
Brought to you by:
Enterprise Strategy Group | Getting to the Bigger Truth™
ESG TECHNICAL VALIDATION
Zero Trust Application Security With Truefort Fortress
Leveraging Behavioral Analytics to Secure On-premises and Cloud-native Applications
By Alex Arcilla, Senior Validation Analyst
MARCH 2022
Introduction
Figure 1. Top Cited Reasons for Increasing IT Complexity
What do you believe are the biggest reasons your organization’s IT environment has become more complex? (Percent of respondents, N=329, five responses accepted)
Source: ESG, a division of TechTarget, Inc.
TrueFort Platform
Figure 2. TrueFort Platform
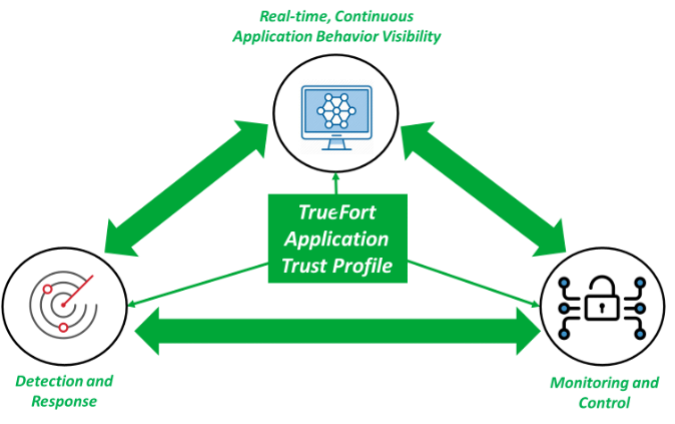
Source: ESG, a division of TechTarget, Inc.
ESG Technical Validation
Understanding Application Behavior
ESG Testing
Figure 3. How TrueFort Maps Applications and Related Granular Detail
Source: ESG, a division of TechTarget, Inc.
Figure 4. Displaying Connections in Tabular Format
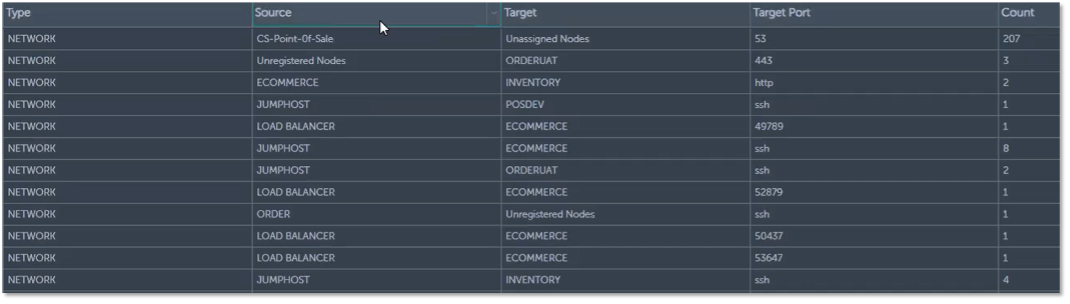
Source: ESG, a division of TechTarget, Inc.
Why This Matters
Establishing Security Controls
ESG Testing
Figure 5. Detecting Trusted and Untrusted Application Behavior
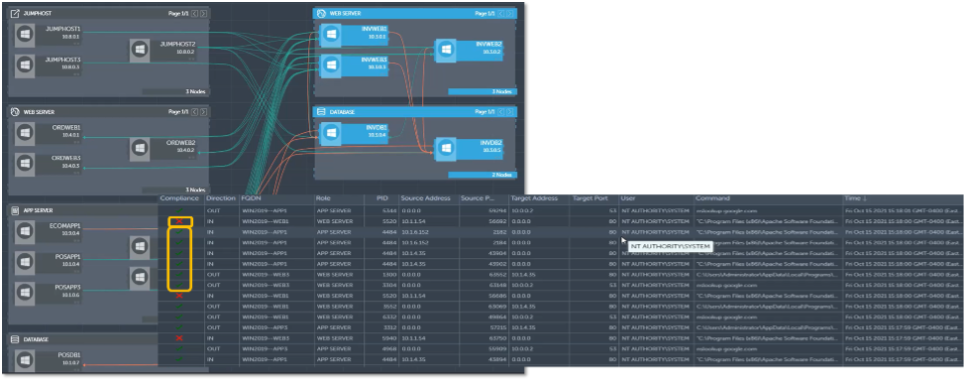
Source: ESG, a division of TechTarget, Inc.
Figure 6. Reviewing Application Behavior against CIS Benchmarks
Source: ESG, a division of TechTarget, Inc.
Figure 7. Detecting Drift with TrueFort’s FIM Capability
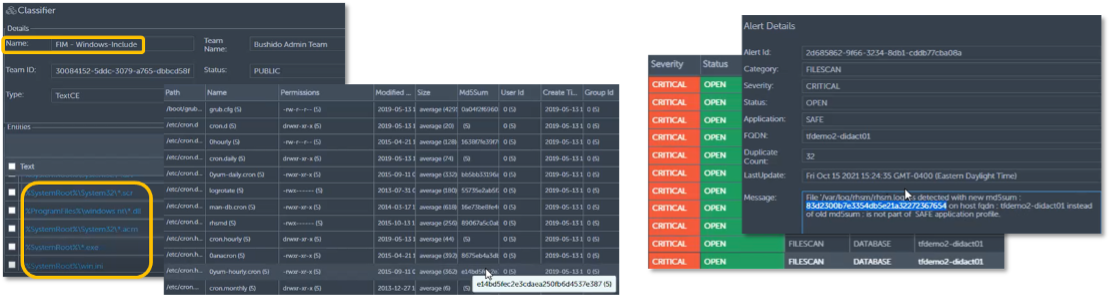
Source: ESG, a division of TechTarget, Inc.
