ABSTRACT
This ESG Technical Review documents ESG’s evaluation and analysis of Axis Security, and how the Application Access Cloud platform helps enterprises implement zero-trust-based access to cloud and on-premises resources for all types of employees, third parties, and devices.
The Challenges
The pandemic triggered a massive shift from office- to home-based workers. Now that many people are working from home and will likely continue to do so, enterprises need to provide secure access easily and cost-effectively. However, according to ESG research, 66% of organizations say securing the network at the edge is more difficult than it was two years ago. The threat landscape is the top reason for this, followed by distributed users and mobile devices, the need to implement policies and security tools, and IT staff shortages (see Figure 1). In addition, secure access is difficult due to the complexity of disparate access systems such as VPNs, VDI, and CASB; requirements for consistent data security; the expansion of IT across on-premises and cloud data centers; and the myriad of applications and employee-owned devices.1
Figure 1. Threats Remain the Biggest Challenge for Network Security at the Edge
You indicated that network security at the edge has become more difficult over the last two years. In your opinion, which of the following factors have been most responsible for making network security management and operations more difficult? (Percent of respondents, N=241, three responses accepted)
Source: Enterprise Strategy Group
Current remote access methods can be expensive and difficult to deploy, manage, and support; and may not provide visibility into potential malicious activity. Many, like virtual private networks (VPNs), require endpoint agents or difficult-to-scale hardware and connect users to an organization’s networked infrastructure instead of to specific resources. This increases network exposure and the risk of compromise—access to the network is the attacker’s holy grail. When several solutions are deployed or there are too many concurrent users, performance may decrease and negatively affect productivity and user experience. Software-defined perimeters (SDPs), another form of network access, can provide secure connectivity, but adoption remains low, with only 9% of organizations using SDP extensively.2
Enterprises need a solution that replaces traditional remote access methods to make it simpler for them to provide access reliably and securely at the edge.

The Solution: Axis Security
Axis Security designed the Application Access Cloud platform as a cloud-native service for securely connecting employees and third parties, as well as their devices to resources and applications in the cloud or on-premises. The platform requires no network changes or endpoint agents, which makes it quick and easy to get running for any number of users. To reduce the threat surface and risk of compromise, Axis users never actually touch the network, host, or application. Instead, Axis isolates applications from users, networks, and the internet by brokering and sanitizing user requests.
Built on zero-trust principles, the solution enables granular control of application permissions. Requests to connect to an application are routed through the platform where they are authenticated against an individual’s policy settings and encrypted. The platform replaces traditional one-time authorizations with continuous authorization using contextual awareness (location, device type, history, and so on), security protocol analysis, and adaptive authentication that evaluates and changes permissions and even policies in real time. All this happens behind the scenes, invisible to users, although every individual action, such as viewing a page or downloading a file, is recorded and authorized separately.
Organizations can deploy secure access at the edge, even for temporary users, with benefits that include:

Secure, agentless access— Axis secures HTTP/S, RDP, SSH, DB, Git, Kubernetes, and other protocols without requiring an agent, simplifying third-party access and BYOD initiatives.
Centralized management— users, applications, and policies are managed through the cloud console. Unlike network layer solutions, Axis enables granular control over user activities at the application level.
Secure TCP and UDP apps— organizations can ensure secure TCP and UDP communications, including VOIP, peer-to-peer, and server-initiated scenarios.
Continuous monitoring and visibility— organizations can detect and investigate potential security issues more rapidly compared to normalizing logs from disparate systems.
Secure networks— Axis operates at the app layer, isolating applications and preventing users from directly accessing the network.
Simplified cloud migration—existing security policies can be used to enable secure access to applications wherever they are located, with no need to reconfigure a VPN or network.
Secure transactions— The platform stops malformed requests before they reach applications. Device posture checks and integration with EDR and SIEM or SOAR systems supports incident response.
Scalability— the platform scales automatically as traffic increases, without network reconfiguration.
