
ESG RESEARCH INSIGHTS REPORT
The XDR Payoff: Better Security Posture
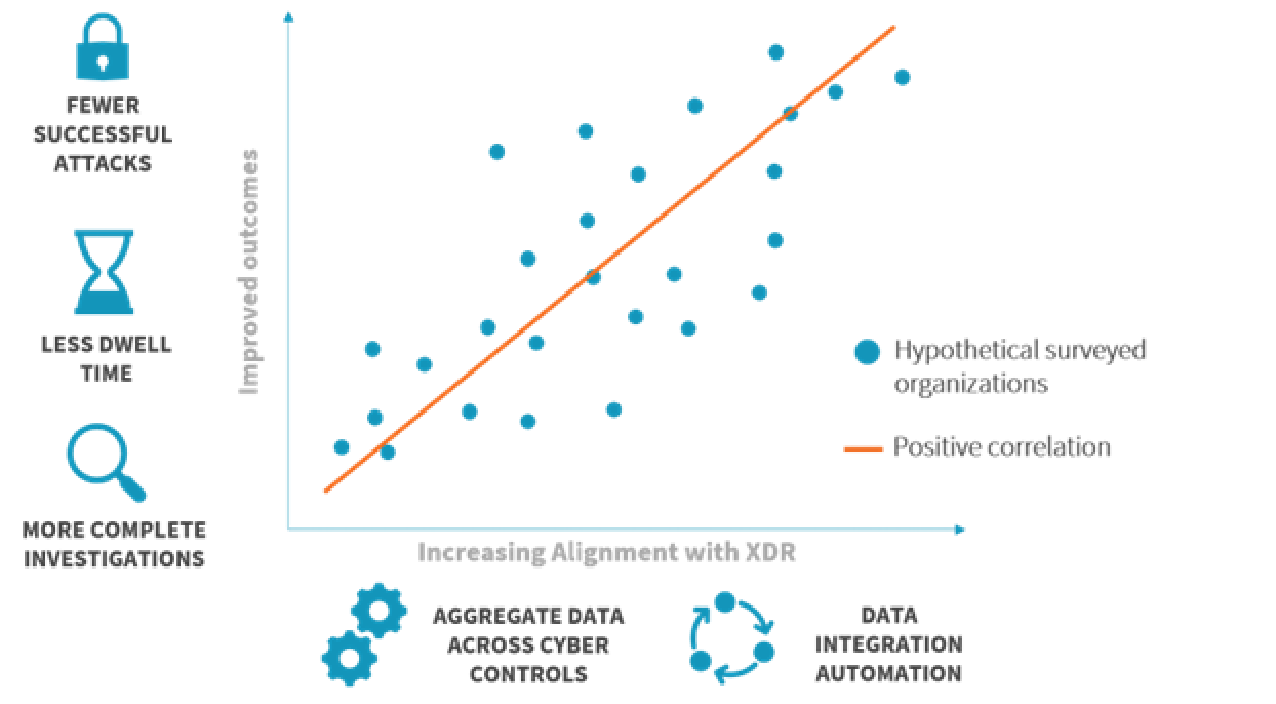
Organizations that employ strategies aligned with XDR experience fewer successful attacks, have a better overall security posture, and live with less daily stress on their teams.
By Dave Gruber, Principal Analyst
Adam DeMattia, Director of Research
JANUARY 2023
Executive Summary
Security organizations that have already invested in aggregation, correlation, and analysis of signals across multiple security controls experience fewer successful attacks, have a better overall security posture, and live with less daily stress on their teams.
Current Situation
Current Situation
- The attack surface in most organizations is rapidly expanding, and current tools are failing to support it, while introducing more vulnerabilities to manage.
- The threat landscape continues to become more sophisticated, as adversaries leverage advanced attack strategies to evade security controls.
- Continued investment in cloud applications and services challenges existing tools to keep up, while many organizations lack the people and skills needed to secure cloud resources.
