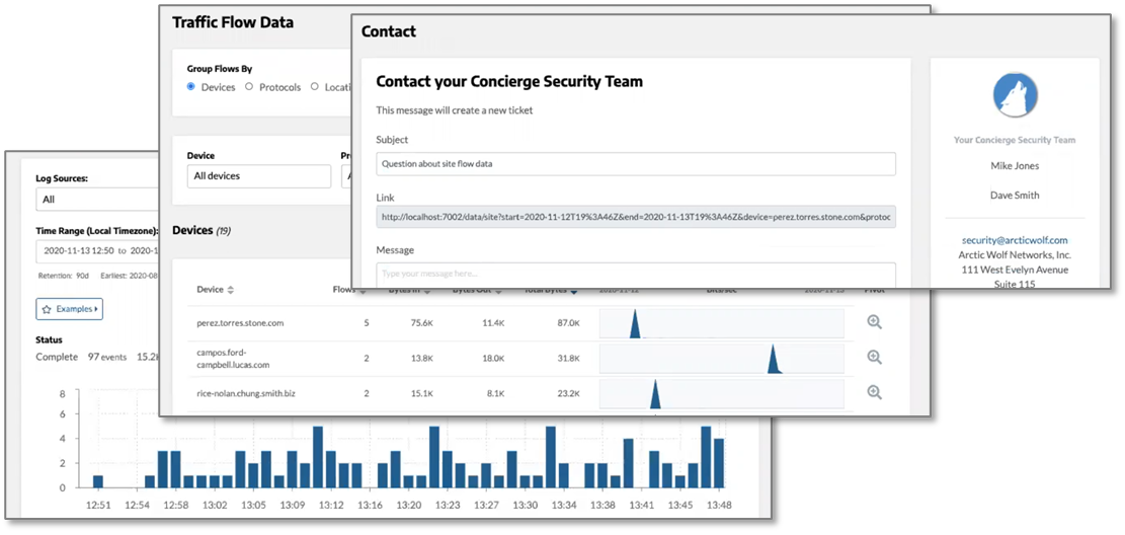
Source: Enterprise Strategy Group
Arctic Wolf can generate weekly, monthly, and additional routine informational reports. These reports help the customer understand the status, activity, and value of the Arctic Wolf service. Arctic Wolf includes more than 100 reports covering cloud, external scans, routine activity, Active Directory lockouts, and more. .
Value of Reports
Arctic Wolf’s reports for a customer showed spikes in phishing incidents every three months. This sparked a conversation with the director of IT and Arctic Wolf discovered that the customer was including executive email addresses in its quarterly financial reports. The correlation to phishing activity helped the organization justify an investment in a cloud-based identity provider to increase security and reduce risks from phishing.
Reporting for another customer revealed a large amount of FTP traffic to numerous internal FTP servers. Arctic Wolf and the customer jointly developed and implemented a plan to migrate FTP activities to a more secure file transfer method and eliminate the FTP servers from the environment.
Figure 5. Reports
Source: Enterprise Strategy Group
WHY THIS MATTERS
According to ESG research, three quarters (75%) of organizations believe that their infrastructure has become more complex in the last two years. And this increasing technology complexity extends to cybersecurity, resulting in a greater attack surface, more sophisticated attacks, and more risks to the organization. With the current cybersecurity skills shortages, organizations cannot hire their way to reduced risk.
ESG validated that Arctic Wolf managed security operations services and the Arctic Wolf portal increase organizational efficiency. Arctic Wolf investigates most issues, drastically reducing the number of incidents the organization must investigate and reducing alert fatigue. The customer portal simplifies incident investigation tracking and provides at-a-glance security health and status information, ensuring that the customer is constantly aware of its current security posture.
The dedicated concierge team collaborates with the customer’s security and IT teams to learn the customer’s business. Knowing what matters and what doesn’t matter for the customer ensures that the concierge team helps reduce risk and optimize the customer’s security posture.
Reduce Risk With Arctic Wolf Managed Detection And Response Service
ESG reviewed the concierge security team’s internal interface to the Arctic Wolf platform to help us understand how Arctic Wolf reduces customer risk while increasing both its own and its customers’ operational efficiency. The backend interface is for Arctic Wolf’s internal use and is designed to streamline the customer’s experience.