ESG Tested
ESG performed an evaluation of Axis Security, focusing on effectiveness, flexibility, and ease of use for both end-users and administrators.
ESG began by taking on the role of a typical end-user who needs remote access to corporate applications. After authenticating using a single-sign-on service, we logged in to the Axis Security user portal. As shown in Figure 2, the user portal provided secure access to preconfigured corporate applications. Clicking on an application icon started a new remote access session to the app. In addition to traditional and web-based applications, Axis provides zero-trust administrative SSH access with one-time passwords and logins. Table 1 lists the types of applications supported by Axis Security.
Figure 2. Axis Security User Portal
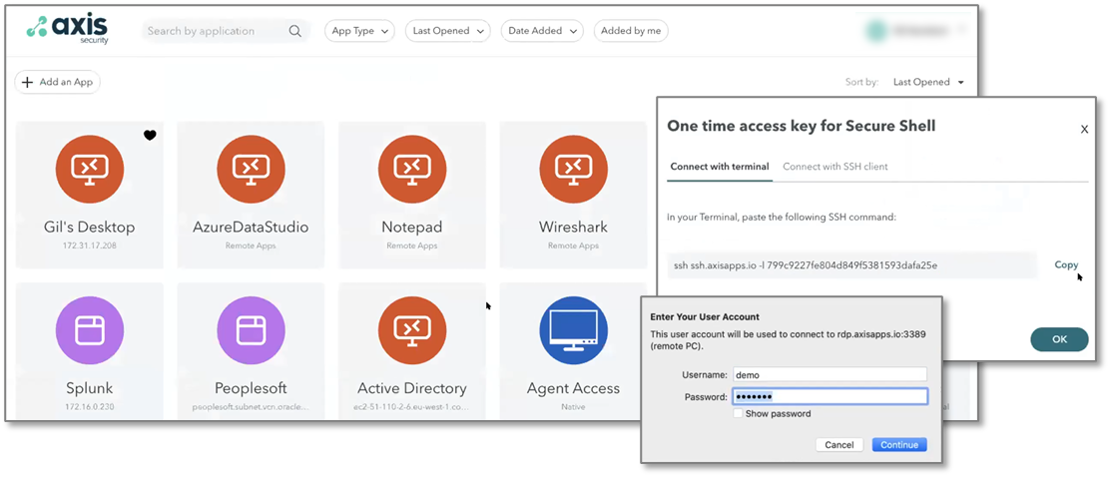
Table 1. Types of Applications Supported by Axis Security.
| Web Apps (HTTP/HTTPS) | Remote Desktop (RDP) |
| Admin Access (SSH) | Git Repositories |
| Databases | Kubernetes |
| Thick Client Apps | TCP Apps |
| UDP Apps | VOIP |
| Video | Peer-to-peer networking |
| Server-initiated | SaaS |
| End-to-end Encryption | Isolated Network Segments |
Source: Enterprise Strategy Group
Axis Security can automatically secure peer-to-peer and VOIP applications. This provides secure access to soft phones and other popular communication apps for employees and enables administrators to control access and log activity. ESG observed a VOIP soft phone connected to the network when we logged in to Axis Security and we successfully placed a call between the soft phone and our mobile phone (see Figure 3).
Figure 3. Secure Peer-to-peer VOIP

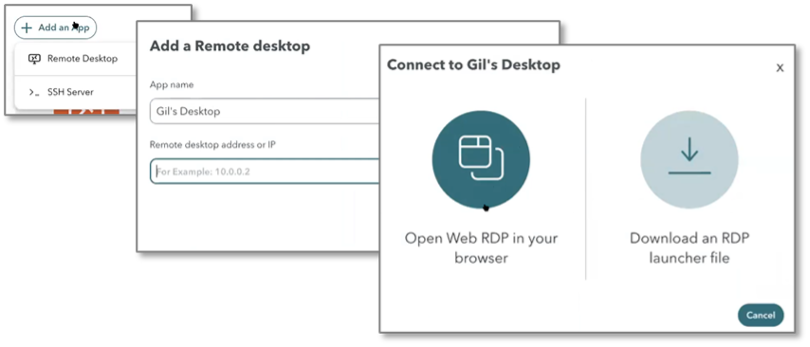
Users that are trusted enough can add their own apps. We added remote desktop access and administrative access to a remote system with the Add an App button (Figure 4). After providing the remote system name or IP address, we initiated both web-based and native-client RDP access. Using a packet sniffer (WireShark), we observed that we had a secure remote desktop connection: communication between the RDP client and server was encrypted, and no communication from the server to other systems was observed at the client.