- The move to cloud, together with ongoing defense-in-depth security strategies, is producing massive amounts of alerts, telemetry, and noise, making it challenging for security teams to triage and prioritize where to focus.
- Reactive, firefighting activities are consuming security resources, leaving no time to improve security programs.
Introducing XDR
Figure 1. Multiple Definitions of XDR Add Confusion
How EDR Investments Have Influenced the Road to XDR
But Isn’t That What a SIEM Is All About?
Understanding the Value of XDR
- Consolidation of disparate tools into a common threat detection and response architecture.
- More effective alert and event correlation. Less specialized skills needed to perform security operations tasks.
- Prioritization of alerts based on risk.
- Reinforce security controls and prevent future similar attacks.
- More efficient threat/forensic investigations.
Figure 2. Top 7 XDR Use Case Priorities
Organizations Aligning with XDR Approaches Report Better Overall Security Posture
Figure 3. ESG’s XDR Value Assessment Model
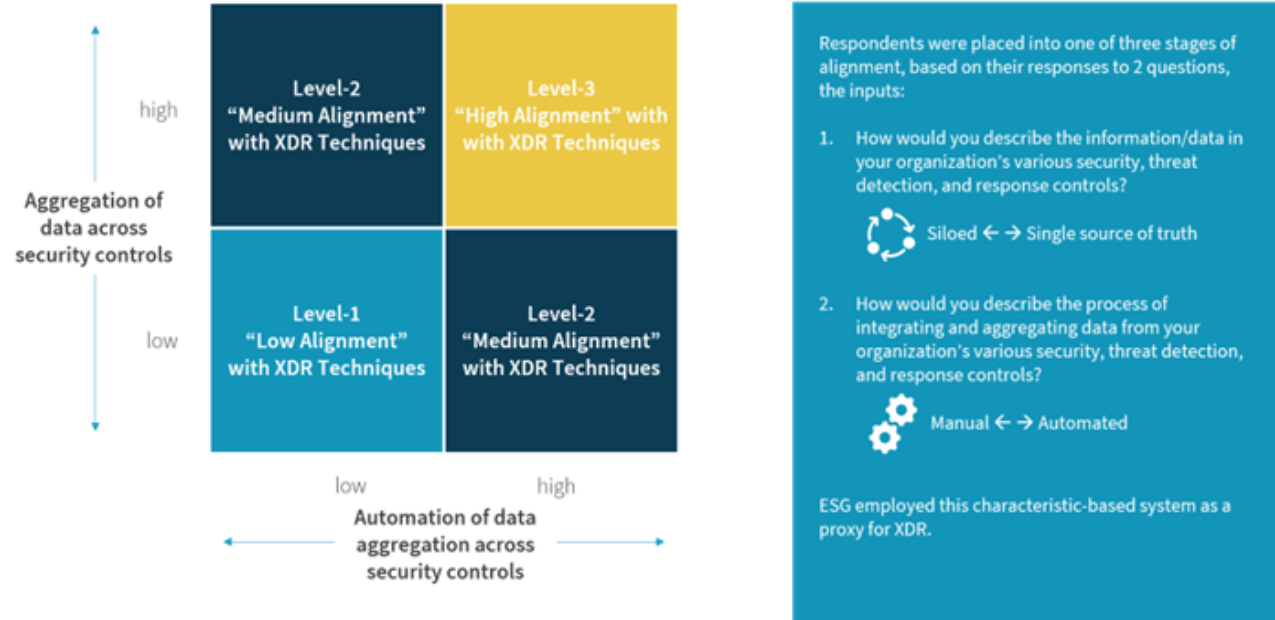
Figure 4. XDR Alignment Maturity Model Distribution
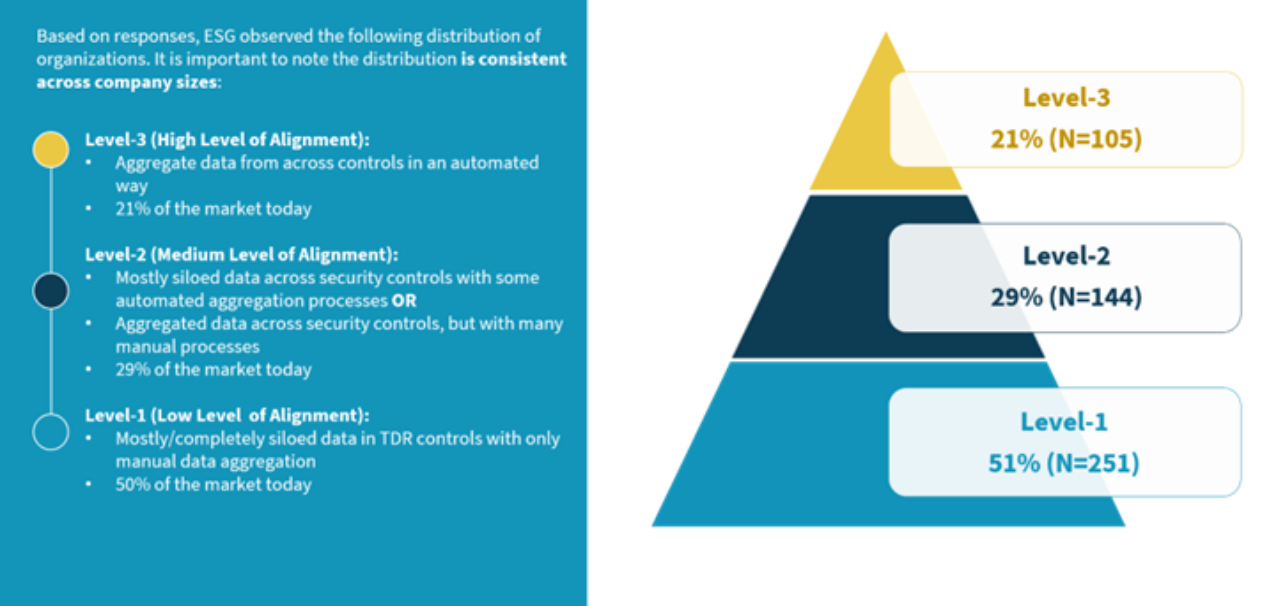
Figure 5. ESG’s XDR Alignment Maturity Hypothesis Visualized
Level-3 Organizations Experienced Half as Many Successful Attacks
Figure 6. Higher Alignment Means More Confidence in the TDR Function
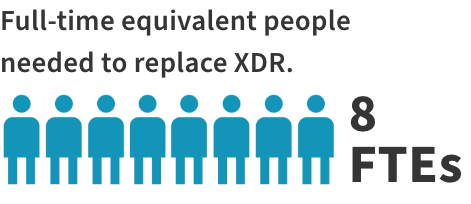
When asked how many FTEs it would take to replace their automated systems, organizations reported an average of 8 FTEs
Figure 7. Those in Alignment Struggle Less with Operational Challenges
Figure 8. Organizations in Higher Alignment Are More Likely to Achieve Greater Improvements
Better Correlation = Better Results