Figure 6 shows an example of an Arctic Wolf security analyst dashboard used by one team for managing risk. The dashboards are customizable to meet the needs of each analyst performing their specific security tasks (threat hunting, investigation, remediation, etc.), and over time the security analysts have developed and customized hundreds of their own dashboards to ensure they maximize their productivity.
Figure 6. An Example of a Security Analyst Dashboard
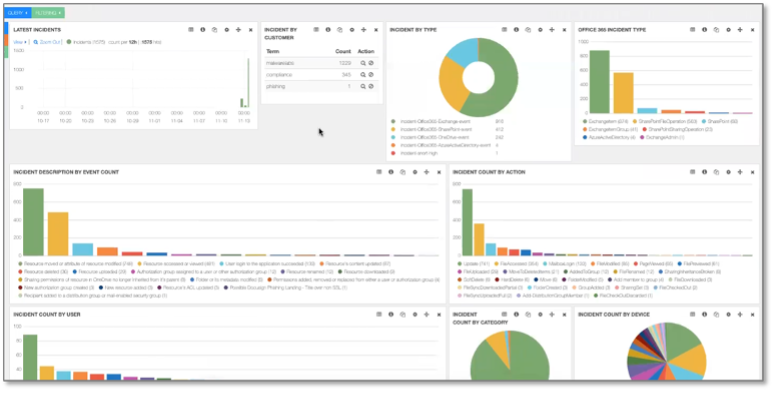
Source: Enterprise Strategy Group
The platform provides a wealth of information and environmental data to an Arctic Wolf security analyst investigating an incident. Figure 7 shows an investigation of a possible DocuSign phishing landing page with the page URL, the user and device information correlated from AD, DNS, DHCP logs, and more. The incident focus includes a customized playbook, guiding the security analyst through the investigation. Should the security analyst decide that the customer needs to act on the incident, the analyst can automatically create an incident ticket and alert the customer.
Figure 7. Incident Focus
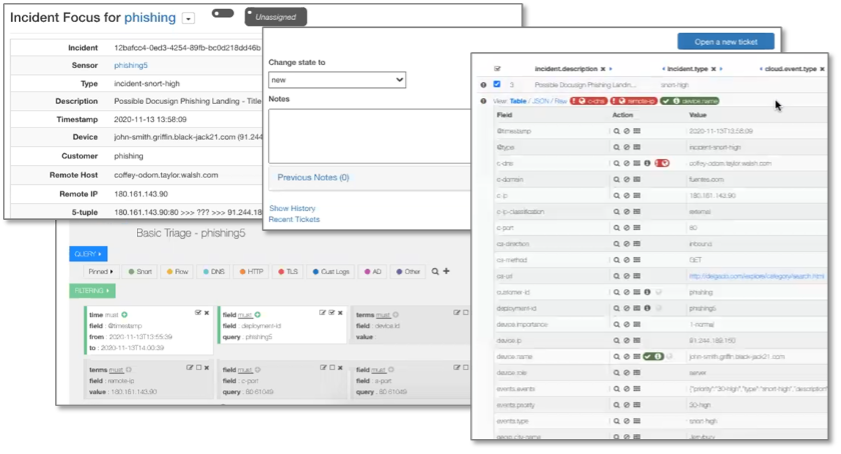
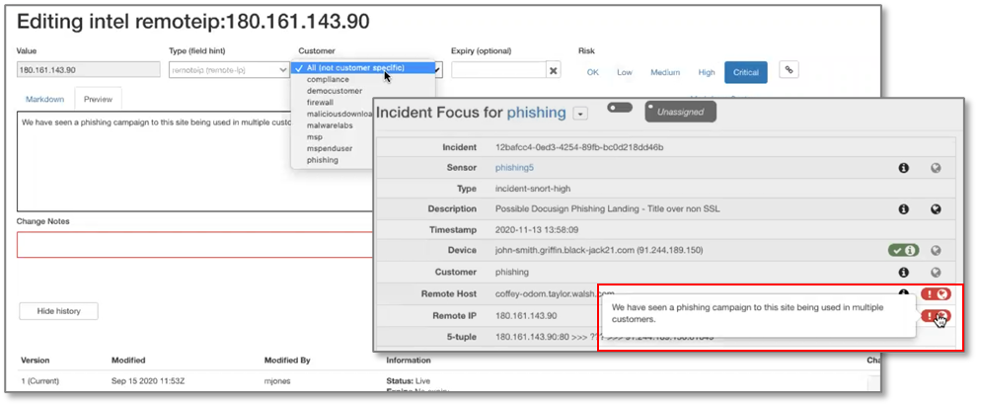
After deciding that the DocuSign landing page was a legitimate phishing attempt, the security analyst annotated the IP address with additional information, as shown in Figure 8. The concierge security team assigned to a customer can also share information, such as the fact that the customer normally does not allow logins from international locations, but the CEO is on vacation for a week in the Bahamas, so logins by the CEO from this location should be allowed and should not be considered a breach.