Figure 4. Self-service Zero-trust Secure Connection to Remote Desktop and SSH
WHY THIS MATTERS
Why This Matters
Data and cloud security are the biggest obstacles to secure access: 34% of organizations said that one of their biggest issues securing employee access is the complexity associated with the increasing use of cloud-based resources, 30% said they face difficulty in addressing secure access from employee-owned devices, and 26% said they are challenged by employees circumventing corporate security controls.3
ESG validated that Axis Security simplifies employee access to cloud and on-premises applications. We found the user portal intuitive and quick. It enabled us to access our corporate applications, peer-to-peer and VOIP communications, and remote desktops, removing the temptation to bypass security controls.
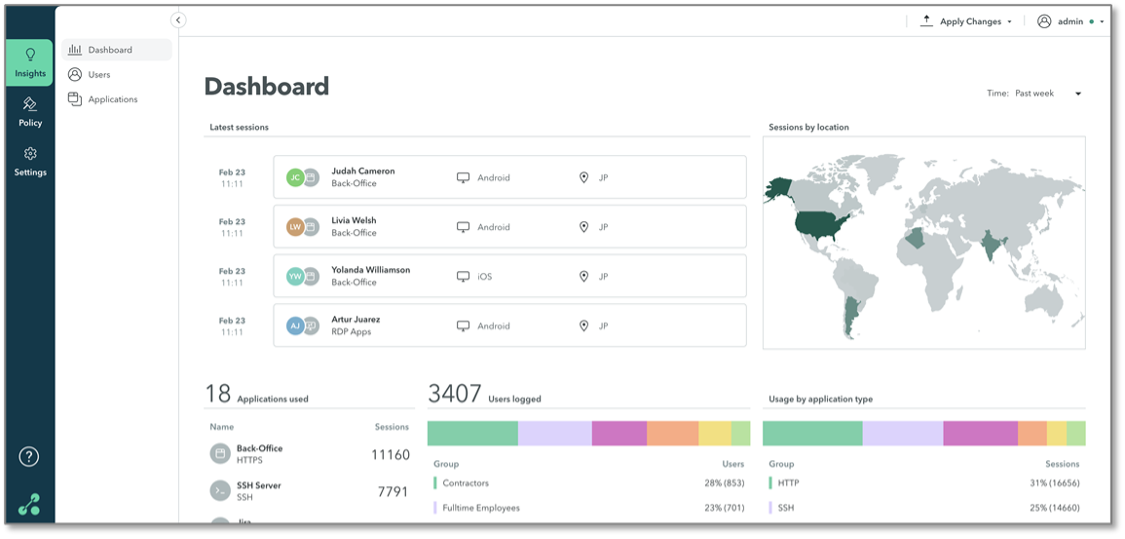
Next, ESG assumed an IT administrator role. We started by logging in to the administrative console and viewing the insights dashboard (Figure 5). The dashboard summarizes key secure session information and provides at-a-glance understanding of the usage of the system. All dashboard items are live links, enabling an administrator to drill down for more information on session locations, session details, and applications.
