Legacy Cybersecurity Training Strategies Are Failing, Leading to a Lack of Resilience
A New, Evidence-based Approach Is Needed
FEBRUARY 2023
Legacy cybersecurity training strategies are failing to prepare the individuals and teams they operate within for modern, advanced threats.
Legacy Technical Training Strategies Are Flawed
The pace of change within modern cyberattacks requires a transformation in the way we think about training—moving from a scheduled, online, or classroom-style approach to a continuous, real-world learning environment.Technical Security Training and Certifications
End-user Security Awareness Training
Can Security Leaders Confidently Prove Workforce Readiness?

Organizational Readiness Measurements Are Lacking
As impactful as a serious cyberattack can be on overall business operations, few C-level execs or BoD members have an ability to effectively measure their organization’s readiness.
A Path to Effective Cyber Resilience
A Systematic Methodology Is Needed
People-centric Cybersecurity Must Be Continuous and Measurable
CISOs need to ensure they have the coverage and required acumen across their entire organization. Business and technical leaders need to have confidence in their preparedness across the AppDev, security, IT/cloud operations, legal, communications, and executive teams.
A Cyber Workforce Resilience Methodology
Figure 1. The Cyber Workforce Resilience Methodology
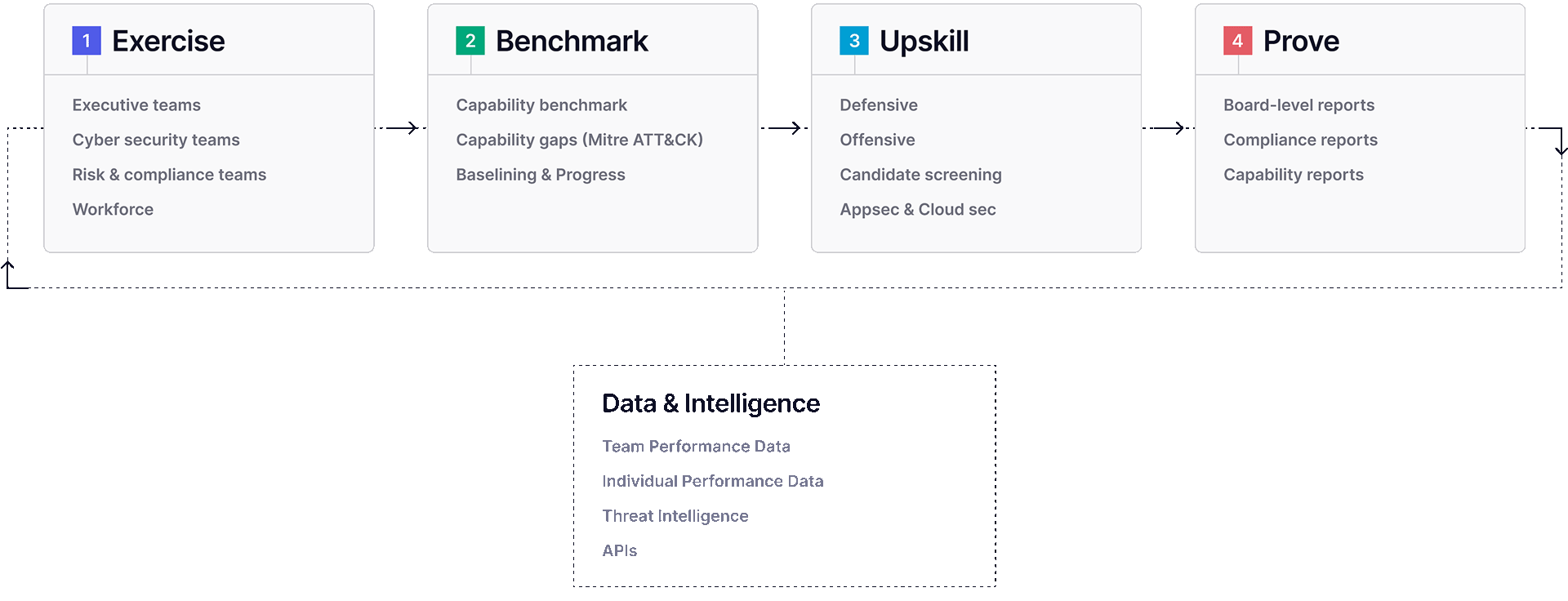
Real-life Exercises
Using highly interactive, realistic simulations and hands-on cybersecurity labs based on real-world scenarios helps evaluate individual and team capabilities and decision making against the latest threats.