This formalized method of information and intelligence sharing spans all customers and feeds into all parts of the Arctic Wolf business, ensuring that all members of the team have immediate access to relevant data without having to search in daily notes or logs, increasing effectiveness and efficiency.
Figure 8. Formalized Internal Intelligence and Information Sharing
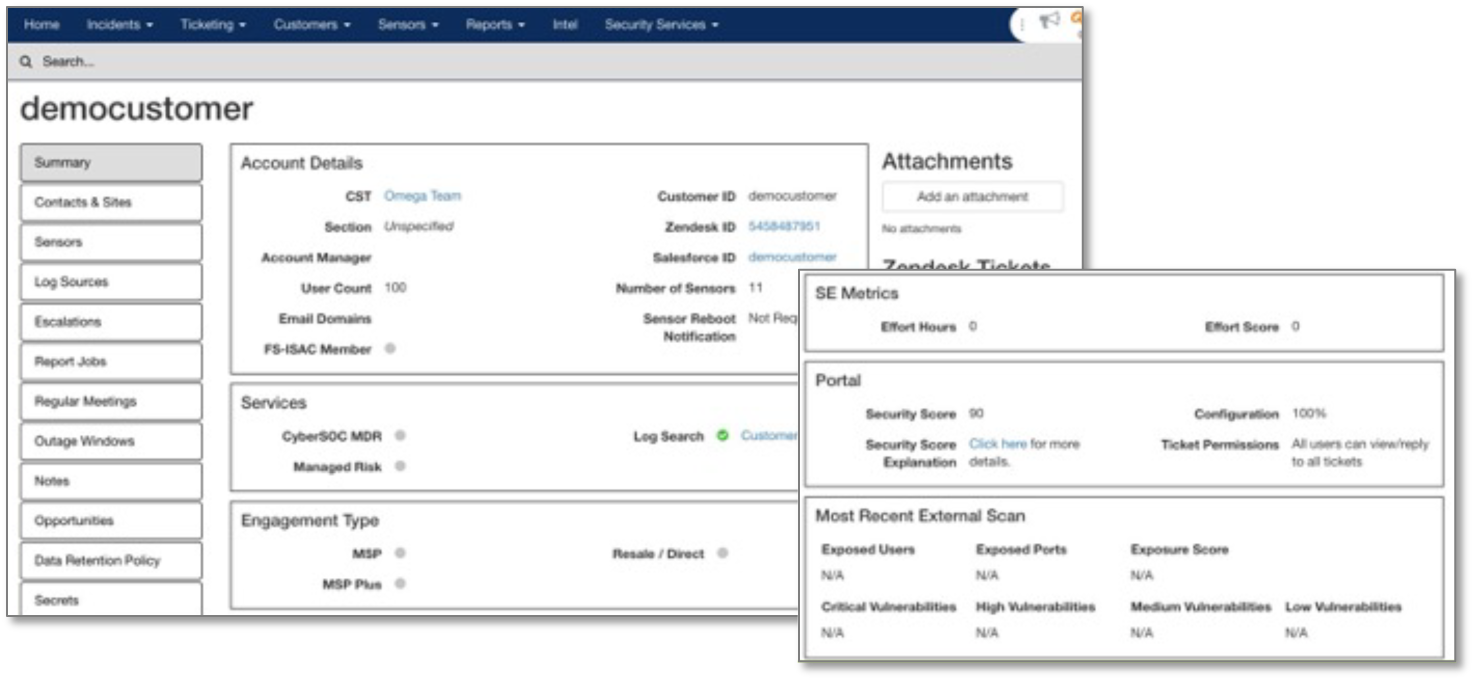
The platform incorporates a complete customer relationship management (CRM) system developed from the perspective of the customer. The CRM captures with whom Arctic Wolf is engaging, as well as their role, location, and other critical information.