Figure 5. Axis Security Insights Dashboard
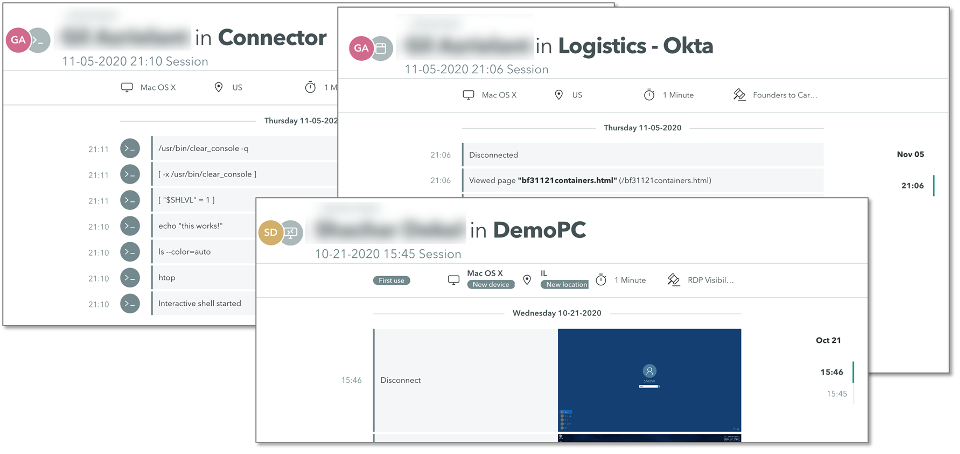
The Axis Security console enables administrators to pivot while searching and exploring data. We clicked on the first item in the Latest session list and then clicked on the username to get a list of the user’s sessions. We could also get to this same data from the Users menu item. We observed that by drilling down, we could see which pages the user viewed when accessing a web-based Logistics app (Figure 6). We could also see which commands the user executed during an SSH session. We also investigated the RDP session of the user and observed that Axis Security captured all activity, including screenshots, of the RDP session. Thus, Axis Security provided both zero-trust secure access and visibility into user activity.
Figure 6. User/Session Details
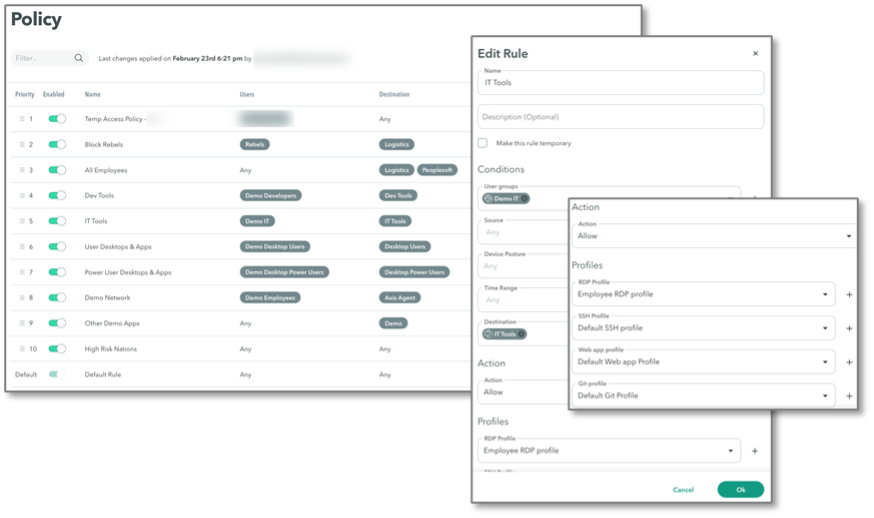
Next, ESG explored configuring access and security. We started with defining policies, as shown in Figure 7. Axis Security policies are similar to firewall rules but are more easily read and understood by humans: the policies control communication for an application from a source to a destination and can include parameters to specify users and groups, time ranges, and device posture. Axis Security can leverage Crowdstrike for additional device postures, and administrators can define profiles for types of applications (RDP, SSH, Web App, Git, etc.) to simplify rule creation and management. As with firewalls, rules are processed in order, and processing stops at the first rule match. Policies are enforced for every communication transaction, not just at the start of a session. Thus, if a policy parameter changes mid-session (for example, a time-of-day boundary is crossed), the policy is still enforced, and the communication may be stopped mid-session.