Figure 2. Expanding the Model
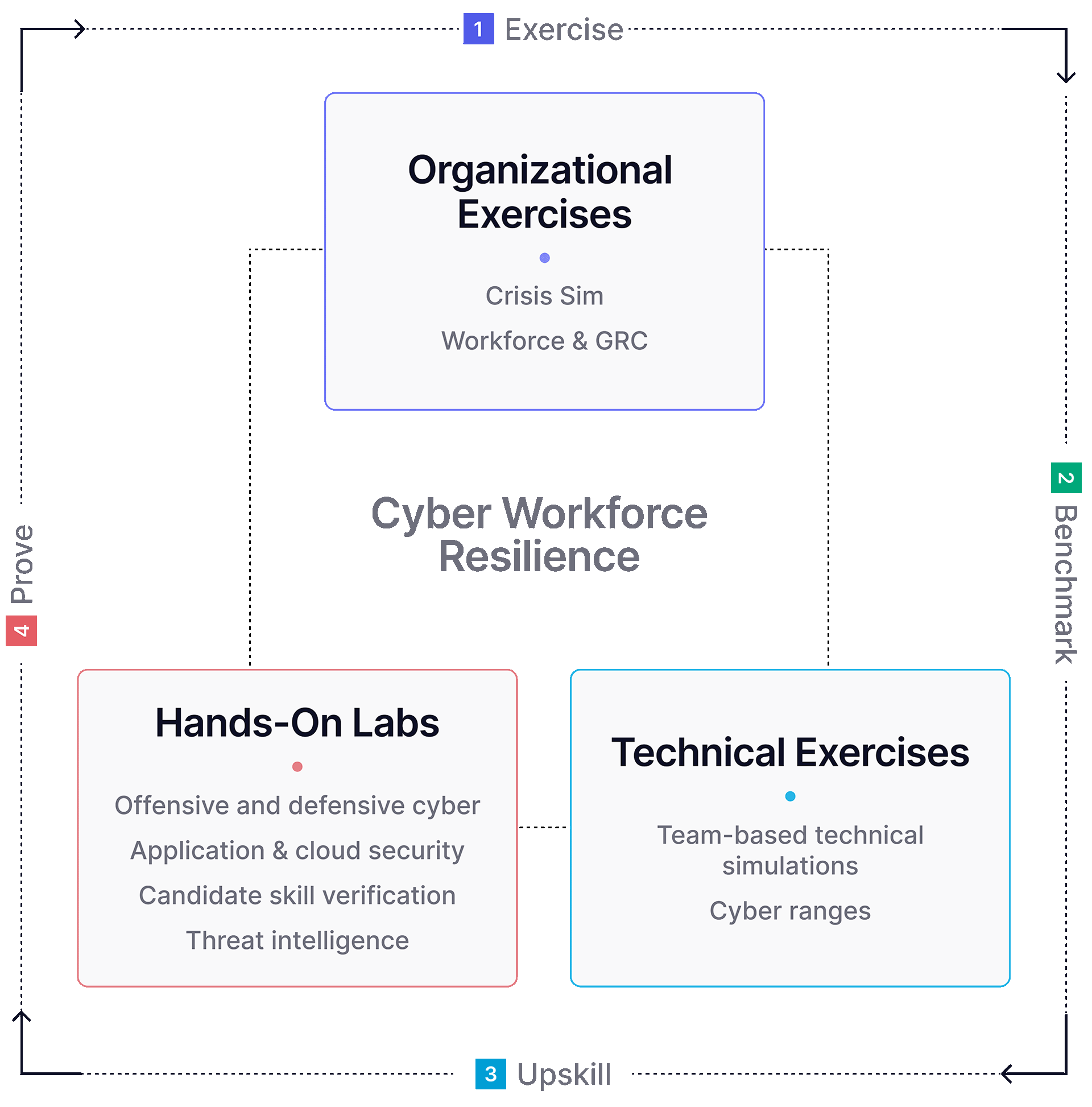
Benchmarks Enable Program Growth
Up-skilling Individuals and Teams
Enabling Retention and Rewards Based on Capabilities, Not Tenure
Continuous assessments help security leaders understand where skills are strong—and weak—within each team and adjust the delivery of instant targeted training to address any weaknesses, allowing them to enable retention and rewards based on capability—not tenure.
Proving Results
Further, benchmarking can help leaders understand and report on where they stack up against other organizations in similar industries.
Automating Resilience Delivers Positive Outcomes
Introducing Immersive Labs
The Bigger Truth
All product names, logos, brands, and trademarks are the property of their respective owners. Information contained in this publication has been obtained by sources TechTarget, Inc. considers to be reliable but is not warranted by TechTarget, Inc. This publication may contain opinions of TechTarget, Inc., which are subject to change. This publication may include forecasts, projections, and other predictive statements that represent TechTarget, Inc.’s assumptions and expectations in light of currently available information. These forecasts are based on industry trends and involve variables and uncertainties. Consequently, TechTarget, Inc. makes no warranty as to the accuracy of specific forecasts, projections or predictive statements contained herein.
This publication is copyrighted by TechTarget, Inc. Any reproduction or redistribution of this publication, in whole or in part, whether in hard-copy format, electronically, or otherwise to persons not authorized to receive it, without the express consent of TechTarget, Inc., is in violation of U.S. copyright law and will be subject to an action for civil damages and, if applicable, criminal prosecution. Should you have any questions, please contact Client Relations at cr@esg-global.com.