Figure 9. Internal CRM
Arctic Wolf captures the incident-type specific notification and escalation chain in the platform and automatically populates incident tickets with the correct notification information. Thus, the platform prevents the wrong person from being notified, or, worse, the correct people from not being notified in a timely manner about critical incidents.
Figure 10. Formalized Escalation Chain Integrated with Ticketing
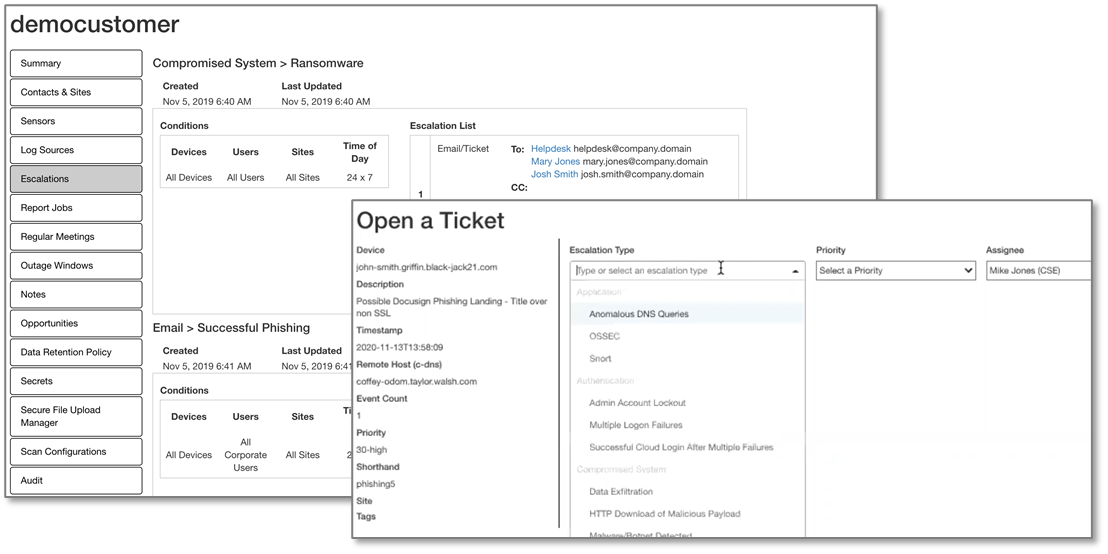
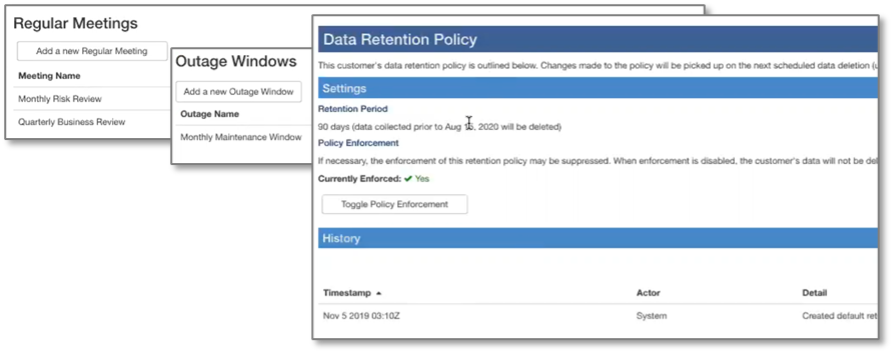
Other critical information such as regular meeting schedules, outage windows, data retention policies, shared secrets, and more, are captured in the platform, making the platform the source of all truth and knowledge about a customer.
Figure 11. Formalized Meetings, Outage Windows, Data Retention
WHY THIS MATTERS
It is cost-prohibitive for managed security services providers to staff security personnel in a one-to-one ratio with their customers. These service providers must increase security analyst, customer support, and management efficiencies to be able to support customers at scale.
ESG validated that Arctic Wolf has developed internal tools, processes, and techniques to increase its operational efficiency. The internal portal includes hundreds of customizable dashboards optimized by security analysts to maximize their productivity. Arctic Wolf has integrated a custom CRM with automated notification and escalation, ensuring the right people are notified at the right time. The tools and procedures formalize and capture knowledge sharing, meetings, outage windows, data, and more, making the portal the centralized location of all truth and knowledge about each customer.