Figure 9. Threat Data Correlation Effectiveness, by Alignment Level
Figure 10. Threat Data Correlation Effectiveness, All Respondents
Figure 11. Threat Detection/Response Personnel Workload, by Level of Alignment
Figure 12. Impact of Global Cybersecurity Skills Shortage, by Level of Alignment
Siloed Data for Most
Figure 13. Most Security, Threat Detection, and Response Control Information Is Fragmented
Figure 14. Integration and Aggregation Process for Security, Threat Detection, and Response Controls Data
Figure 15. Operational Improvements Achieved from Effective Threat Data Correlation
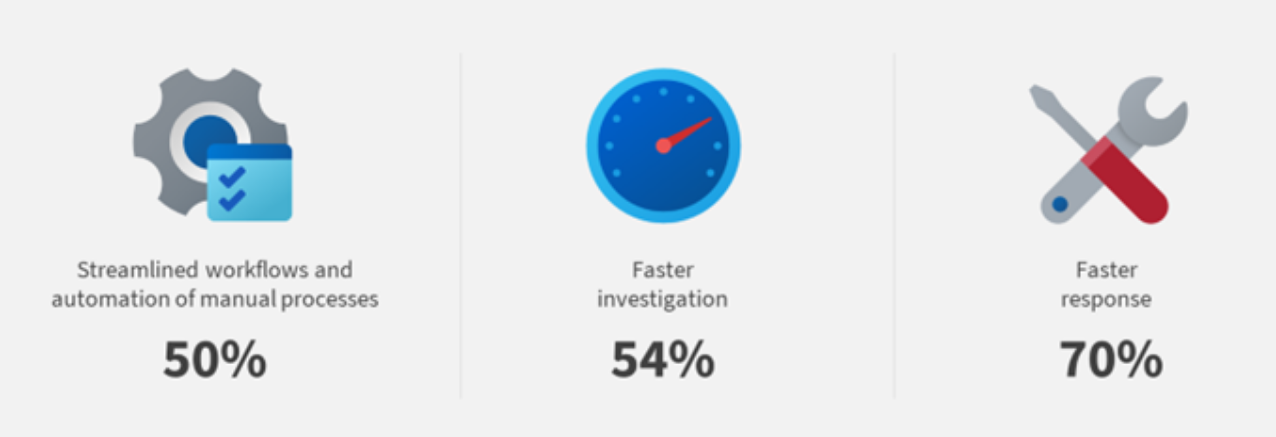
Level-3 Organizations Ignore Significantly Fewer Alerts
This statistic leads to the significant difference we see in the number of breaches experienced by Level-1 and Level-2 organizations. Again, XDR solutions offer a new path for less mature security teams to make a significant impact on the reduction of successful attacks without hiring specialized resources.
Figure 16. Security Events/Alerts Ignored by Organizations
Figure 17. Typical/Average Dwell Time Prior to Data Breach Detection

Figure 18. Average Number of Data Breaches and Attacks
Why Can’t My SIEM Solve the Problem?
Figure 19. Organizations’ Satisfaction with Upfront Correlation of SIEMs
Figure 20. Organizations’ Views on the Amount of Data Ingested into Their SIEMs
Figure 21. Organizations Plan Continued Investment
MITRE ATT&CK Offers Broad Benefits Across Security Operations
Figure 22. Top 5 MITRE ATT&CK Use Cases
The Bigger Truth
Methodology and Demographics