Figure 8. Using Microsegmentation to Create Cybersecurity Policies
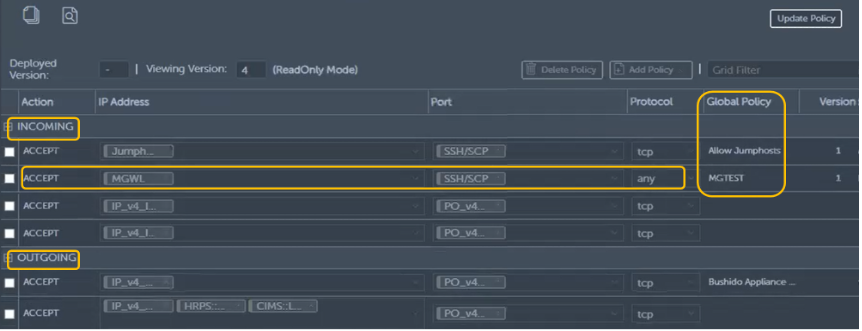
Source: ESG, a division of TechTarget, Inc.
Why This Matters
Decreasing Time to Detection and Response
ESG Testing
Figure 9. Rulebooks for Detecting Anomalous Behavior
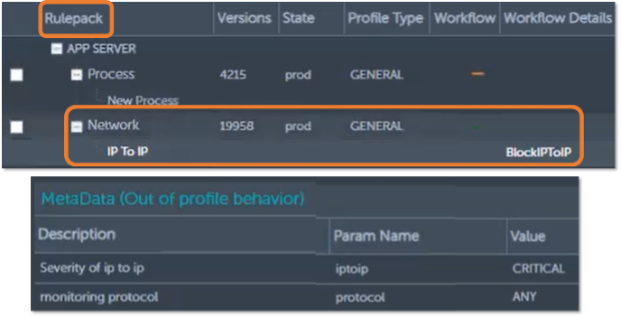
Source: ESG, a division of TechTarget, Inc.
Figure 10. Detecting and Analyzing Anomalous Application Behavior
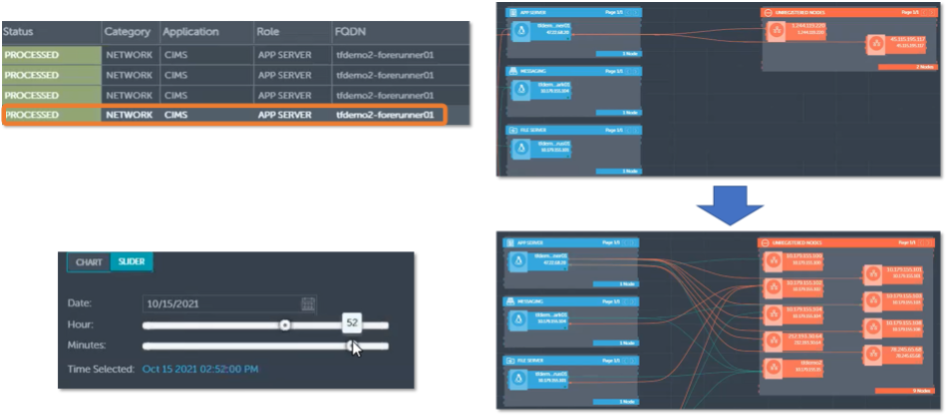
Source: ESG, a division of TechTarget, Inc.
Figure 11. Examining How Anomalous Behavior Occurred
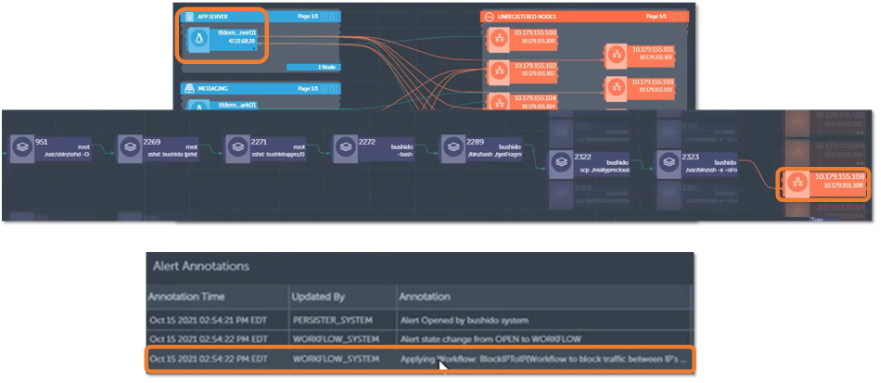
Source: ESG, a division of TechTarget, Inc.
Why This Matters
The Bigger Truth
- Establish a baseline of normal runtime application behavior without resorting to offline investigations and manual documentation of applications and the underlying architecture.
- Leverage the baseline to detect anomalous or untrusted application behavior via continuous monitoring.
- Implement targeted security alerts, policies, and controls that leverage the behavioral baseline to detect, understand, and respond to potential threats and attacks from entering and moving laterally through the organization.
This ESG Technical Validation was commissioned by TrueFort and is distributed under license from TechTarget, Inc.
All product names, logos, brands, and trademarks are the property of their respective owners. Information contained in this publication has been obtained by sources TechTarget, Inc. considers to be reliable but is not warranted by TechTarget, Inc. This publication may contain opinions of TechTarget, Inc., which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget, Inc.’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget, Inc. makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
This publication is copyrighted by TechTarget, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.

Enterprise Strategy Group | Getting to the Bigger Truth™
Enterprise Strategy Group is an IT analyst, research, validation, and strategy firm that provides market intelligence and actionable insight to the global IT community.