With increased operational efficiencies, Arctic Wolf security analysts can focus on investigating and resolving alerts. Only those alerts requiring customer action are sent to the customer. This reduces customer risk and alert fatigue, ensuring that customers quickly take action on critical incidents before attackers can wreak havoc.
Collaborate To Manage And Reduce Risk
Arctic Wolf designed the risk management portal to foster collaboration between the customer and the concierge security team in their joint efforts to identify and reduce risks in the organization’s infrastructure. Arctic Wolf’s approach to risk management is to extend beyond simply monitoring the environment to helping the customer understand remediation efforts, risks, level of effort, and return on investments. Thus, the risk management portal is used by both the customer and the concierge security team.
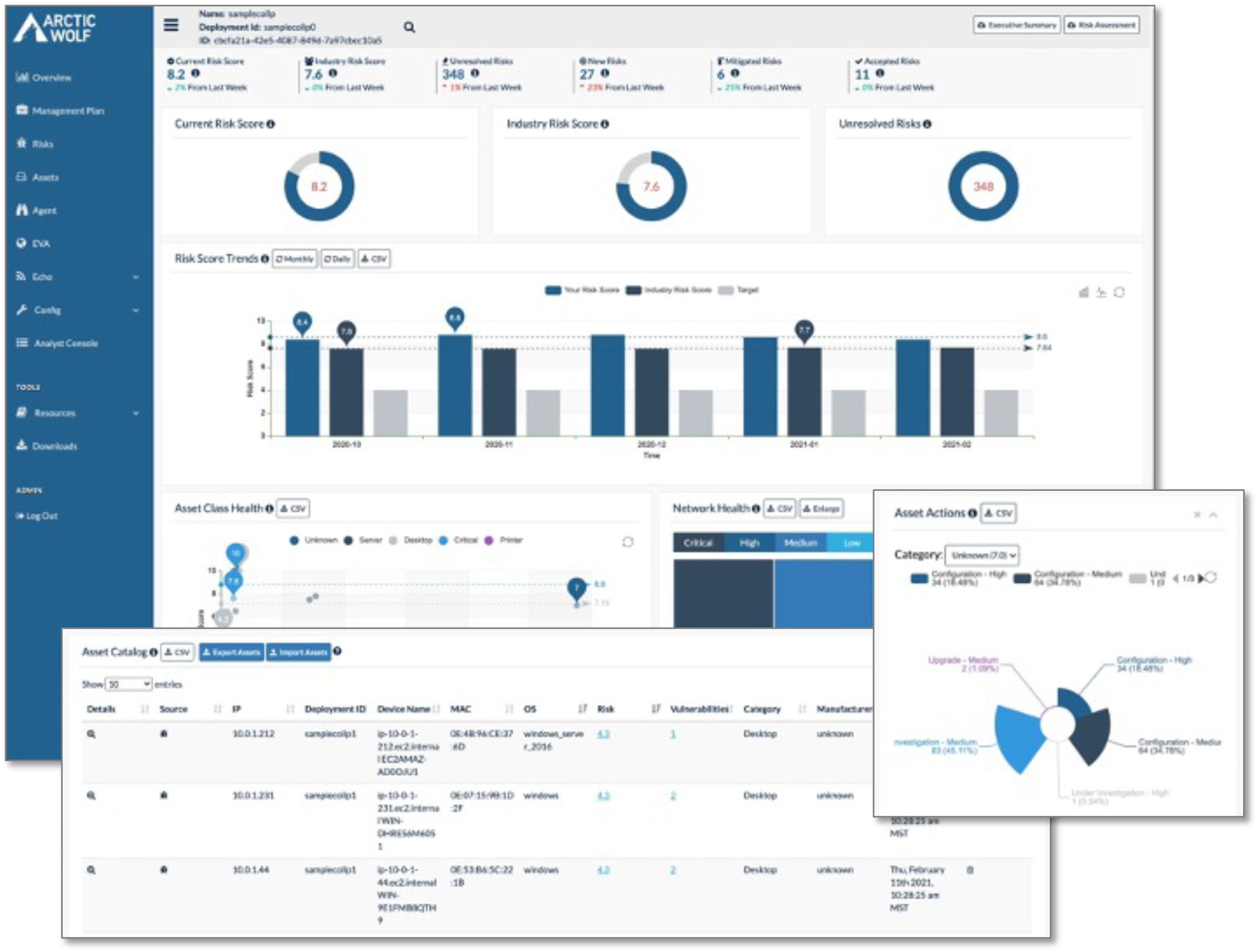
The risk management dashboard provides all users with at-a-glance understanding of the current risk management status. As shown in Figure 12, the dashboard presents the organization’s risk score and risk score trends, enabling the customer to benchmark its level of success in reducing risk compared to similar organizations in the same industry. Customers can work with the concierge security team to classify systems, networks, workloads, and other assets. The security health of these assets is also shown in the dashboard, helping customers understand their current risk status. Users can view additional metrics and data to help them better understand and triage risks.