To gather data for this report, Enterprise Strategy Group conducted a comprehensive survey of security and IT professionals responsible for their organization’s detection and response strategies, processes, and technologies. All respondents were based in North America (US and Canada) and employed at organizations with 500 or more employees. The survey was filed between June 15, 2020, and June 30, 2020. All respondents were given an incentive to complete the survey in cash awards and/or cash equivalents.
After applying data quality control best practices and screening the remaining completed responses (on several criteria) for data integrity, a final sample of 500 respondents remained. Figure 23 - Figure 25 detail the demographics and firmographics of the respondent base. Note: Totals in figures and tables throughout this report may not add up to 100% due to rounding.
Figure 23. Respondents’ Current Responsibility
Figure 24. Company Size (Number of Employees)
Figure 25. Respondents’ Primary Industries
This Enterprise Strategy Group Research Insights Report was commissioned by Trend Micro and is distributed under license from TechTarget, Inc.
All product names, logos, brands, and trademarks are the property of their respective owners. Information contained in this publication has been obtained by sources TechTarget, Inc. considers to be reliable but is not warranted by TechTarget, Inc. This publication may contain opinions of TechTarget, Inc., which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget, Inc.’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget, Inc. makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
This publication is copyrighted by TechTarget, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.

About Enterprise Strategy Group
Enterprise Strategy Group is an integrated technology analysis, research, and strategy firm that provides market intelligence, actionable insight, and go-to-market content services to the global IT community.