Figure 7. Axis Security Policy Definition
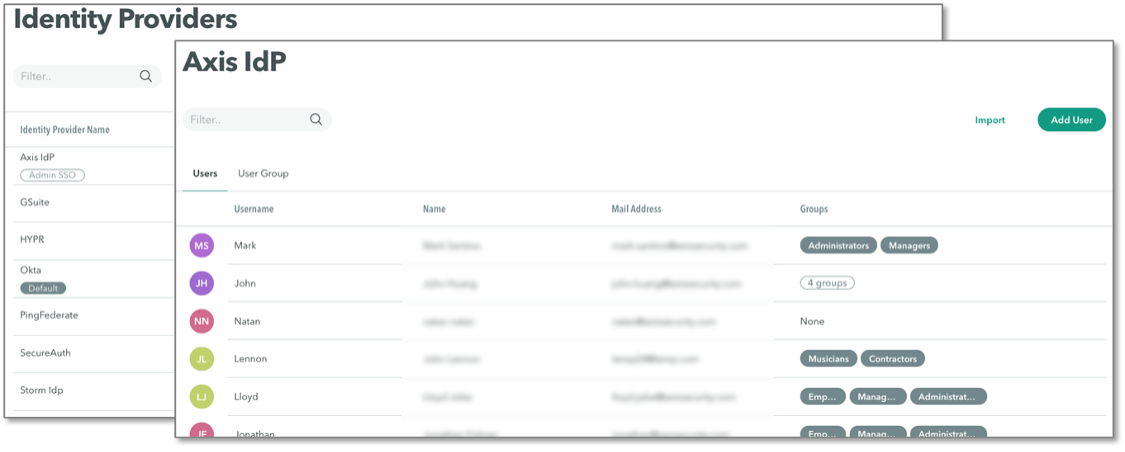
Axis Security includes its own identity provider to manage users and groups (Figure 8). The Axis IdP supports bulk import and temporary users with automatic deletion after a specified number of days. This feature is useful to enable secure access for contractors, hackathons, and other events. Administrators can also link to Google Gsuite, Okta, Microsoft, and other providers for identity and single-sign-on services for employees.
Figure 8. Users and Identities
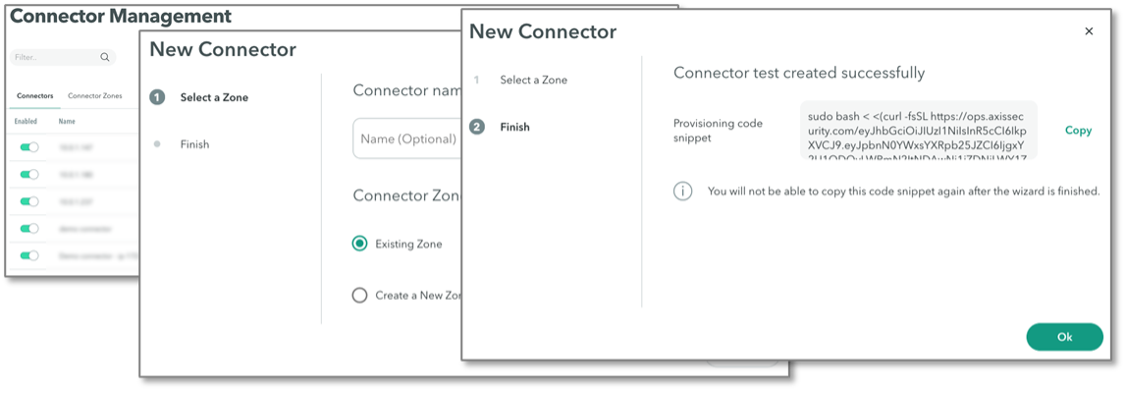
Axis Security never exposes applications, remote desktops, or SSH servers to the public internet. Instead, administrators install an Axis Security connector in each network segment. The connector makes an encrypted outbound connection to the Axis Application Access Cloud. Remote users also make a connection to the Axis Security cloud, and the Axis Security service connects the user to the application.