Figure 12. Risk Management Dashboard
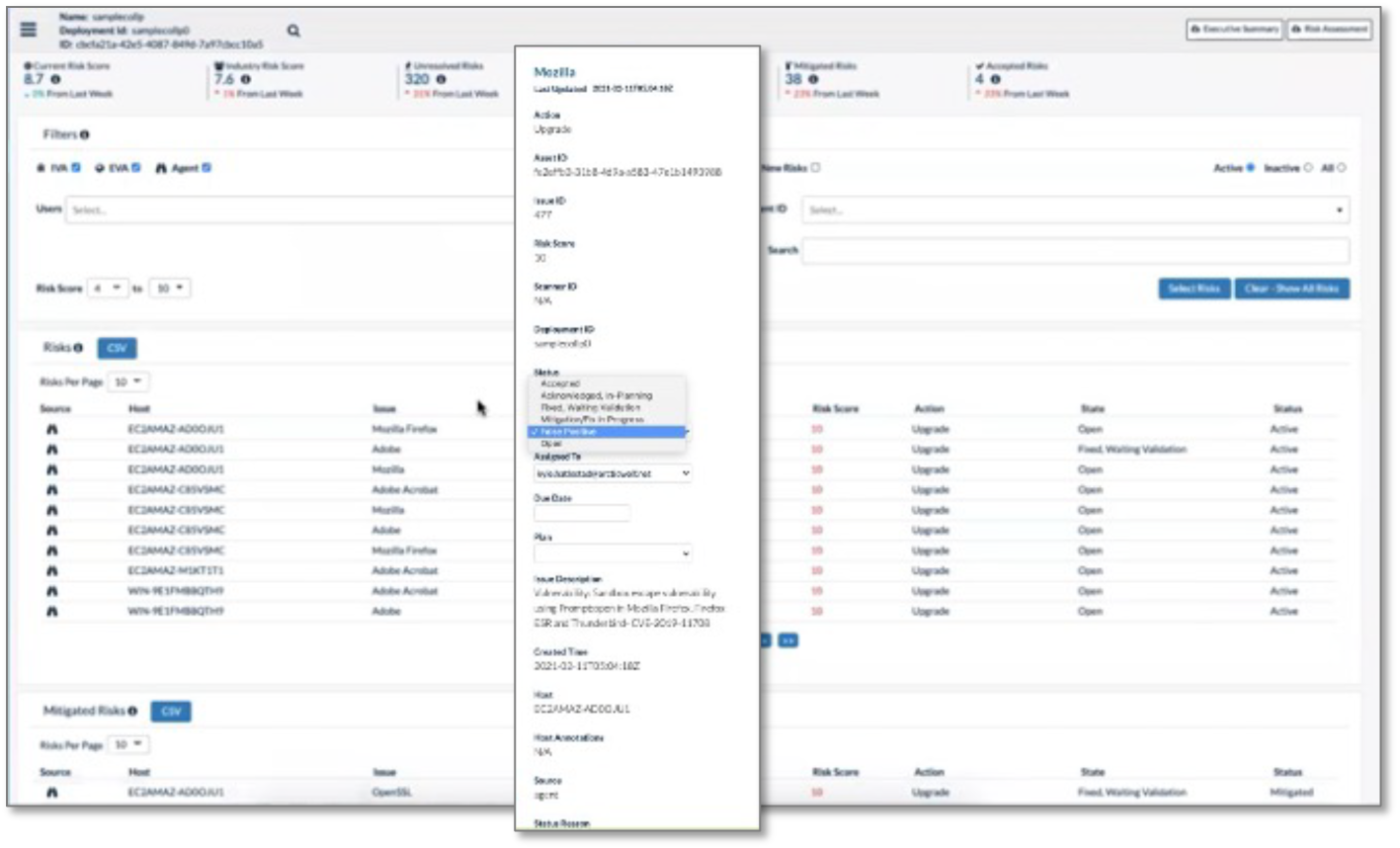
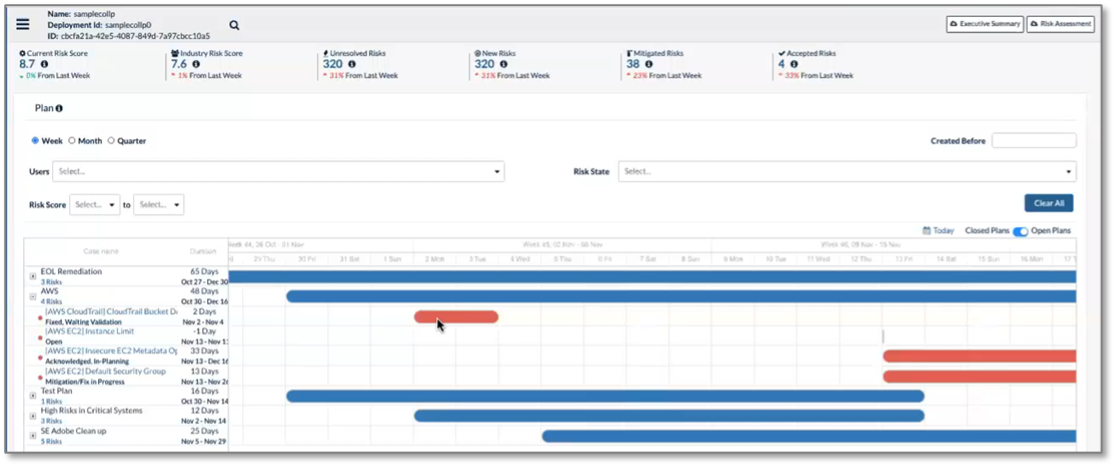
Arctic Wolf uses both its own and the customer’s network; external and agent-based risk scanners; threat intelligence; and other techniques to identify risks such as vulnerabilities, dark web alerts, CSPM problems, and more, in the infrastructure. Customers and concierge security team members can use the risks section of the risk management portal to view the list of detected risks on assets, as shown in Figure 13. The portal supports searching and filtering and users can update risk status directly from the list of