
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG SHOWCASE
The Need For Zero Trust Data Security
By Scott Sinclair, Senior Analyst; and Monya Keane, Senior Research Analyst
AUGUST 2021
Abstract
Overview
The Increasingly Diverse and Complex Data Security Landscape
41% of finance organizations identified the increasing or changing cybersecurity landscape and 42% identified new data security and privacy regulations as drivers of IT complexity at their organizations.
Ransomware
Figure 1. Frequency of Ransomware Attacks
Source: Enterprise Strategy Group
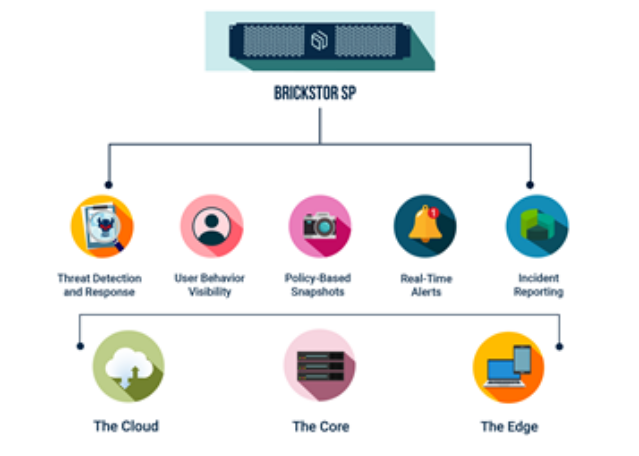
RackTop Systems—Zero Trust Data Security for Modern File Environments
- Automatically detects and stops insider threats and ransomware attacks on file data.
- Automatically maintains immutable copies of files for rapid file-level recovery.
- Instantly reports on what files were accessed.
- Automatically alerts security and infrastructure teams via email and webhooks with customized responses and automatic incident reporting.
- Delivers essential features to modernize existing production NAS storage.

Scott Sinclair, Senior Analyst, ESG
The Bigger Truth
Data Security Platform for Unstructured Data
This ESG Showcase was commissioned by RackTop Systems and is distributed under license from ESG.
1 Source: ESG Research Report, Data Storage Trends in an Increasingly Hybrid Cloud World, Mar 2020.
2 Source: ESG Research Report, 2021 Technology Spending Intentions Survey, Jan 2021.
3 ibid.
4 ibid.
5 Source: ESG Master Survey Results, 2021 Technology Spending Intentions Survey, Dec 2020.
6 ibid.
7 Source: ESG Research Report, Tape’s Place in an Increasingly Cloud-based IT Landscape, Dec 2020.
8 ibid.
All trademark names are property of their respective companies. Information contained in this publication has been obtained by sources The Enterprise Strategy Group (ESG) considers to be reliable but is not warranted by ESG. This publication may contain opinions of ESG, which are subject to change from time to time. This publication is copyrighted by The Enterprise Strategy Group, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of The Enterprise Strategy Group, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact ESG Client Relations at 508.482.0188.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