We used the Axis Security console to create a new connector. As part of the deployment process, the console created and displayed a bash script. We executed the script on a VM, and the connector was automatically downloaded, installed, and configured without requiring additional input. We noted that we could also install the connector via RPM or OVA. We were then able to use the connector to connect to multiple apps inside the zone from our remote location.
Figure 9. Deploying Axis Security Connectors
WHY THIS MATTERS
Why This Matters
Almost half (48%) of organizations report a problematic shortage of cybersecurity skills.4 These organizations need security tools that are effective and easy to use and that require little investment in training or time.
ESG validated that Axis Security simplifies deployment, requiring execution of a bash script for each network segment connector. We found that building policies was intuitive and enabled us to create logical policies at the application layer. We could quickly and easily create zero-trust-style secure access controls for the organization. The Axis Security dashboard provided a clear understanding of user activity, and we could drill down and pivot through the data to explore specific actions. Logging of each transaction (command line, page view, etc.) ensured we had a complete record for forensics or threat hunting.
The Bigger Truth
The pandemic forced enterprises to provide remote access to an unprecedented number of employees, partners, and suppliers, and ESG research shows that 44% of organizations prefer to keep as many employees as possible working remotely as long as possible even after the pandemic.5 This effort is challenging due to the threat landscape, implementation of policies and security controls, increased usage of personal devices for business purposes, and expanding use of the cloud. Organizations also report that the shortage of IT security resources and multiple security tools used for different threat vectors and use cases present additional obstacles to ensuring security at the edge. Thus, it’s not surprising that enterprises want to identify a secure access solution that replaces costly, labor-intensive traditional approaches like VPNs.
ESG conducted a technical review of Axis Security to evaluate its remote access capabilities, and our evaluation revealed that the solution simplifies employee access to cloud and on-premises applications. The user portal is intuitive and easy to use, enabling quick access to corporate applications, peer-to-peer and VOIP communications, and remote desktops. Using Axis Security removed the temptation to bypass security controls.
We also found that the solution is simple to deploy. Building security policies was intuitive. We could quickly and easily create zero-trust-style secure access controls for the organization and the dashboard enabled us to explore and understand user activity. Each individual transaction is inspected, authorized, and logged. This ensured we had a complete record of activity for forensics or threat hunting.
The results that are presented in this document are based on evaluation in a controlled environment. Due to the many variables in each organization’s infrastructure, it is important to perform planning and testing in your own environment to validate the viability and efficacy of any solution.
Axis Security is a single remote access solution suitable for all types of users, devices, applications, and locations. It frees enterprises of the “security tax” burden―expense, complexity, time, or latency―of adding security to solve a business problem. The zero-trust principles built into the platform deliver essential visibility, enable a granular approach to continuous authorization and provide access only to authorized resources. If your organization’s objective is to enable fast, simple, secure remote access, then ESG recommends that you evaluate Axis Security.
Secure Your Enterprise in Minutes
1 Source: ESG Master Survey Results, Transitioning Network Security Controls to the Cloud, Jul 2020.
2 Ibid.
3 Ibid.
4 Source: ESG Master Survey Results, 2021 Technology Spending Intentions Survey, Dec 2020.
5 Ibid.
This ESG Technical Review was commissioned by Axis Security and is distributed under license from ESG.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.
The goal of ESG Validation reports is to educate IT professionals about information technology solutions for companies of all types and sizes. ESG Validation reports are not meant to replace the evaluation process that should be conducted before making purchasing decisions, but rather to provide insight into these emerging technologies. Our objectives are to explore some of the more valuable features and functions of IT solutions, show how they can be used to solve real customer problems, and identify any areas needing improvement. The ESG Validation Team’s expert third- party perspective is based on our own hands-on testing as well as on interviews with customers who use these products in production environments.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.