risks. When a risk has been remediated, the user can change the status to Mitigation/Fix in Progress, which means that the remediation will be verified at the next scan cycle.
Figure 13. Detected Risks
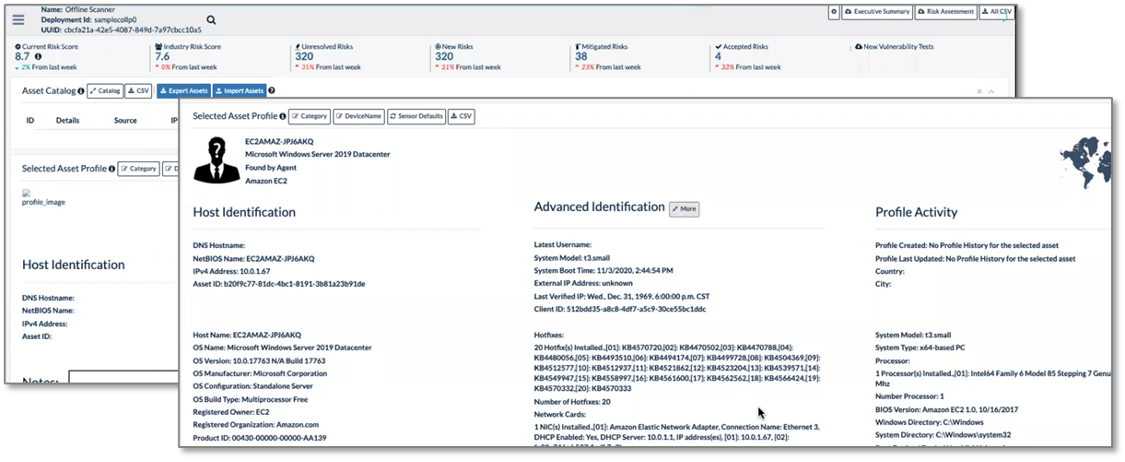
Clicking on an entry in the list displayed the details of the asset, including scan history, networking configuration, software packages, hotfixes, task list, and more, as shown in Figure 14. This information helps both the customer and the concierge security team understand asset health and state, hunt for active threats, and triage and prioritize risk and remediation efforts for maximum ROI.
Figure 14. Asset Details
Arctic Wolf’s goal is to advance the customer’s security journey towards ending cyber-risk. Instead of just providing a list of vulnerabilities, the concierge security team collaborates with the customer to streamline and simplify the often daunting risk mitigation effort. The result of this effort is a set of risk remediation project plans and schedules that are tracked directly in the risk management portal, as shown in Figure 15.
Customers can also create and track their own plans. Each plan can include rules defining the assets or risks that will be addressed. Thus, plans are automatically updated as assets are added or changed, risks are mitigated, and new issues are discovered.
Arctic Wolf reviews with the customer their remediation plans and efforts during monthly and quarterly status meetings and these plans help the customer understand and reduce risk over time.
Figure 15. Risk Remediation Management Planning and Scheduling
WHY THIS MATTERS
Using scanning tools, threat intelligence, and other sources, organizations can quickly compile very long lists of vulnerabilities, CSPM problems, and other risks. The challenge isn’t in finding these risks, but in triaging, prioritizing, and remediating them.
ESG validated that Arctic Wolf uses its risk management platform and collaborates with the customer to help the customer on its journey towards ending cyber-risk. The risk management platform helps both the customer and the Arctic Wolf concierge security team understand the risks to the customer’s assets. Working together, both teams develop plans and schedules to remediate issues. The plans are captured in the portal and are automatically updated as assets are added or changed, and issues are addressed. Arctic Wolf reviews the mitigation plans and schedules during routine monthly and quarterly meetings, ensuring that customers stay on track and continue reducing risk over time.
The Bigger Truth
Despite the critical lack of cybersecurity skills, organizations turning to third parties for cybersecurity services are seeking much more than staff augmentation. They are looking for a mentor that can help them strengthen understanding of and participation in security as a “team sport,” simultaneously helping with strategic issues, such as mitigating the increasing complexity of security within hybrid and multi-cloud architectures and tactical issues, such as the overwhelming volume of security alerts and the day-to-day efforts of detecting and responding to security incidents and addressing vulnerabilities and other risks.
ESG validated that:
- Dedicates a concierge security team to each customer; this team learns the customer’s business and IT environment and what security issues are most important or unique to the customer.
- Leverages the customer’s existing technology stack for security control and telemetry.
- Investigates all issues, only involving the customer for security incidents that require customer action, reducing the number of customer incident investigations.
- Automates incident alert and escalation, ensuring customers rapidly resolve critical issues and reducing alert fatigue.
- Collaborates with the customer, developing plans and schedules for mitigating vulnerabilities, CSPM issues, and other risks with the goal of ending cyber-risk.
The Arctic Wolf platform automates activities, provides status, and is the central repository of all data and knowledge regarding each customer. The platform and Arctic Wolf’s collaborative efforts help customers increase operating efficiencies and reduce risks.
ESG’s validation of Arctic Wolf’s managed security operations services and the Arctic Wolf Platform was based on testing in a controlled environment. Due to the many variables in each production data center, it is important to perform evaluation in your own environment to validate the viability and efficacy of any solution.
If your organization is considering engaging with service providers to help manage security operations, ESG believes that you should consider how Arctic Wolf can help you on your journey to driving risk to zero while increasing the operating efficiencies of your technology and security teams.
We take the operational approach to cybersecurity
DOWNLOAD PDF REPORT
This ESG Technical Validation was commissioned by Arctic Wolf and is distributed under license from ESG.
1 Source: ESG Master Survey Results, 2021 Technology Spending Intentions Survey, Dec 2020.
2 Source: ESG Master Survey Results, 2020 Technology Spending Intentions Survey, Jan 2020.
3 Source: ESG Master Survey Results, 2021 Technology Spending Intentions Survey, Dec 2020.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.

